Nicknamed ProxyNotShell, a brand new exploit used within the wild takes benefit of the not too long ago revealed Microsoft Server-Aspect Request Forgery (SSRF) vulnerability CVE-2022-41040 and a second vulnerability, CVE-2022-41082 that enables Distant Code Execution (RCE) when PowerShell is accessible to unidentified attackers.
Based mostly on ProxyShell, this new zero-day abuse danger leverage a chained assault much like the one used within the 2021 ProxyShell assault that exploited the mix of a number of vulnerabilities – CVE-2021-34523, CVE-2021-34473, and CVE-2021-31207 – to allow a distant actor to execute arbitrary code.
Regardless of the potential severity of assaults utilizing them, ProxyShell vulnerabilities are nonetheless on CISA’s checklist of prime 2021 routinely exploited vulnerabilities.
Meet ProxyNotShell
Recorded on September 19, 2022, CVE-2022-41082 is an assault vector concentrating on Microsoft’s Change Servers, enabling assaults of low complexity with low privileges required. Impacted companies, if susceptible, allow an authenticated attacker to compromise the underlying alternate server by leveraging current alternate PowerShell, which might lead to a full compromise.
With the assistance of CVE-2022-41040, one other Microsoft vulnerability additionally recorded on September 19, 2022, an attacker can remotely set off CVE-2022-41082 to remotely execute instructions.
Although a person must have the privilege to entry CVE-2022-41040, which ought to curtail the vulnerability accessibility to attackers, the required stage of privilege is low.
On the time of writing, Microsoft has not but issued a patch however recommends that customers add a blocking rule as a mitigation measure.
Each vulnerabilities had been uncovered throughout an energetic assault in opposition to GTSC, a Vietnamese group referred to as GTSC, granting attackers entry to a few of their purchasers. Although neither vulnerability by itself is especially harmful, exploits chaining them collectively might doubtlessly result in catastrophic breaches.
The chained vulnerabilities might grant an outsider attacker the power to learn emails immediately off a company’s server the power to breach the group with CVE-2022-41040 Distant Code Execution and implant malware on the group’s Change Server with CVE-2022-41082.
Although it seems that attackers would wish some stage of authentication to activate the chained vulnerabilities exploit, the precise stage of authentication required – rated “Low” by Microsoft – will not be but clarified. But, this required low authentication stage ought to successfully forestall an enormous, automated assault concentrating on each Change server across the globe. This hopefully will forestall a replay of the 2021 ProxyShell debacle.
But, discovering a single legitimate electronic mail tackle/password mixture on a given Change server shouldn’t be overly troublesome, and, as this assault bypasses MFA or FIDO token validation to log into Outlook Net Entry, a single compromised electronic mail tackle/password mixture is all that’s wanted.
Mitigating ProxyNotShell Publicity
On the time of writing, Microsoft has not but issued a patch however recommends that customers add a blocking rule as a mitigation measure of unknown efficacy.
Blocking incoming site visitors to Change Servers holding vital asserts can also be an choice, although solely practicable if such a measure doesn’t impression important operations and may ideally be perceived as a short lived measure pending Microsoft’s issuance of a verified patch.
Assessing ProxyNotShell Publicity
As the present mitigation choices are both of unverified efficacy or doubtlessly damaging to the graceful working of operations, evaluating the diploma of publicity to ProxyNotShell may forestall taking doubtlessly disruptive pointless preventative measures, or point out which property to preemptively migrate to unexposed servers.
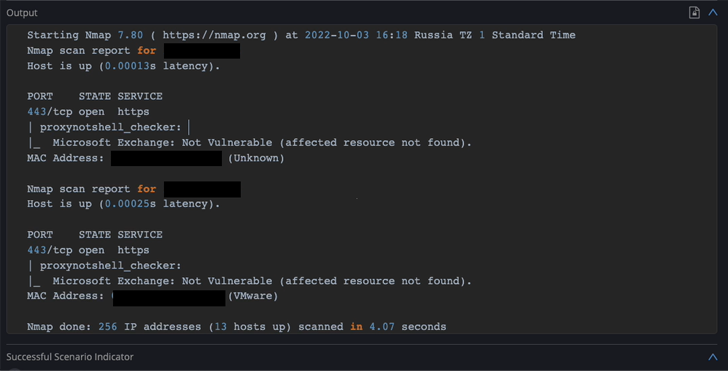
Cymulate Analysis Lab has developed a custom-made evaluation for ProxyNotShell that allow organizations to estimate precisely their diploma of publicity to ProxyNotShell.
A ProxyNotShell assault vector has been added to the superior eventualities templates, and working it in your surroundings yields the required info to validate publicity – or lack thereof – to ProxyNotShell.
Till verified patches can be found from Microsoft, assessing publicity to ProxyNotShell to guage precisely which servers are potential targets is essentially the most cost-efficient technique to consider precisely which property are uncovered and devise focused preemptive measures with most impression.
Notice: This text is contributed by Cymulate Analysis Labs.