Cloud-native know-how is rising in significance, and the Cloud Native Computing Basis (CNCF), a part of the Linux Basis, is a key group driving collaboration on cloud safety all through the {industry}.
That collaboration contains occasions akin to KubeCon Americas and Europe, which regularly function cloud-native safety as a key subject, however seeing the significance of cloud native safety, CNCF took the subsequent step and created a separate occasion.
CloudNativeSecurityCon North America 2023 (CNSC) lately befell in Seattle, and served as the primary vendor-neutral, practitioner-driven convention centered solely on cloud-native safety. The occasion featured over 800 attendees and 50 sponsors. It had 70-plus classes for all safety ranges of technologists.
Safety Is Folks-Powered; Business Collaboration Is a Resolution
Safety stays a urgent problem for the cloud-native and open supply neighborhood, stated Priyanka Sharma, Govt Director, CNCF. Throughout her keynote, she stated there are 7.1 million-plus cloud-native builders based on Slash Knowledge.
She emphasised that the {industry} wants “a paradigm shift to stage up our efficiency,” as cloud utilization will proceed to develop, and so will the threats associated to it.
Although the organizations are doing their half to safe their cloud environments, Sharma indicated that top-down strategy will not be the easiest way, as a substitute having a extra bottom-up strategy from the neighborhood, pointing to software program safety vendor Snyk’s “2022 State of Cloud Safety Report,” which confirmed 77% of organizations noticed poor coaching and collaboration as a significant cloud safety problem.

Having siloed groups working in numerous international locations, utilizing totally different instruments, and relying on unmonitored insurance policies are frequent safety challenges in lots of enterprise safety eventualities, however once they contain the cloud, it multiplies difficulties to the safety setting additional. Therefore, Sharma said, “Safety is people-powered,” and having industry-level collaboration from all of the stakeholders together with a shared asset listing will enhance cloud safety throughout the {industry}. Even after all of the talks about innovation and proper strategy completed within the cloud-native area, a talent scarcity is one thing the {industry} remains to be going through. CNCF introduced Kubernetes and Cloud Affiliate (KCSA) certification, to handle the most important problem of lack of technical experience in cloud-native setting.
CNCF organizes itself with Technical Advisory Teams (TAGs) for various focus areas, and it’s trying to a Safety TAG to assist organizations with facilitating the safety for initiatives throughout the cloud-native ecosystem. It is a 165-member crew that helps CNCF initiatives by way of training, partnership, and mission engagement. This group will assist with security measures for any CNCF initiatives; any incubating mission inside the group should now undergo a safety audit by the Safety TAG. The Sigstore mission that was adopted by Kubernetes was an instance of such open, multivendor collaboration.
Key Convention Subjects
Themes that popped up in the course of the occasion — together with SBOM, runtime safety, infrastructure as-a-code safety, code to safe insurance policies and authentication, and ChatGPT — indicated that the adoption of cloud-native purposes will proceed to develop, and the {industry} should prioritize safety for these purposes. The considered having an open supply safety device for securing open supply code is smart. At the moment, CNCF has 21 security-related open-source initiatives: Open Coverage Agent (OPA) and Replace Framework TUF have graduated with 5 different incubating initiatives, and the remainder are within the sandbox stage.
Software program Provide Chain Safety
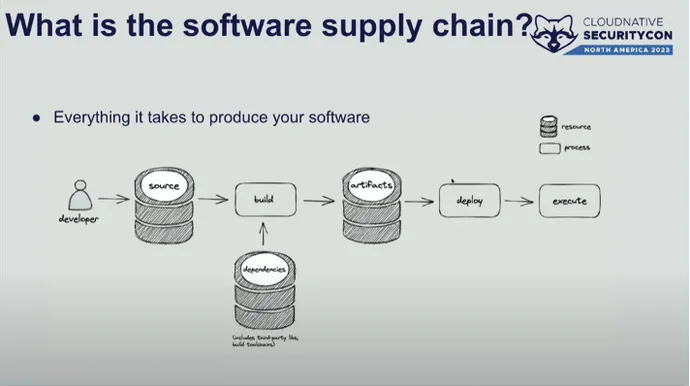
Many classes on the convention had been centered on understanding what the software program provide chain means and why securing it stays necessary.
