A variant of the Mirai botnet generally known as MooBot is co-opting weak D-Hyperlink gadgets into a military of denial-of-service bots by benefiting from a number of exploits.
“If the gadgets are compromised, they are going to be absolutely managed by attackers, who may make the most of these gadgets to conduct additional assaults similar to distributed denial-of-service (DDoS) assaults,” Palo Alto Networks Unit 42 stated in a Tuesday report.
MooBot, first disclosed by Qihoo 360’s Netlab group in September 2019, has beforehand focused LILIN digital video recorders and Hikvision video surveillance merchandise to broaden its community.
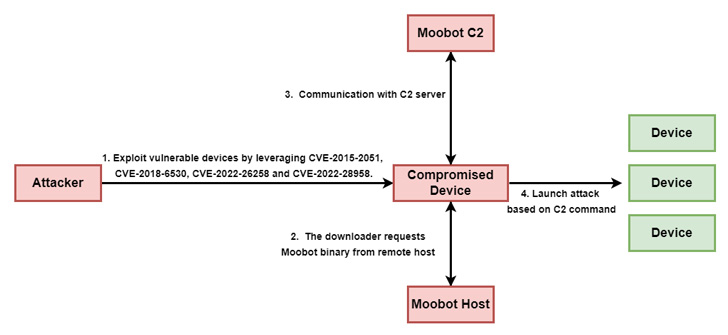
Within the newest wave of assaults found by Unit 42 in early August 2022, as many as 4 completely different flaws in D-Hyperlink gadgets, each previous and new, have paved the best way for the deployment of MooBot samples. These embrace –
- CVE-2015-2051 (CVSS rating: 10.0) – D-Hyperlink HNAP SOAPAction Header Command Execution Vulnerability
- CVE-2018-6530 (CVSS rating: 9.8) – D-Hyperlink SOAP Interface Distant Code Execution Vulnerability
- CVE-2022-26258 (CVSS rating: 9.8) – D-Hyperlink Distant Command Execution Vulnerability, and
- CVE-2022-28958 (CVSS rating: 9.8) – D-Hyperlink Distant Command Execution Vulnerability
Profitable exploitation of the aforementioned flaws may result in distant code execution and the retrieval of a MooBot payload from a distant host, which then parses directions from a command-and-control (C2) server to launch a DDoS assault on a selected IP tackle and port quantity.
Prospects of D-Hyperlink home equipment are extremely advisable to use patches and upgrades launched by the corporate to mitigate potential threats.
“The vulnerabilities […] have low assault complexity however important safety impression that may result in distant code execution,” the researchers stated. “As soon as the attacker positive factors management on this method, they may take benefit by together with the newly compromised gadgets into their botnet to conduct additional assaults similar to DDoS.”