A newly created synthetic intelligence (AI) system based mostly on deep reinforcement studying (DRL) can react to attackers in a simulated setting and block 95% of cyberattacks earlier than they escalate.
That is based on the researchers from the Division of Vitality’s Pacific Northwest Nationwide Laboratory who constructed an summary simulation of the digital battle between attackers and defenders in a community and educated 4 totally different DRL neural networks to maximise rewards based mostly on stopping compromises and minimizing community disruption.
The simulated attackers used a sequence of ways based mostly on the MITRE ATT&CK framework’s classification to maneuver from the preliminary entry and reconnaissance section to different assault phases till they reached their objective: the affect and exfiltration section.
The profitable coaching of the AI system on the simplified assault setting demonstrates that defensive responses to assaults in actual time could possibly be dealt with by an AI mannequin, says Samrat Chatterjee, a knowledge scientist who introduced the staff’s work on the annual assembly of the Affiliation for the Development of Synthetic Intelligence in Washington, DC on Feb. 14.
“You do not need to transfer into extra advanced architectures when you can not even present the promise of those methods,” he says. “We wished to first reveal that we will really prepare a DRL efficiently and present some good testing outcomes, earlier than shifting ahead.”
The applying of machine studying and synthetic intelligence methods to totally different fields inside cybersecurity has turn into a scorching development over the previous decade, from the early integration of machine studying in e mail safety gateways within the early 2010s to more moderen efforts to use ChatGPT to research code or conduct forensic evaluation. Now, most safety merchandise have — or declare to have — just a few options powered by machine studying algorithms educated on massive datasets.
But creating an AI system able to proactive protection continues to be aspirational, quite than sensible. Whereas a wide range of hurdles stay for researchers, the PNNL analysis exhibits that an AI defender could possibly be doable sooner or later.
“Evaluating a number of DRL algorithms educated below numerous adversarial settings is a vital step towards sensible autonomous cyber protection options,” the PNNL analysis staff acknowledged of their paper. “Our experiments recommend that model-free DRL algorithms could be successfully educated below multi-stage assault profiles with totally different talent and persistence ranges, yielding favorable protection outcomes in contested settings.”
How the System Makes use of MITRE ATT&CK
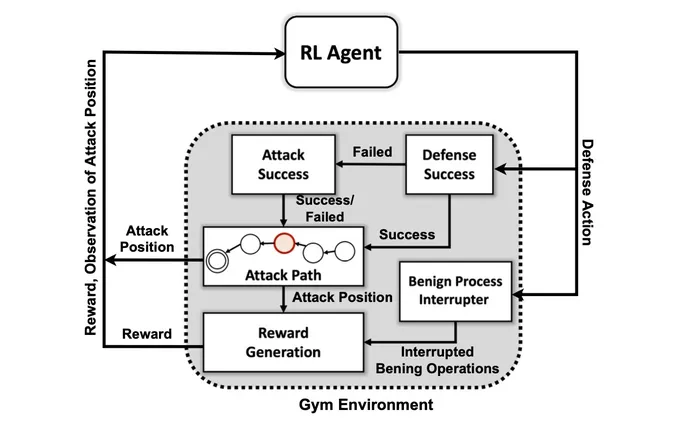
The primary objective of the analysis staff was to create a customized simulation setting based mostly on an open supply toolkit often called Open AI Gymnasium. Utilizing that setting, the researchers created attacker entities of various talent and persistence ranges with the power to make use of a subset of seven ways and 15 methods from the MITRE ATT&CK framework.
The objectives of the attacker brokers are to maneuver via the seven steps of the assault chain, from preliminary entry to execution, from persistence to command and management, and from assortment to affect.
For the attacker, adapting their ways to the state of the setting and the defender’s present actions could be advanced, says PNNL’s Chatterjee.
“The adversary has to navigate their method from an preliminary recon state all the way in which to some exfiltration or affect state,” he says. “We’re not making an attempt to create a type of mannequin to cease an adversary earlier than they get contained in the setting — we assume that the system is already compromised.”
The researchers used 4 approaches to neural networks based mostly on reinforcement studying. Reinforcement studying (RL) is a machine studying method that emulates the reward system of the human mind. A neural community learns by strengthening or weakening sure parameters for particular person neurons to reward higher options, as measured by a rating indicating how nicely the system performs.
Reinforcement studying primarily permits the pc to create a superb, however not excellent, method to the issue at hand, says Mahantesh Halappanavar, a PNNL researcher and an creator of the paper.
“With out utilizing any reinforcement studying, we might nonetheless do it, however it could be a very massive drawback that won’t have sufficient time to really provide you with any good mechanism,” he says. “Our analysis … provides us this mechanism the place deep reinforcement studying is kind of mimicking a number of the human habits itself, to some extent, and it will probably discover this very huge area very effectively.”
Not Prepared for Prime Time
The experiments discovered {that a} particular reinforcement studying methodology, often called a Deep Q Community, created a powerful resolution to the defensive drawback, catching 97% of the attackers within the testing information set. But the analysis is just the beginning. Safety professionals shouldn’t search for an AI companion to assist them do incident response and forensics anytime quickly.
Among the many many issues that stay to be solved is getting reinforcement studying and deep neural networks to elucidate the components that influenced their choices, an space of analysis referred to as explainable reinforcement studying (XRL).
As well as, the robustness of the AI algorithms and discovering environment friendly methods of coaching the neural networks are each issues that should be solved, says PNNL’s Chatterjee.
“Making a product— that was not the primary motivation for this analysis,” he says. “This was extra about scientific experimentation and algorithmic discovery.”