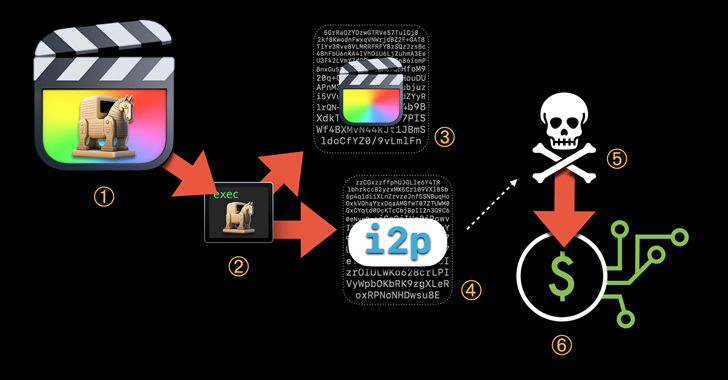
Trojanized variations of reputable functions are getting used to deploy evasive cryptocurrency mining malware on macOS methods.
Jamf Risk Labs, which made the invention, stated the XMRig coin miner was executed as Closing Reduce Professional, a video enhancing software program from Apple, which contained an unauthorized modification.
“This malware makes use of the Invisible Web Undertaking (i2p) […] to obtain malicious elements and ship mined foreign money to the attacker’s pockets,” Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley stated in a report shared with The Hacker Information.
An earlier iteration of the marketing campaign was documented precisely a 12 months in the past by Development Micro, which identified the malware’s use of i2p to hide community visitors and speculated that it could have been delivered as a DMG file for Adobe Photoshop CC 2019.
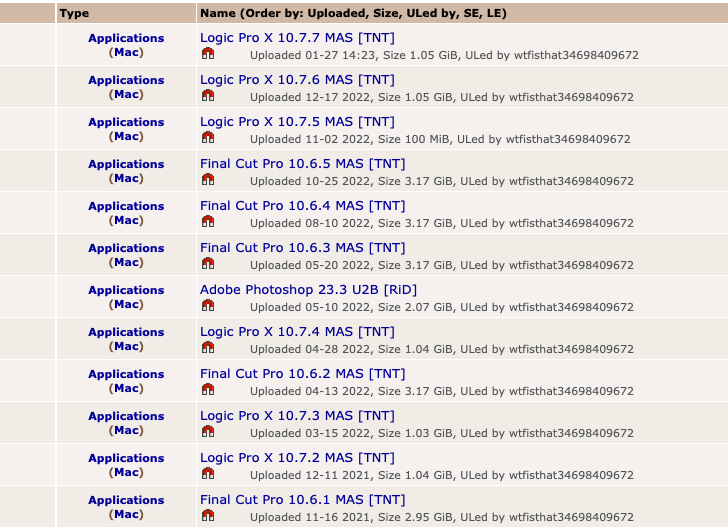
The Apple system administration firm stated the supply of the cryptojacking apps could be traced to Pirate Bay, with the earliest uploads relationship all the best way again to 2019.
The result’s the invention of three generations of the malware, noticed first in August 2019, April 2021, and October 2021, that charts the evolution of the marketing campaign’s sophistication and stealth.
One instance of the evasion method is a shell script that screens the record of working processes to test for the presence of Exercise Monitor, and if that’s the case, terminate the mining processes.
The malicious mining course of banks on the person launching the pirated utility, upon which the code embedded within the executable connects to an actor-controlled server over i2p to obtain the XMRig element.
The malware’s means to fly beneath the radar, coupled with the truth that customers working cracked software program are willingly doing one thing unlawful, has made the distribution vector a extremely efficient one for a few years.
Apple, nonetheless, has taken steps to fight such abuse by subjecting notarized apps to extra stringent Gatekeeper checks in macOS Ventura, thereby stopping tampered apps from being launched.
“However, macOS Ventura didn’t stop the miner from executing,” Jamf researchers famous. “By the point the person receives the error message, that malware has already been put in.”
“It did stop the modified model of Closing Reduce Professional from launching, which may increase suspicion for the person in addition to drastically cut back the chance of subsequent launches by the person.”