The risk actor behind the SolarWinds provide chain assault has been linked to yet one more “extremely focused” post-exploitation malware that might be used to take care of persistent entry to compromised environments.
Dubbed MagicWeb by Microsoft’s risk intelligence groups, the event reiterates Nobelium’s dedication to creating and sustaining purpose-built capabilities.
Nobelium is the tech large’s moniker for a cluster of actions that got here to mild with the subtle assault focusing on SolarWinds in December 2020, and which overlaps with the Russian nation-state hacking group broadly often known as APT29, Cozy Bear, or The Dukes.
“Nobelium stays extremely lively, executing a number of campaigns in parallel focusing on authorities organizations, non-governmental organizations (NGOs), intergovernmental organizations (IGOs), and assume tanks throughout the US, Europe, and Central Asia,” Microsoft mentioned.
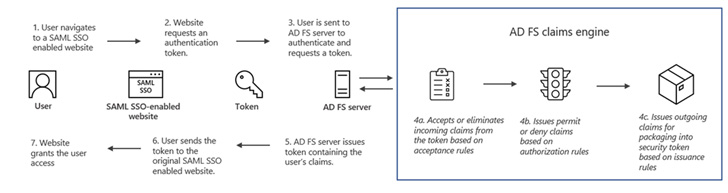
MagicWeb, which shares similarities with one other device known as FoggyWeb, is assessed to have been deployed to take care of entry and preempt eviction throughout remediation efforts, however solely after acquiring extremely privileged entry to an surroundings and shifting laterally to an AD FS server.
Whereas FoggyWeb comes with specialised capabilities to ship extra payloads and steal delicate info from Energetic Listing Federation Companies (AD FS) servers, MagicWeb is a rogue DLL (a backdoored model of “Microsoft.IdentityServer.Diagnostics.dll”) that facilitates covert entry to an AD FS system via an authentication bypass.
“Nobelium’s capability to deploy MagicWeb hinged on accessing extremely privileged credentials that had administrative entry to the AD FS servers, giving them the flexibility to carry out no matter malicious actions they needed to on the techniques that they had entry to,” Microsoft mentioned.
The findings come on the heels of the disclosure of an APT29-led marketing campaign aimed toward NATO-affiliated organizations with the purpose of accessing overseas coverage info.
Particularly, this entails disabling an enterprise logging function known as Purview Audit (beforehand Superior Audit) to reap emails from Microsoft 365 accounts.”APT29 continues to reveal distinctive operational safety and evasion ways,” Mandiant mentioned.
One other newer tactic utilized by the actor in current operations is using a password guessing assault to acquire the credentials related to a dormant account and enroll it for multi-factor authentication, granting it entry to the group’s VPN infrastructure.
APT29 stays a prolific risk group simply because it’s skillful. Final month, Palo Alto Networks Unit 42 flagged a phishing marketing campaign that takes benefit of Dropbox and Google Drive cloud storage companies for malware deployment and different post-compromise actions.