A chat by a Yahoo consultant highlighted how 85% to 97% of enterprise code makes use of open supply parts, and any vulnerabilities in these could pose safety threats. That problem underscores the significance of getting safety ingrained at each stage of the software program growth life cycle (SDLC), from software growth to CI/CD pipeline right down to manufacturing.
Code dependencies have grow to be one of the frequent causes main to produce chain assaults. Based on a latest report on software program provide chain safety, provide chain assaults have grown 742% year-over-year previously three years. Due to this fact, a DevSecOps strategy is necessary to make sure the DevOps workflow is maintained by making safety seamless. It means having safety as an intrinsic a part of software growth, integration, and operation in DevOps-centric environments.
“Shift Proper” Is as Essential as “Shift Left”
Deployment of purposes within the cloud has been a fast-track initiative for a lot of enterprises, typically in help of digital transformation initiatives, however most of the similar safety challenges, akin to software program vulnerabilities, managing configuration and permission, compliance, and detecting and responding to threats, plaguing conventional purposes additionally hamper cloud software safety.
From the cloud-native viewpoint, two tendencies are most seen. The primary is the best way wherein “shift left” corresponds to the utilization of CI/CD safety, having centralized duties and dependencies that may be monitored. It factors to shifting safety towards an earlier stage within the software program growth life cycle, particularly that safety is inbuilt from the time the supply code is created.
However the second pattern is “shift proper,” which is gaining equal significance in understanding what’s going on within the runtime setting because the workload deployed on microservices and orchestrated by Kubernetes. The Falco mission with CNCF (initially began by Sysdig), which relies on eBPF know-how, seeks to assist organizations perceive what each course of is doing in its containers and hosts. It is sort of a safety digicam for the cloud setting.
Software program Invoice of Supplies
Log4j was a prime of thoughts in the course of the present, highlighting the way it disrupted the operations of many organizations in so many various methods.
Comparable high-profile assaults on the availability chain had been the explanation for the US federal authorities to problem an govt order to create pointers for securing software program options used for the federal government. The change of strategy to constructing software program utilizing third-party dependencies makes having full transparency within the software necessary.
So, the strategy of sustaining a software program invoice of supplies (SBOM) that can supply a list all parts, modules, and libraries used within the software and likewise drawing the connection between provide chain parts is turning into more and more necessary.
One attention-grabbing alternate in the course of the convention tackled the way to deal with metadata that will likely be collected over time by every software program factor. In a panel, a Google consultant talked about its new product, Graph for Understanding Artifact Composition (GUAC), which capabilities like an aggregator for this metadata in a high-fidelity graph database.
Sponsor Panorama
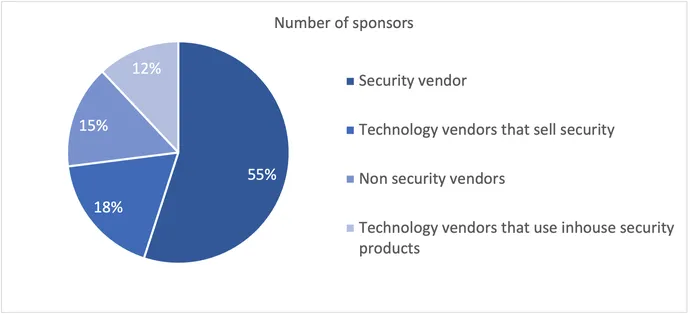
CNSC was a comparatively small-scale convention, however its sponsors represented distributors distributed throughout the {industry}. Roughly 55% had been safety distributors, 18% know-how distributors providing some safety, 12% had been know-how distributors that use in-house safety product however don’t promote the safety product as a stand-alone providing, and 15% non-security distributors.
A Sturdy Begin
The primary-ever CNSC was a robust begin for the cloud-native neighborhood to create a spot to assemble every year for a centered have a look at safety challenges and alternatives in cloud-native environments.
CNCF is doing an incredible job getting several types of distributors collectively and supporting cloud-native safety initiatives. That is exposing builders to safety considerations. Quite the opposite, conventional safety groups additionally should be taught to work higher with builders and guarantee safety approaches align with growth priorities and enterprise targets.
That is only a first step towards fixing the issues associated to cloud-native safety. There may be extra collaboration with folks and course of to be completed in future.