A risk with a North Korea nexus has been discovered leveraging a “novel spear phish methodology” that includes making use of trojanized variations of the PuTTY SSH and Telnet shopper.
Google-owned risk intelligence agency Mandiant attributed the brand new marketing campaign to an rising risk cluster it tracks beneath the title UNC4034.
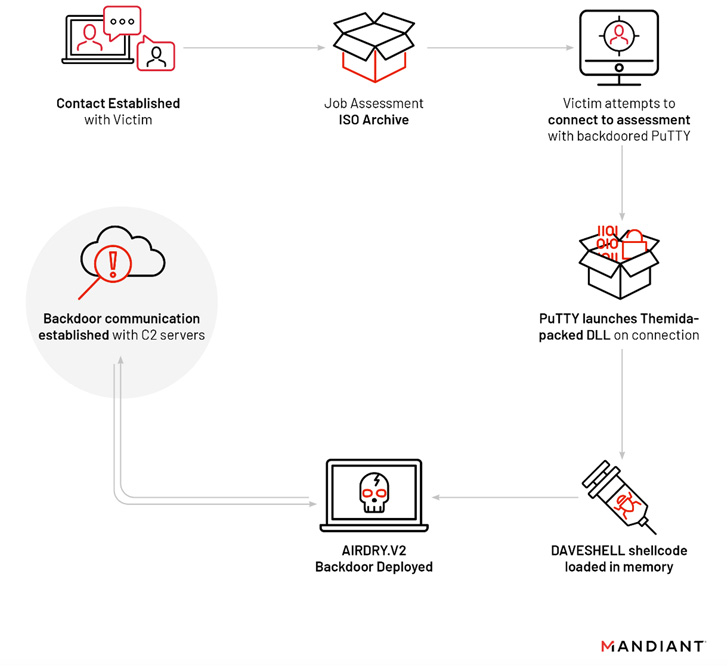
“UNC4034 established communication with the sufferer over WhatsApp and lured them to obtain a malicious ISO package deal relating to a pretend job providing that led to the deployment of the AIRDRY.V2 backdoor by way of a trojanized occasion of the PuTTY utility,” Mandiant researchers stated.
The utilization of fabricated job lures as a pathway for malware distribution is an oft-used tactic by North Korean state-sponsored actors, together with the Lazarus Group, as a part of a permanent marketing campaign referred to as Operation Dream Job.
The entry level of the assault is an ISO file that masquerades as an Amazon Evaluation as a part of a possible job alternative on the tech large. The file was shared over WhatApp after establishing preliminary contact over e mail.
The archive, for its half, holds a textual content file containing an IP tackle and login credentials, and an altered model of PuTTY that, in flip, masses a dropper referred to as DAVESHELL, which deploys a more moderen variant of a backdoor dubbed AIRDRY.
It is possible that the risk actor satisfied the sufferer to launch a PuTTY session and use the credentials supplied within the TXT file to connect with the distant host, successfully activating the an infection.
AIRDRY, also referred to as BLINDINGCAN, has previously been utilized by North Korea-linked hackers to strike U.S. protection contractors and entities in South Korea and Latvia.
Whereas earlier variations of the malware got here with practically 30 instructions for file switch, file administration, and command execution, the most recent model has been discovered to eschew the command-based strategy in favor of plugins which are downloaded and executed in reminiscence.
Mandiant stated it was in a position to include the compromise earlier than any additional post-exploitation actions might happen following the deployment of the implant.
The event is yet one more signal that using ISO information for preliminary entry is gaining traction amongst risk actors to ship each commodity and focused malware.
The shift can be attributable to Microsoft’s resolution to dam Excel 4.0 (XLM or XL4) and Visible Fundamental for Purposes (VBA) macros for Workplace apps downloaded from the web by default.