A brand new piece of analysis from lecturers at ETH Zurich has recognized a lot of important safety points within the MEGA cloud storage service that could possibly be leveraged to interrupt the confidentiality and integrity of person information.
In a paper titled “MEGA: Malleable Encryption Goes Awry,” the researchers level out how MEGA’s system doesn’t shield its customers towards a malicious server, thereby enabling a rogue actor to completely compromise the privateness of the uploaded recordsdata.
“Moreover, the integrity of person information is broken to the extent that an attacker can insert malicious recordsdata of their selection which go all authenticity checks of the shopper,” ETH Zurich’s Matilda Backendal, Miro Haller, and Kenneth G. Paterson stated in an evaluation of the service’s cryptographic structure.
MEGA, which advertises itself because the “privateness firm” and claims to offer user-controlled end-to-end encrypted cloud storage, has greater than 10 million every day lively customers, with over 122 billion recordsdata uploaded to the platform to this point.
Chief among the many weaknesses is an RSA Key Restoration Assault that makes it attainable for MEGA (itself appearing maliciously) or a resourceful nation-state adversary answerable for its API infrastructure to recuperate a person’s RSA non-public key by tampering with 512 login makes an attempt and decrypt the saved content material.
“As soon as a focused account had made sufficient profitable logins, incoming shared folders, MEGAdrop recordsdata and chats may have been decryptable,” Mathias Ortmann, MEGA’s chief architect, stated in response to the findings. “Recordsdata within the cloud drive may have been successively decrypted throughout subsequent logins.”
The recovered RSA key can then be prolonged to make method for 4 different assaults –
- Plaintext Restoration Assault, which permits MEGA to decrypt node keys — an encryption key related to each uploaded file and are encrypted with a person’s grasp key — and use them to decrypt all person communication and recordsdata.
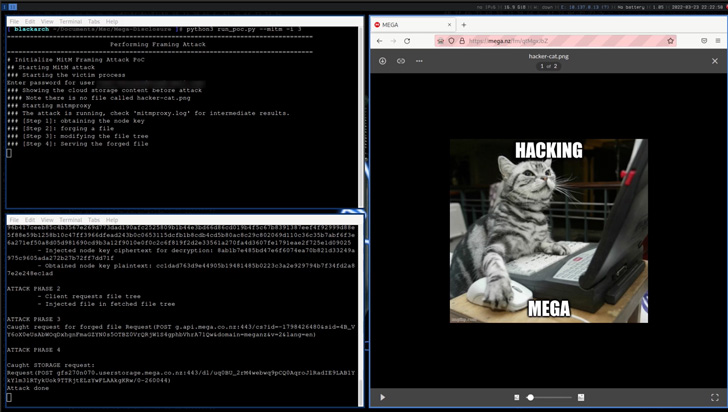
- Framing Assault, whereby MEGA can insert arbitrary recordsdata into the person’s file storage which might be indistinguishable from genuinely uploaded ones.
- Integrity Assault, a much less stealthy variant of the Framing Assault that may be exploited to forge a file within the title of the sufferer and place it within the goal’s cloud storage, and
“Every person has a public RSA key utilized by different customers or MEGA to encrypt information for the proprietor, and a personal key utilized by the person themselves to decrypt information shared with them,” the researchers defined. “With this [GaP Bleichenbacher attack], MEGA can decrypt these RSA ciphertexts, albeit requiring an impractical variety of login makes an attempt.”
In a nutshell, the assaults could possibly be weaponized by MEGA or any entity controlling its core infrastructure to add lookalike recordsdata and decrypt all recordsdata and folders owned by or shared with the sufferer in addition to the chat messages exchanged.
The shortcomings are extreme as they undermine MEGA’s supposed safety ensures, prompting the corporate to difficulty updates to deal with the primary three of the 5 points. The fourth vulnerability associated to the breach of integrity is anticipated to be addressed in an upcoming launch.
As for the Bleichenbacher-style assault towards MEGA’s RSA encryption mechanism, the corporate famous the assault is “difficult to carry out in apply as it might require roughly 122,000 shopper interactions on common” and that it might take away the legacy code from all of its purchasers.
MEGA additional emphasised that it isn’t conscious of any person accounts that will have been compromised by the aforementioned assault strategies.
“The reported vulnerabilities would have required MEGA to grow to be a nasty actor towards sure of its customers, or in any other case may solely be exploited if one other social gathering compromised MEGA’s API servers or TLS connections with out being seen,” Ortmann identified.
“The assaults […] come up from sudden interactions between seemingly unbiased parts of MEGA’s cryptographic structure,” the researchers elaborated. “They trace on the problem of sustaining large-scale methods using cryptography, particularly when the system has an evolving set of options and is deployed throughout a number of platforms.”
“The assaults offered right here present that it’s attainable for a motivated social gathering to seek out and exploit vulnerabilities in actual world cryptographic architectures, with devastating outcomes for safety. It’s conceivable that methods on this class appeal to adversaries who’re prepared to take a position vital sources to compromise the service itself, rising the plausibility of high-complexity assaults.”