An unknown superior persistent risk (APT) group has been linked to a sequence of spear-phishing assaults concentrating on Russian authorities entities because the onset of the Russo-Ukrainian battle in late February 2022.
“The campaigns […] are designed to implant a Distant Entry Trojan (RAT) that can be utilized to surveil the computer systems it infects, and run instructions on them remotely,” Malwarebytes stated in a technical report printed Tuesday.
The cybersecurity firm attributed the assaults with low confidence to a Chinese language hacking group, citing infrastructure overlaps between the RAT and Sakula Rat malware utilized by a risk actor often known as Deep Panda.
The assault chains, whereas leveraging completely different lures over the course of two months, all employed the identical malware barring small variations within the supply code.
The marketing campaign is alleged to have commenced round February 26, days after Russia’s army invasion of Ukraine, with the emails distributing the RAT below the guise of an interactive map of Ukraine (“interactive_map_UA.exe”).
The event as soon as once more demonstrates risk actors’ capabilities to adapt and regulate their assaults to world occasions, utilizing probably the most related and up-to-date lures to maximise their possibilities of success.
A second early March assault wave primarily focused the state-controlled RT TV and concerned the usage of a rogue software program repair for the Log4Shell vulnerability that made headlines in late 2021.
Apart from together with the patch within the type of a compressed TAR file, the e-mail message additionally got here with a PDF doc with directions to put in the patch and listed one of the best safety practices to observe, together with enabling two-factor authentication, utilizing Kaspersky antivirus, and refraining from opening or replying to suspicious emails.
In an extra try to spice up the authenticity of the e-mail, the doc additionally contained a VirusTotal URL pointing to an unrelated file to present the impression that the Log4j patch file just isn’t malicious.
What’s extra, the e-mail featured hyperlinks to an attacker-controlled area “rostec[.]digital” together with fraudulent profiles created on Fb and Instagram alluding to the Russian protection conglomerate.
“Curiously, the risk actor created the Fb web page in June 2021, 9 months earlier than it was used on this marketing campaign,” the researchers stated. “This was in all probability an try to draw followers, to make the web page look extra respectable, and it suggests the APT group had been planning this marketing campaign lengthy earlier than the invasion of Ukraine.”
The third iteration of the assault that adopted made use of one other malicious executable file — this time “build_rosteh4.exe” — in an try to go off the malware as if it is from Rostec.
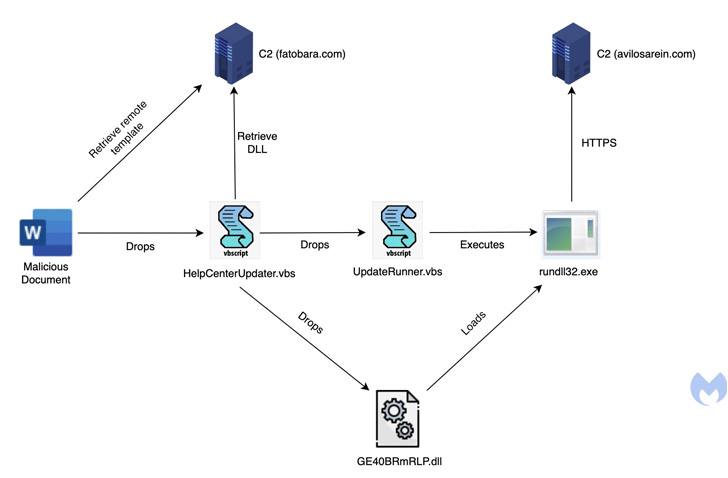
Lastly, in mid-April 2022, the attackers pivoted to a job-themed phishing bait for Saudi Aramco, a Saudi Arabian petroleum and pure gasoline firm, the weaponized Microsoft Phrase doc appearing as a set off for an an infection sequence to deploy the RAT.
The DLL payload employs a wide range of superior tips to thwart evaluation, together with management movement flattening and string obfuscation, whereas additionally incorporating options that enable it to arbitrary recordsdata despatched from a distant server to the contaminated host and execute command-line directions.
The findings intently observe findings from Examine Level {that a} Chinese language adversarial collective with connections to Stone Panda and Mustang Panda focused no less than two analysis institutes situated in Russia with a beforehand undocumented backdoor referred to as Spinner.