Welcome again, my cyber warriors!
Because the struggle in Ukraine rages on, it is necessary to remember that this struggle did not start in February of this 12 months, however relatively it has been simmering for nearly a decade. Ever for the reason that individuals of Ukraine overthrew their despotic Russian puppet in 2014, the Russians have been incessantly attacking the Ukrainian individuals and their establishments. Earlier than we check out the Russian cyber assaults in opposition to Ukraine, let’s take a quick second to have a look at the latest historical past of Ukraine.
It is all the time a troublesome job to summarize 100 years of historical past in just a few paragraphs, however right here goes my feeble try. Please bear with me and forgive my omissions within the curiosity of brevity.
The Final 100 Years of Ukrainian Historical past in a Nutshell
In 1922, Ukraine was a one of many founding republics of the Soviet Union (the Soviet Union grew out of the Russian Revolution of 1917). It suffered genocide below Stalin and misplaced 6-8 million individuals from a mass hunger engineered by the Soviet state. When Nikita Khrushchev grew to become head of the Soviet Communist get together in 1954, he appeared favorably upon Ukraine and the Ukrainian individuals as he had been the top of the Ukrainian Communist Celebration. He transferred elements of conventional Russia to the Ukraine republic. This included the Crimean Peninsula (Crimea was captured by the Catherine the Nice in 1781 from the Turks). This expanded the Ukraine republic and Crimea remained a part of the Soviet Union till it is disintegration in 1991. When the Soviet Union disintegrated, Ukraine then suffered a decade of financial deprivation with the financial system shrinking by over 10% per 12 months.
From 1994-2004, Leonid Kuchma was the President of Ukraine. His presidency was marked by corruption and scandals. Because of this, he selected to not run once more and two main candidates battled it out for the presidency, Victor Yanukovych and Viktor Yushchenko (for these of us within the west, these two names are so related that it’s troublesome to maintain them straight). The previous, Yanukovych, was intently linked to Putin, whereas the latter, Yushchenko, wished to convey Ukraine nearer to the West. On the threat of oversimplification, I’ll confer with them because the Russian-linked, Yanukovych, and the Western-linked Yushchenko.The Russian-linked candidate, Yanukovych, gained an in depth election however the opposition and goal election observers claimed fraud and irregularities within the election. This led to the Orange Revolution which befell from November 2004 to January 2005. The Orange Revolution was a sequence of protests and political occasions that challenged the rigged election of Yanukovych.
Ultimately, the Supreme Court docket of Ukraine dominated the election null and void in February 2005. After one other runoff election, Western-linked, Yushchenko, grew to become president.
When the subsequent election befell in 2010, the main candidates for the presidency have been Yushchenko ,Yanukovych and Yulia Tymoshenko. Yushkenko and Tymoshenko have been allies in the course of the Orange Revolution however the two grew to become bitter rivals in the course of the 2010 election.
In an election marked by widespread corruption and fraud, Russian-linked, Victor Yanocovych, was elected prime minister. Yanocovych had shut ties to Putin and the Kremlin and was reputed to be the favourite of Putin (his Ukraine election marketing campaign supervisor, Paul Manafort, was Trump’s 2016 Presidential election marketing campaign supervisor. Coincidence?). As he imprisoned his rival, Yulia Timoshenko, and moved to restrict freedoms and draw Ukraine nearer to Russia, the Ukrainian individuals revolted and he was impeached by parliament in 2014. Yanocovych fled Ukraine to Russia the place he nonetheless resides below the safety of Putin. Quickly thereafter, Russia invaded Ukraine and took management of Crimea and Donbas. Then, the cyber assaults start.
In February 2019, Ukraine amended its structure in ways in which would ease it is integration into Europe. In April 2019, a former comic/actor of Jewish descent, Volodymyr Zelenskyy, was overwhelmingly elected president of Ukraine with 73% of the vote. Zelenskyy continued the motion of Ukraine away from Russia and additional integration into the remainder of Europe.
On February 24, 2022, Russia invades Ukraine.
Main Russian Cyber Assaults in opposition to Ukraine in Current Years
To offer you some perspective on the cyber struggle component, listed below are the key occasions within the final 10 years. There have been so many Russian assaults in opposition to Ukraine in recent times it’s troublesome to trim this checklist to only few. A lot of the most severe assaults have taken place after the mass protests in 2013-2014 that led to the ouster of Yanocovych.
ATM’s Attacked with Ploutus
In February 2014, ATM’s belonging to one of many largest Ukrainian banks have been hacked. The ATM’s had been loaded with money on Friday and have been empty by Monday. Gangs employed by Russia and its separatists in Ukraine, merely emptied the money. Reportedly, the malware Ploutus was used within the assault. Ploutus is able to deactivating and bypassing conventional antivirus programs.
BlackEnergy3
The BlackEnergy3 assault was a complicated assault in opposition to the Ukrainian electrical energy grid. Blackenergy3 was really reconstituted malware that had beforehand been used for DDoS assaults. The malware relied upon social engineering to enter the company community of the electrical utility (it used an e mail tackle that appeared to return from a Ukrainian authorities official) benefiting from a MS Phrase vulnerability (MS-2014-4144). The attackers (Sandworm, a hacker group throughout the Russian GRU)) then used mimikatz to collect credentials that have been used to compromise the Human Machine Interface (HMI) into the SCADA community. They then disconnected 30 substation breakers that created the blackout. For extra on BlackEnergy3,click on right here.
