A brand new exploit has been devised to “unenroll” enterprise- or school-managed Chromebooks from administrative management.
Enrolling ChromeOS gadgets makes it potential to implement system insurance policies as set by the group through the Google Admin console, together with the options which are out there to customers.
“Every enrolled system complies with the insurance policies you set till you wipe or deprovision it,” Google states in its documentation.
That is the place the exploit – dubbed Shady Hacking 1nstrument Makes Machine Enrollment Retreat aka SH1MMER – is available in, permitting customers to bypass these admin restrictions.
The strategy can be a reference to shim, a Return Merchandise Authorization (RMA) disk picture utilized by service heart technicians to reinstall the working system and run analysis and restore packages.
The Google-signed shim picture is a “mixture of current Chrome OS manufacturing facility bundle elements” – particularly a launch picture, a toolkit, and the firmware, amongst others – that may be flashed to a USB drive.
A Chromebook can then be booted in developer mode with the drive picture to invoke the restoration choices. A shim picture can both be common or particular to a Chromebook board.
SH1MMER takes benefit of a modified RMA shim picture to create a restoration media for the Chromebook and writes it to a USB stick. Doing so requires an on-line builder to obtain the patched model of the RMA shim with the exploit.
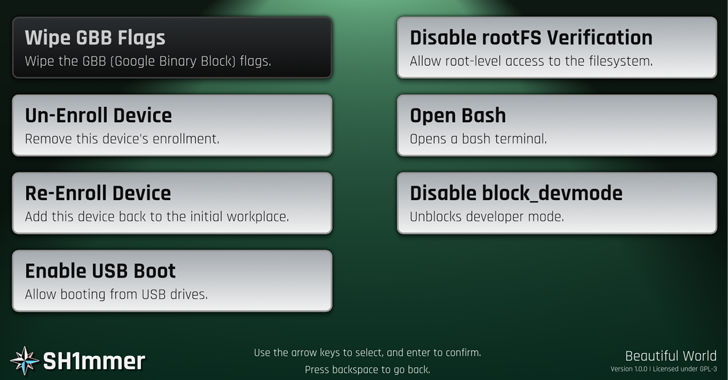
The following step entails launching the restoration mode on the Chromebook and plugging the USB stick containing the picture into the system to show an altered restoration menu that permits customers to utterly unenroll the machine.
“It should now behave fully as if it’s a private pc and now not comprise spy ware or blocker extensions,” the Mercury Workshop group, which got here up with the exploit, stated.
“RMA shims are a manufacturing facility software permitting sure authorization features to be signed, however solely the KERNEL partitions are checked for signatures by the firmware,” the group additional elaborated. “We will edit the opposite partitions to our will so long as we take away the pressured readonly bit on them.”
Moreover, the SH1MMER menu can be utilized to re-enroll the system, allow USB boot, open a bash shell, and even permit root-level entry to the ChromeOS working system.
The Hacker Information has reached out to Google for remark, and we’ll replace the story if we hear again.