An unofficial safety patch has been made obtainable for a brand new Home windows zero-day vulnerability within the Microsoft Help Diagnostic Instrument (MSDT), even because the Follina flaw continues to be exploited within the wild.
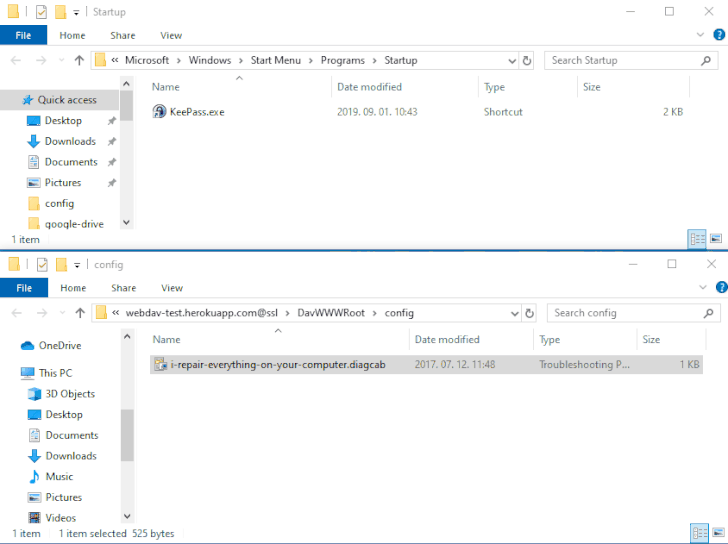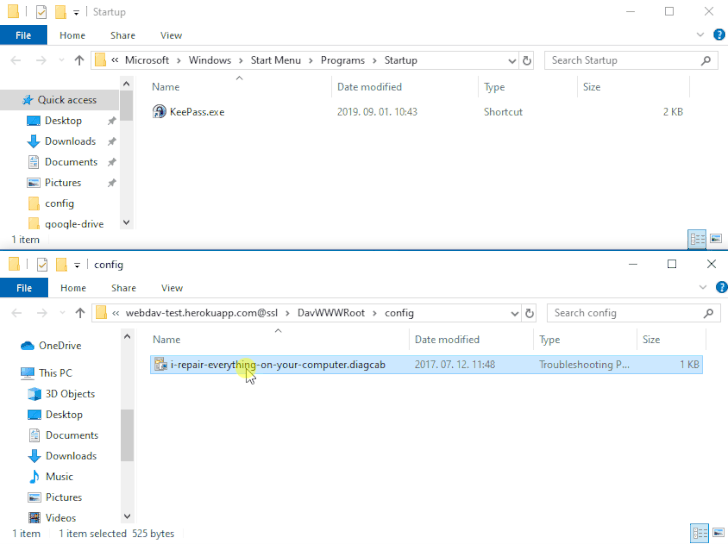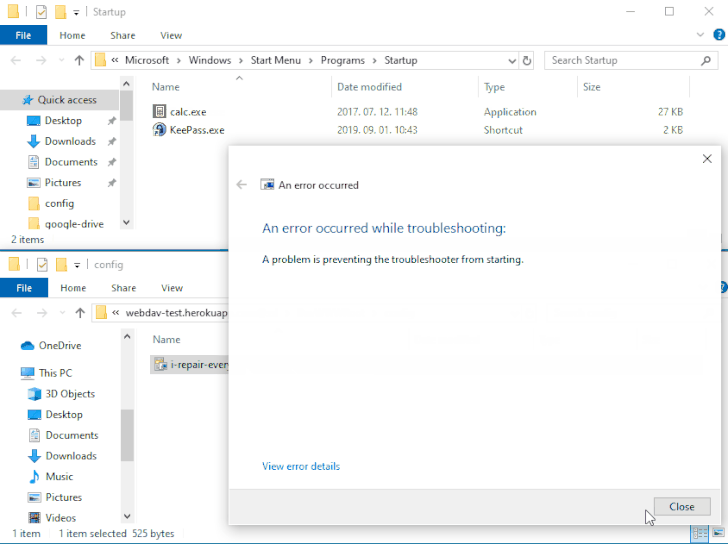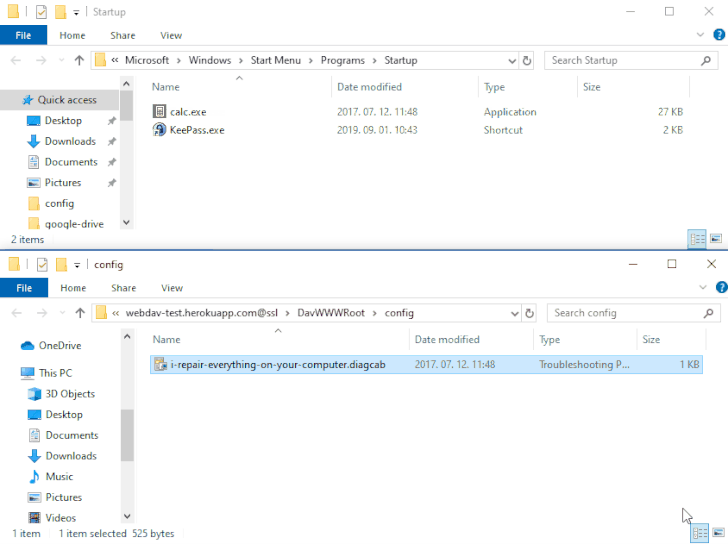
The problem — referenced as DogWalk — pertains to a path traversal flaw that may be exploited to stash a malicious executable file to the Home windows Startup folder when a possible goal opens a specifically crafted “.diagcab” archive file that accommodates a diagnostics configuration file.
The concept is that the payload would get executed the following time the sufferer logs in to the system after a restart. The vulnerability impacts all Home windows variations, ranging from Home windows 7 and Server Server 2008 to the newest releases.
DogWalk was initially disclosed by safety researcher Imre Rad in January 2020 after Microsoft, having acknowledged the issue, deemed it as not a safety problem.
“There are a selection of file sorts that may execute code in such a approach however aren’t technically ‘executables,'” the tech big mentioned on the time. “And various these are thought of unsafe for customers to obtain/obtain in electronic mail, even ‘.diagcab’ is blocked by default in Outlook on the internet and different locations.”
Whereas all information downloaded and acquired by way of electronic mail embody a Mark-of-the-Net (MOTW) tag that is used to find out their origin and set off an acceptable safety response, 0patch’s Mitja Kolsek famous that the MSDT utility is just not designed to test this flag and therefore permits the .diagcab file to be opened with out warning.
