Microsoft on Monday revealed steerage for a newly found zero-day safety flaw in its Workplace productiveness suite that may very well be exploited to realize code execution on affected programs.
The weak point, now assigned the identifier CVE-2022-30190, is rated 7.8 out of 10 for severity on the CVSS vulnerability scoring system. Microsoft Workplace variations Workplace 2013, Workplace 2016, Workplace 2019, and Workplace 2021, in addition to Skilled Plus editions, are impacted.
“To assist shield prospects, we have revealed CVE-2022-30190 and extra steerage right here,” a Microsoft spokesperson advised The Hacker Information in an emailed assertion.
The Follina vulnerability, which got here to gentle late final week, concerned a real-world exploit that leveraged the shortcoming in a weaponized Phrase doc to execute arbitrary PowerShell code by making use of the “ms-msdt:” URI scheme. The pattern was uploaded to VirusTotal from Belarus.
However first indicators of exploitation of the flaw date again to April 12, 2022, when a second pattern was uploaded to the malware database. This artifact is believed to have focused a consumer in Russia with a malicious Phrase doc (“приглашение на интервью.doc“) that masqueraded as an interview invitation with Sputnik Radio.
“A distant code execution vulnerability exists when MSDT is named utilizing the URL protocol from a calling software similar to Phrase,” Microsoft mentioned in an advisory for CVE-2022-30190.
“An attacker who efficiently exploits this vulnerability can run arbitrary code with the privileges of the calling software. The attacker can then set up packages, view, change, or delete knowledge, or create new accounts within the context allowed by the consumer’s rights.”
The tech large credited crazyman, a member of the Shadow Chaser Group, for reporting the flaw on April 12, coinciding with the invention of the in-the-wild exploit focusing on Russian customers, indicating the corporate had been already conscious of the vulnerability.
Certainly, in line with screenshots shared by the researcher on Twitter, Microsoft closed the vulnerability submission report on April 21, 2022 stating “the difficulty has been fastened,” whereas additionally dismissing the flaw as “not a safety difficulty” because it requires a passkey offered by a help technician when beginning the diagnostic software.
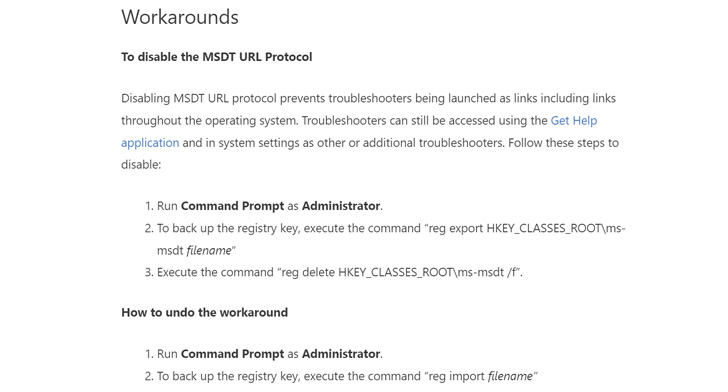
In addition to releasing detection guidelines for Microsoft Defender for Endpoint, the Redmond-based firm has supplied workarounds in its steerage to disable the MSDT URL protocol by way of a Home windows Registry modification.
“If the calling software is a Microsoft Workplace software, by default, Microsoft Workplace opens paperwork from the web in Protected View or Software Guard for Workplace, each of which forestall the present assault,” Microsoft mentioned.
This isn’t the primary time Microsoft Workplace protocol schemes like “ms-msdt:” have come below the scanner for his or her potential misuse. Earlier this January, German cybersecurity firm SySS disclosed the way it’s doable to open recordsdata immediately by way of specifically crafted URLs similar to “ms-excel:ofv|u|https://192.168.1.10/poc[.]xls.”