An “extraordinarily subtle” Chinese language-speaking superior persistent menace (APT) actor dubbed LuoYu has been noticed utilizing a malicious Home windows software known as WinDealer that is delivered via man-on-the-side assaults.
“This groundbreaking improvement permits the actor to switch community visitors in-transit to insert malicious payloads,” Russian cybersecurity firm Kaspersky mentioned in a brand new report. “Such assaults are particularly harmful and devastating as a result of they don’t require any interplay with the goal to result in a profitable an infection.”
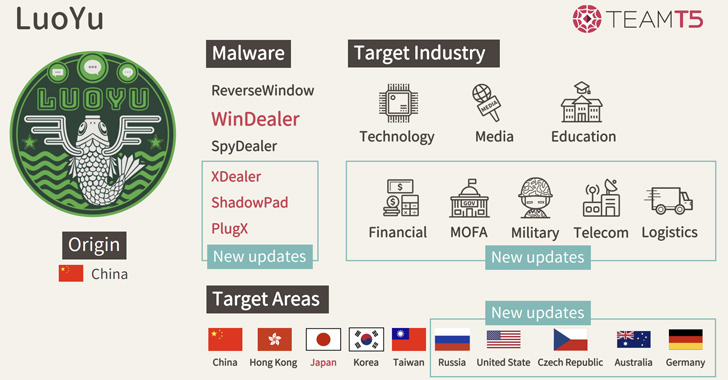
Recognized to be energetic since 2008, organizations focused by LuoYu are predominantly international diplomatic organizations established in China and members of the tutorial group in addition to monetary, protection, logistics, and telecommunications corporations.
LuoYu’s use of WinDealer was first documented by Taiwanese cybersecurity agency TeamT5 on the Japan Safety Analyst Convention (JSAC) in January 2021. Subsequent assault campaigns have used the malware to focus on Japanese entities, with remoted infections reported in Austria, Germany, India, Russia, and the U.S.
Different instruments which are a part of the adversary’s malware arsenal embrace PlugX and its successor ShadowPad, each of which have been utilized by quite a lot of Chinese language menace actors to allow their strategic goals. Moreover, the actor is thought to focus on Linux, macOS, and Android units.
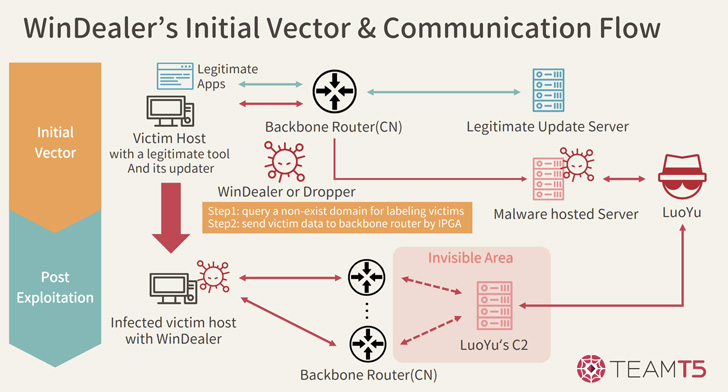
WinDealer, for its half, has been delivered previously by way of web sites that act as watering holes and within the type of trojanized functions masquerading as immediate messaging and video internet hosting providers like Tencent QQ and Youku.
However the an infection vector has since been traded for one more distribution technique that makes use of the automated replace mechanism of choose reputable functions to serve a compromised model of the executable on “uncommon events.”
WinDealer, a modular malware platform at its core, comes with all the standard bells and whistles related to a conventional backdoor, permitting it to vacuum delicate info, seize screenshots, and execute arbitrary instructions.
However the place it additionally stands aside is its use of a posh IP era algorithm to pick out a command-and-control (C2) server to hook up with at random from a pool of 48,000 IP addresses.
“The one option to clarify these seemingly not possible community behaviors is by assuming the existence of a man-on-the-side attacker who is ready to intercept all community visitors and even modify it if wanted,” the corporate mentioned.
A man-on-the-side assault, just like a man-in-the-middle assault, allows a rogue interloper to learn and inject arbitrary messages right into a communications channel, however not modify or delete messages despatched by different events.
Such intrusions usually financial institution on strategically timing their messages such that the malicious reply containing the attacker-supplied information is shipped in response to a sufferer’s request for an internet useful resource earlier than the precise response from the server.
The truth that the menace actor is ready to management such an enormous vary of IP addresses may additionally clarify the hijacking of the replace mechanism related to real apps to ship the WinDealer payload, Kaspersky identified.
“Man-on-the-side-attacks are extraordinarily harmful as the one situation wanted to assault a tool is for it to be linked to the web,” safety researcher Suguru Ishimaru mentioned.
“Regardless of how the assault has been carried out, the one manner for potential victims to defend themselves is to stay extraordinarily vigilant and have strong safety procedures, resembling common antivirus scans, evaluation of outbound community visitors, and in depth logging to detect anomalies.”