“Outlook is just not the one supply car: such file is cheerfully downloaded by all main browsers together with Microsoft Edge by merely visiting(!) a web site, and it solely takes a single click on (or mis-click) within the browser’s downloads checklist to have it opened,” Kolsek mentioned.
“No warning is proven within the course of, in distinction to downloading and opening some other identified file able to executing [the] attacker’s code.”
The patches and the renewed curiosity within the zero-day bug comply with lively exploitation of the “Follina” distant code execution vulnerability by leveraging malware-laced Phrase paperwork that abuse the “ms-msdt:” protocol URI scheme.
Based on enterprise safety agency Proofpoint, the flaw (CVE-2022-30190, CVSS rating: 7.8) is being weaponized by a risk actor tracked as TA570 to ship the QBot (aka Qakbot) information-stealing trojan.
“Actor makes use of thread hijacked messages with HTML attachments which, if opened, drop a ZIP archive,” the corporate mentioned in a sequence of tweets detailing the phishing assaults.
“Archive accommodates an IMG with a Phrase doc, shortcut file, and DLL. The LNK will execute the DLL to start out QBot. The doc will load and execute a HTML file containing PowerShell abusing CVE-2022-30190 used to obtain and execute Qbot.”
QBot has additionally been employed by preliminary entry brokers to achieve preliminary entry to focus on networks, enabling ransomware associates to abuse the foothold to deploy file-encrypting malware.
The DFIR Report, earlier this 12 months, additionally documented how QBot infections transfer at a speedy tempo, enabling the malware to reap browser knowledge and Outlook emails a mere half-hour after preliminary entry and propagate the payload to an adjoining workstation across the 50-minute mark.