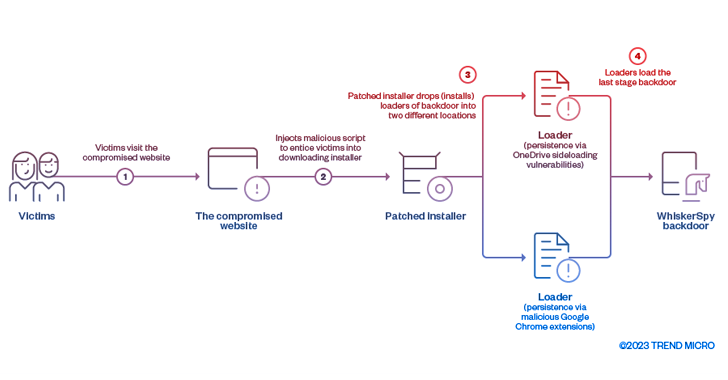
The cyber espionage menace actor tracked as Earth Kitsune has been noticed deploying a brand new backdoor referred to as WhiskerSpy as a part of a social engineering marketing campaign.
Earth Kitsune, energetic since at the very least 2019, is identified to primarily goal people thinking about North Korea with self-developed malware reminiscent of dneSpy and agfSpy. Beforehand documented intrusions have entailed using watering holes that leverage browser exploits in Google Chrome and Web Explorer to activate the an infection chain.
The differentiating issue within the newest assaults is a shift to social engineering to trick customers into visiting compromised web sites associated to North Korea, in keeping with a brand new report from Development Micro launched final week.
The cybersecurity firm mentioned the web site of an unnamed pro-North Korean group was hacked and modified to distribute the WhiskerSpy implant. The compromise was found on the finish of final 12 months.
“When a focused customer tries to look at movies on the web site, a malicious script injected by the attacker shows a message immediate notifying the victims with a video codec error to entice them to obtain and set up a trojanized codec installer,” researchers Joseph C Chen and Jaromir Horejsi mentioned.
The booby-trapped script is claimed to have been injected into the web site’s video pages, with the installer (“Codec-AVC1.msi”) subsequently employed to load WhiskerSpy.
However the assault additionally displays some intelligent methods in an try and sidestep detection. This includes delivering the malicious script solely to these guests whose IP addresses match particular standards –
- An IP tackle subnet situated in Shenyang, China
- A particular IP tackle situated in Nagoya, Japan, and
- An IP tackle subnet situated in Brazil
Development Micro famous that the focused IP addresses in Brazil belong to a business VPN service and that the menace actor might have “used this VPN service to check the deployment of their watering gap assaults.”
Persistence is achieved by both abusing a Dynamic Library Hyperlink (DLL) hijacking vulnerability in OneDrive or by way of a malicious Google Chrome extension that employs native messaging APIs to execute the payload each time the online browser is launched.
The WhiskerSpy backdoor, like different malware of its sort, comes with capabilities to delete, enumerate, obtain and add recordsdata, take screenshots, inject shellcode, load arbitrary executables.
“Earth Kitsune are proficient with their technical skills and are repeatedly evolving their instruments, techniques, and procedures,” the researchers mentioned.
Earth Yako Strikes Tutorial and Analysis Sectors in Japan
Earth Kitsune isn’t the one menace actor to go after Japanese targets, for the cybersecurity firm additionally detailed one other intrusion set codenamed Earth Yako putting analysis organizations and assume tanks within the nation.
The exercise, noticed as lately as January 2023, is a continuation of a beforehand identified marketing campaign known as Operation RestyLink. A subset of the assaults additionally focused entities situated in Taiwan.
“The intrusion set launched new instruments and malware inside a brief time frame, incessantly altering and increasing its assault targets,” Development Micro mentioned, stating Earth Yako’s modus operandi of “actively altering their targets and strategies.”
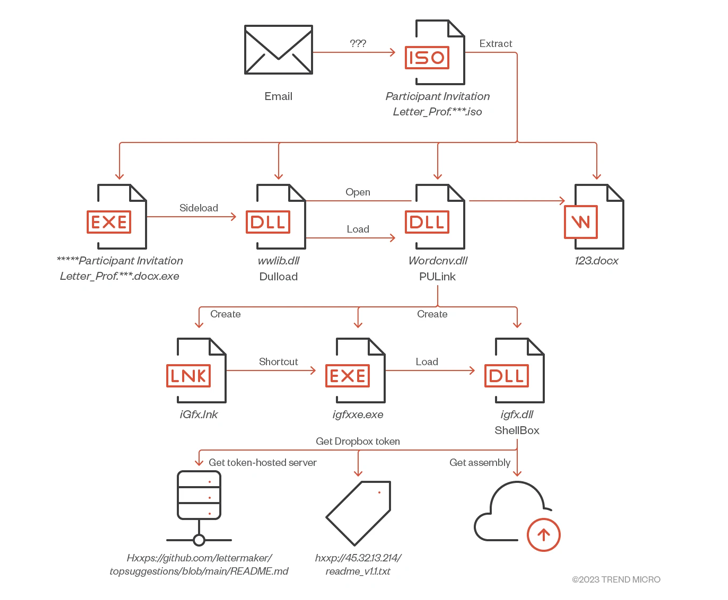
The place to begin is a spear-phishing electronic mail that masquerades as invites to public occasions. The messages comprise a malicious URL that factors to a payload, which, in flip, is answerable for downloading the malware onto the system.
The assaults are additionally characterised by a trove of customized instruments comprising droppers (PULink), loaders (Dulload, MirrorKey), stagers (ShellBox), and backdoors (PlugBox, TransBox).
PlugBox, ShellBox, and TransBox, because the names suggest, reap the benefits of Dropbox APIs to retrieve next-stage malware from a distant server hard-coded in a GitHub repository, obtain instructions, and harvest and exfiltrate information.
The precise origins of Earth Yako stay unknown, however Development Micro mentioned it recognized partial technical overlaps between the group and different menace actors like Darkhotel, APT10 (aka Stone Panda), and APT29 (aka Cozy Bear or Nobelium).
“One of many traits of the current focused assaults is that they shifted to focusing on the people thought-about to have comparatively weak safety measures in comparison with corporations and different organizations,” the corporate mentioned.
“This shift to focusing on people over enterprises is highlighted by the focusing on and abuse of Dropbox as it’s thought-about a preferred service within the area amongst customers for private use, however not for organizations.”