CrashOveride (aka Industroyer)
CrashOveride was the primary malware particularly designed to assault electrical grids (BlackEnergy3 was initially a DDoS instrument and morphed into social engineering instrument to realize entry to the Human Machine Interface (HMI) of {the electrical} grid). It was used in opposition to Ukraine within the December 17, 2016 transmission substation assault.
SCADA/ICS programs use a large number of protocols and virtually no two programs are alike, making assaults much more difficult. There may be, however, a unifying protocol meant to translate the a number of protocols, often called OPC. CrashOveride used OPC to speak to the varied modules within the electrical substation.
CrashOveride prompted the open breakers on distant terminal models (RTU) to enter an infinite loop. This causes the circuit breakers to stay open even when the operators tried to close them down.
Petya and NotPetya
Petya was a ransomware assault propogated by e mail attachments in 2016. In 2017, after the discharge of the NSA’s EternalBlue by the ShadowBrokers, this malware was repurposed utilizing EternalBlue to realize entry to the working system. Researchers named the brand new ransomware, NotPetya, to differentiate it from Petya. This assault was targeted on Ukraine however shortly unfold all through the world inflicting billions of {dollars} of harm to programs. Many have known as it the costliest malware in historical past. NotPetya is a case research in how malware focused to at least one nation or sector, can wreak havoc worldwide. The NSA must also be held responsible– in part–for this destruction.
NotPetya portrayed itself as ransomware however even after the victims paid the ransom their information have been nonetheless unrecoverable. The Russian GRU hacking group often called Sandworm is the probably wrongdoer.
Paralysis of Treasury Division of Ukraine
Like most state owned treasuries, the Ukrainian Treasury makes periodic funds to each people and companies. On December 6, 2016, Ukraine’s Treasury, Ministry of Finance, and pension fund have been knocked offline for 2 days, delaying funds to a wide range of entities. It seems that this was coordinated DDoS assault in opposition to these authorities departments.
Airtight Wiper
Simply because the struggle started in February 2022, quite a lot of organizations in Ukraine have been hit with an assault often called Airtight Wiper. This can be a refined piece of malware that deletes and corrupts information together with fragmenting the information making it very troublesome to reconstruct in a restoration. It was primarily focused to the monetary, agriculture, emergency response, and vitality sector.
Industroyer and CaddyWiper
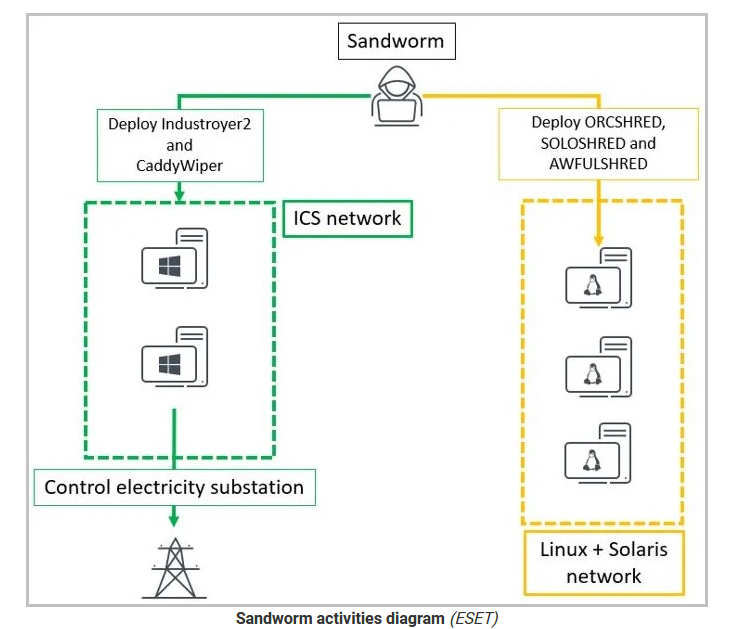
The Russian state-sponsored hacking group often called Sandworm, tried as soon as once more to takedown the Ukrainian electrical grid on April 12,2022. This assault tried to take down a big Ukrainian vitality supplier by disconnecting its electrical substations with a brand new variant of the Industroyer2 malware for industrial management programs (ICS) and a brand new model of the CaddyWiper information destruction malware.
The risk actor used a model of the Industroyer ICS malware personalized for the goal high-voltage electrical substations after which tried to erase the traces of the assault by executing CaddyWiper and different data-wiping malware households tracked as Orcshred, Soloshred, and Awfulshred for Linux and Solaris programs.

Abstract
The Ukrainian individuals have rejected the tyrannical insurance policies of Putin and his puppets and are paying a heavy value. Ever since Ukraine rejected the Putin puppet as their prime minister, Russia has been hammering their financial system and establishments continuous. This should cease. Sadly, Putin solely respects energy. That’s the reason we should act.