Whereas revealed developments in ransomware assaults have been contradictory — with some corporations monitoring extra incidents and different fewer — enterprise e-mail compromise (BEC) assaults proceed to have confirmed success towards organizations.
BEC circumstances, as a share of all incident-response circumstances, greater than doubled within the second quarter of the yr, to 34% from 17% within the first quarter of 2022. That is in response to Arctic Wolf’s “1H 2022 Incident Response Insights” report, revealed on Sept. 29, which discovered that particular industries — together with monetary, insurance coverage, enterprise providers, and legislation corporations, in addition to authorities businesses — skilled greater than double their earlier variety of circumstances, the corporate stated.
Total, the variety of BEC assaults encountered per e-mail field has grown by 84% within the first half of 2022, in response to knowledge from cybersecurity agency Irregular Safety.
In the meantime, to date this yr, menace studies launched by organizations have revealed contradictory developments for ransomware. Arctic Wolf and the Identification Theft Useful resource Middle (ITRC) have seen drops within the variety of profitable ransomware assaults, whereas enterprise clients appear to be encountering ransomware much less typically, in response to safety agency Trellix. On the similar time, community safety agency WatchGuard had a opposite take, noting that its detection of ransomware assaults skyrocketed 80% within the first quarter of 2022, in contrast with all of final yr.
The Gleam of BEC Outshines Ransomware
The surging state of BEC panorama is unsurprising, says Daniel Thanos, vice chairman of Arctic Wolf Labs, as a result of BEC assaults provide cybercriminals benefits over ransomware. Particularly, BEC positive aspects don’t depend on the worth of cryptocurrency, and assaults are sometimes extra profitable at escaping discover whereas in progress.
“Our analysis reveals that menace actors are sadly very opportunistic,” he says.
For that motive, BEC — which makes use of social engineering and inside techniques to steal funds from companies — continues to be a stronger income for cybercriminals. In 2021, BEC assaults accounted for 35%, or $2.4 billion, of the $6.9 billion in potential losses tracked by the FBI’s Web Crime Criticism Middle (IC3), whereas ransomware remained a small fraction (0.7%) of the entire.
By way of income from particular person assaults on companies, the Arctic Wolf evaluation famous that the median ransom for the primary quarter was about $450,000, however the analysis group didn’t present the typical loss for victims of BEC assaults.
Shifting Financially Motivated Cyber Techniques
Irregular Safety discovered in its menace report earlier this yr that that the overwhelming majority of all cybercrime incidents (81%) concerned exterior vulnerabilities in a number of extremely focused merchandise — specifically, Microsoft’s Alternate server and VMware’s Horizon virtual-desktop software program — in addition to poorly configured distant providers, corresponding to Microsoft’s Distant Desktop Protocol (RDP).
Unpatched variations of Microsoft Alternate particularly are susceptible to the ProxyShell exploit (and now the ProxyNotShell bugs), which makes use of three vulnerabilities to provide attackers administrative entry to an Alternate system. Whereas Microsoft patched the problems greater than a yr in the past, the corporate didn’t publicize the vulnerabilities till a number of months later.
VMware Horizon is a well-liked digital desktop and app product susceptible to the Log4Shell assault that exploited the notorious Log4j 2.0 vulnerabilities.
Each avenues are fueling BEC campaigns particularly, researchers have famous.
As well as, many cyber gangs are utilizing knowledge or credentials stolen from companies throughout ransomware assaults to gasoline BEC campaigns.
“As organizations and workers turn out to be extra conscious of 1 tactic, menace actors will regulate their methods in an effort to remain one step forward of e-mail safety platforms and safety consciousness coaching,” Irregular Safety stated earlier this yr. “The adjustments famous on this analysis are simply among the indicators that these shifts are already occurring, and organizations ought to count on to see extra sooner or later.”
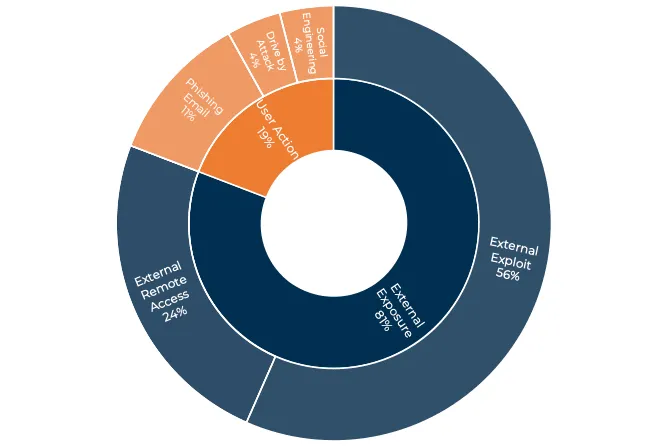
Social engineering is widespread, too, as ever. Whereas exterior assaults on vulnerabilities and misconfigurations are essentially the most prevalent method that attackers achieve entry to techniques, human customers and their credentials proceed to be a well-liked goal in BEC assaults, says Arctic Wolf’s Thanos.
“BEC circumstances are sometimes the results of social engineering, in comparison with ransomware circumstances, which are sometimes attributable to exploitation of unpatched vulnerabilities or distant entry instruments,” he says. “In our expertise, menace actors usually tend to assault an organization through distant exploit than dupe a human.
How one can Keep away from BEC Compromise
To keep away from being a sufferer, fundamental safety measures can go a good distance, Arctic Wolf discovered. In reality, many firms falling prey to BEC assaults didn’t have safety controls that probably might have prevented harm, the corporate acknowledged in its evaluation.
For example, the analysis discovered that 80% of these firms struggling a BEC incident had no multifactor authentication in place. As well as, different controls, corresponding to community segmentation and safety consciousness coaching, might assist forestall BEC assaults from being pricey, even after the attacker efficiently compromises an exterior system.
“Corporations ought to strengthen their worker defenses via safety coaching,” Thanos says, “however in addition they want to handle the vulnerabilities that menace actors give attention to.”


