Since Wi-Fi routers interface immediately with the open internet, they make for prime targets for risk actors seeking to construct out a botnet. The marketing campaign detailed by Unit 42 researchers leverages 4 totally different vulnerabilities unfold throughout numerous D-Hyperlink routers. All 4 vulnerabilities are listed within the Nationwide Vulnerability Database (NVD), and three of them have vital severity scores of 9.8 out of 10.
The fourth vulnerability, which is listed as CVE-2015-2051 and impacts D-Hyperlink’s DIR-645 Router, at present lacks a CVSS Model 3.x severity rating because it was not too long ago up to date with further data and is awaiting reanalysis. Nonetheless, in contrast to the opposite three vulnerabilities, this one is listed within the Cybersecurity and Infrastructure Safety Company’s (CISA) Identified Exploited Vulnerabilities Catalog. Whereas D-Hyperlink has launched patches for all 4 vulnerabilities exploited on this marketing campaign, the DIR-645 Router has reached finish of life, so CISA recommends retiring this gadget.
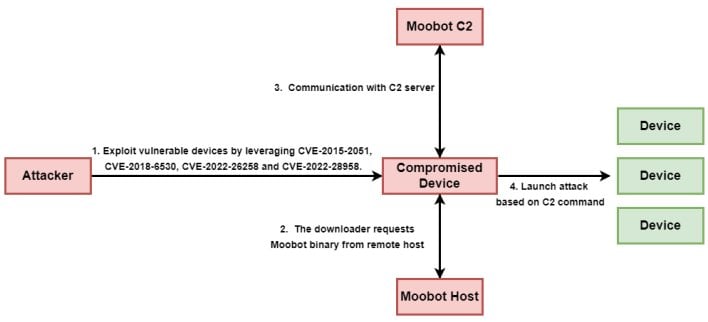
These with D-Hyperlink routers ought to be sure that these units are updated, in order to guard them from being subsumed into the MooBot botnet. The 4 vulnerabilities leveraged on this marketing campaign are as follows:
| Vulnerability | Affected Router(s) |
| CVE-2015-2051 |
DIR-645 |
| CVE-2018-6530 | DIR-880L, DIR-868L, DIR-65L, DIR-860L |
| CVE-2022-26258 |
DIR-816L |
| CVE-2022-28958 |
DIR-820L |


