Authorities in america, Germany, the Netherlands and the U.Okay. final week mentioned they dismantled the “RSOCKS” botnet, a set of thousands and thousands of hacked units that had been bought as “proxies” to cybercriminals in search of methods to route their malicious visitors by way of another person’s laptop. Whereas the coordinated motion didn’t title the Russian hackers allegedly behind RSOCKS, KrebsOnSecurity has recognized its proprietor as a 35-year-old Russian man residing overseas who additionally runs the world’s high Russian spamming discussion board.
The RUSdot mailer, the e-mail spamming software made and bought by the administrator of RSOCKS.
Based on a press release by the U.S. Division of Justice, RSOCKS supplied purchasers entry to IP addresses assigned to units that had been hacked:
“A cybercriminal who wished to make the most of the RSOCKS platform might use an internet browser to navigate to a web-based ‘storefront’ (i.e., a public site that enables customers to buy entry to the botnet), which allowed the client to pay to hire entry to a pool of proxies for a specified each day, weekly, or month-to-month time interval. The price for entry to a pool of RSOCKS proxies ranged from $30 per day for entry to 2,000 proxies to $200 per day for entry to 90,000 proxies.”
The DOJ’s assertion doesn’t point out that RSOCKS has been in operation since 2014, when entry to the net retailer for the botnet was first marketed on a number of Russian-language cybercrime boards.
The person “RSOCKS” on the Russian crime discussion board Verified modified his title to RSOCKS from a earlier deal with: “Stanx,” whose very first gross sales thread on Verified in 2016 shortly ran afoul of the discussion board’s guidelines and prompted a public chastisement by the discussion board’s administrator.
Verified was hacked twice up to now few years, and every time the non-public messages of all customers on the discussion board had been leaked. These messages present that after being warned of his discussion board infraction, Stanx despatched a personal message to the Verified administrator detailing his cybercriminal bona fides.
“I’m the proprietor of the RUSdot discussion board (former Spamdot),” Stanx wrote in Sept. 2016. “In spam matters, individuals know me as a dependable particular person.”
A Google-translated model of the Rusdot spam discussion board.
RUSdot is the successor discussion board to Spamdot, a much more secretive and restricted discussion board the place a lot of the world’s high spammers, virus writers and cybercriminals collaborated for years earlier than the neighborhood’s implosion in 2010. Even at present, the RUSdot Mailer is marketed on the market on the high of the RUSdot neighborhood discussion board.
Stanx mentioned he was a longtime member of a number of main boards, together with the Russian hacker discussion board Antichat (since 2005), and the Russian crime discussion board Exploit (since April 2013). In an early publish to Antichat in January 2005, Stanx disclosed that he’s from Omsk, a big metropolis within the Siberian area of Russia.
Based on the cyber intelligence agency Intel 471, the person Stanx certainly registered on Exploit in 2013, utilizing the e-mail tackle stanx@rusdot.com, and the ICQ quantity 399611. A search in Google for that ICQ quantity turns up a cached model of a Vkontakte profile for a Denis “Neo” Kloster, from Omsk, Russia.
Cybersecurity agency Constella Intelligence reveals that in 2017, somebody utilizing the e-mail tackle istanx@gmail.com registered on the Russian freelancer job web site fl.ru with the profile title of “Denis Kloster” and the Omsk telephone variety of 79136334444. One other file listed by Constella suggests Denis’s actual surname could in actual fact be “Emilyantsev” [Емельянцев].
That telephone quantity is tied to the WHOIS registration information for a number of domains over time, together with proxy[.]data, allproxy[.]data, kloster.professional and deniskloster.com.

A replica of the passport for Denis Kloster, as posted to his Vkontakte web page in 2019. It reveals that in Oct. 2019, he obtained a visa from the American Embassy in Bangkok, Thailand.
The “about me” part of DenisKloster.com says the 35-year-old was born in Omsk, that he received his first laptop at age 12, and graduated from highschool at 16. Kloster says he’s labored in lots of giant corporations in Omsk as a system administrator, internet developer and photographer.
Based on Kloster’s weblog, his first actual job was operating an “internet advertising” agency he based referred to as Web Promoting Omsk (“riOmsk“), and that he even lived in New York Metropolis for some time.
“One thing new was required and I made a decision to go away Omsk and attempt to reside within the States,” Kloster wrote in 2013. “I opened an American visa for myself, it was not tough to get. And so I moved to reside in New York, the biggest metropolis on this planet, in a rustic the place all needs come true. However even this was not sufficient for me, and since then I started to journey the world.”
The present model of the About Me web page on Kloster’s web site says he closed his promoting enterprise in 2013 to journey the world and concentrate on his new firm: One that gives safety and anonymity companies to prospects around the globe. Kloster’s self-importance web site and LinkedIn web page each record him as CEO of an organization referred to as “SL MobPartners.”
In 2016, Deniskloster.com featured a publish celebrating three years in operation. The anniversary publish mentioned Kloster’s anonymity enterprise had grown to just about two dozen workers, most of whom had been included in a gaggle picture posted to that article (and a few of whom Kloster thanked by their first names and final initials).

The staff who stored issues operating for RSOCKS, circa 2016.
“Due to you, we at the moment are growing within the area of data safety and anonymity!,” the publish enthuses. “We make merchandise which might be utilized by 1000’s of individuals around the globe, and that is very cool! And that is only the start!!! We don’t simply work collectively and we’re not simply mates, we’re Household.”
Mr. Kloster didn’t reply to repeated requests for remark.
It’s not clear if the coordinated takedown focusing on the RSOCKS botnet will probably be everlasting, because the botnet’s house owners might merely rebuild — and probably rebrand — their crime machine. Based mostly on the RSOCKS proprietor’s posts, that’s precisely what they intend to do.
“RSocks ceases to exist,” wrote the Rsocks account on the BlackHatWorld discussion board on June 17. “However don’t fear. All of the energetic plans and fund balances will probably be transferred to a different service. Keep tuned. We’ll inform you about its title and all the main points later.”
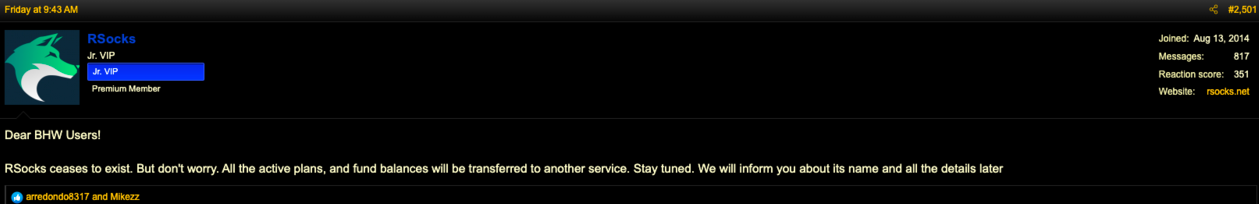
Rsocks informed the BlackHatWorld neighborhood they’d be again quickly underneath a brand new title.
Malware-based proxy companies like RSOCKS have struggled to stay aggressive in a cybercrime market with more and more subtle proxy companies that supply many extra options. The demise of RSOCKS follows intently on the heels of VIP72[.]com, a competing proxy botnet service that operated for a decade earlier than its house owners pulled the plug on the service final yr.

