With 2022 coming to an in depth, there is no such thing as a higher time to buckle down and put together to face the safety challenges within the yr to return. This previous yr has seen its fair proportion of breaches, assaults, and leaks, forcing organizations to scramble to guard their SaaS stacks. March alone noticed three totally different breaches from Microsoft, Hubspot, and Okta.
With SaaS sprawl ever rising and turning into extra complicated, organizations can look to 4 areas inside their SaaS atmosphere to harden and safe.
Be taught how one can automate your SaaS stack safety
Misconfigurations Abound
Enterprises can have over 40 million knobs, examine containers, and toggles of their workers’ SaaS apps. The safety crew is accountable to safe every of those settings, person roles and permissions to make sure they adjust to business and firm coverage.
Not solely due to their apparent threat or misalignment with safety insurance policies, misconfigurations are overwhelmingly difficult to safe manually. These configurations can change with every replace, and their complexity is compounded by the various compliance business requirements. Including to that problem, SaaS app homeowners have a tendency to sit down in enterprise departments exterior the safety crew’s scope and should not educated or centered on the app’s safety.
Safety groups ought to onboard a SaaS Safety Posture Administration (SSPM) resolution, like Adaptive Protect, that gives full visibility and management throughout a crucial mass of SaaS apps within the SaaS stack. The answer should determine each international app settings and platform-specific configurations inside every app. Safety groups ought to have the ability to use the answer to achieve context into safety alerts and achieve solutions to questions like: Which customers are topic to a sure misconfiguration? Are they admins? Is their MFA enabled? By having these solutions at their fingertips, safety groups can implement firm and business insurance policies to remediate potential dangers from any misconfiguration.
SaaS-to-SaaS Entry
One other rising safety problem derives from the growing quantity of apps related to the corporate’s SaaS atmosphere. On common, 1000’s of apps are related with out the approval or information of the safety crew. Staff join these apps, usually to spice up productiveness, allow distant work and to raised construct and scale firm’s work processes.
Nevertheless, when connecting apps to their workspaces, workers are prompted to grant permissions for the app to entry. These permissions embody the flexibility to learn, create, replace, and delete company or private information, to not point out that the app itself could possibly be malicious. By clicking “settle for,” the permissions they grant can allow risk actors to achieve entry to helpful firm information. Customers are sometimes unaware of the importance of the permissions they’ve granted to those Third-party apps.
Falling within the Shadow IT area, safety groups should have the ability to uncover Third get together apps and determine which pose a threat. From entry scopes requested by these apps, to approved customers and cross referencing, the safety crew ought to have the ability to measure the extent of entry to delicate information throughout the group’s stack. An SSPM resolution like Adaptive Protect, can arm the safety crew with such a discovery and management along with offering superior reporting capabilities for efficient and correct threat assessments to drive actionable measures.
Get a demo of how an SSPM resolution will help mitigate Third-party app entry.
System-to-SaaS Person Danger
Safety groups should take care of threats from customers accessing their SaaS functions from private, unsecured units. Accessing a SaaS app through an unmanaged gadget poses a excessive degree of threat for a company, particularly when the gadget proprietor is a extremely privileged person. Private units are vulnerable to information theft and may inadvertently go on malware into the group’s atmosphere. Misplaced or stolen units may also present a gateway for criminals to entry the community.
Safety groups want an answer that permits them to handle SaaS dangers originating from compromised units. An SSPM resolution like Adaptive Protect can determine privileged customers reminiscent of admins and executives, calculate user-risk ranges, and acknowledge which endpoint units must be extra secured.
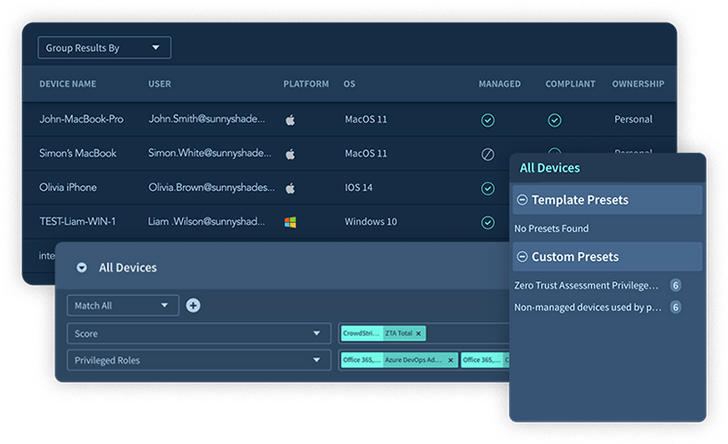 |
| Determine 1. Adaptive Protect’s System Stock |
Identification and Entry Governance
Each SaaS app person is a possible gateway for a risk actor, as seen in the newest Uber MFA Fatigue assault. Processes to make sure correct customers’ entry management and authentication settings are crucial, along with validation of role-based entry administration (versus individual-based entry) and establishing an understanding of entry governance. Identification and entry governance helps make sure that safety groups have full visibility and management of what’s taking place throughout all domains.
Safety groups want to observe all identities to make sure that person exercise meets their group’s safety pointers. IAM Governance permits the safety crew to behave upon arising points by offering fixed monitoring of the corporate’s SaaS Safety posture in addition to its implementation of entry management.
Ultimate Ideas
Gartner referred to as SaaS Safety Posture Administration (SSPM) within the “4 Should-Have Applied sciences That Made the Gartner Hype Cycle for Cloud Safety, 2021” for options that constantly assess safety threat and handle the SaaS functions’ safety posture. With an SSPM platform, like Adaptive Protect, organizations can harden their SaaS safety to determine and remediate points quicker and stop future assaults. Safety groups can introduce greatest practices for SaaS safety that stretch past Misconfiguration Administration to cowl SaaS-to-SaaS Entry, System-to-SaaS Person Danger ranges, and Identification & Entry Administration Governance.


