The takedown resulted from a worldwide legislation enforcement operation involving eleven nations, headed by Europol’s European Cybercrime Middle.
The European Cybercrime Middle/EC3 of Europol and legislation enforcement companies from eleven nations launched a joint operation to take down FluBot spyware and adware. The investigation concerned Australia, Finland, Belgium, Spain, Eire, Hungary, Sweden, the Netherlands, Switzerland, and the USA legislation enforcement authorities whereas EC3 coordinated the operation.
Eire’s Garda Nationwide Cyber Crime Bureau (GNCCB) was a part of the investigation workforce. GNCCB Detective Superintendent Pat Ryan acknowledged that “the investigation is ongoing to establish the people behind this world malware marketing campaign.”
Particulars of the Operation
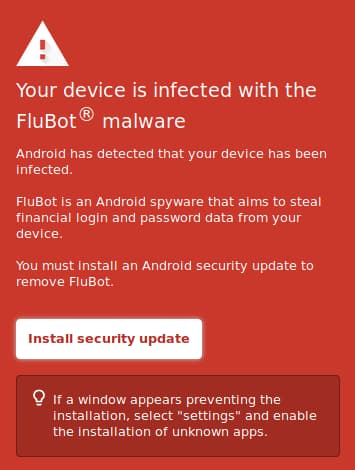
In a weblog submit, Europol defined that the FluBot Android malware was distributed via SMS and was able to stealing on-line banking credentials, passwords, and different delicate information. Therefore, an in depth investigation was launched since FluBot spyware and adware focused Android smartphones throughout Australia, Europe, and different components of the world.
Authorities famous that its distribution scope was widening shortly. Now the spyware and adware is below the management of Dutch Police/Politie, which carried out the operation in Could, rendering the malware pressure inactive.
About FluBot
FluBot malware is distributed as an utility, making it tough to detect it. The malware will get put in on the Android smartphone via textual content messages. The consumer is requested to click on on a hyperlink and set up an app for monitoring a bundle supply or entry a pretend voice mail message.
After the app is put in, it asks for accessibility permissions. The malware operators use the entry to steal delicate information from the smartphone, together with banking app login particulars and cryptocurrency pockets credentials. It may additionally successfully disable the cell phone’s built-in safety mechanisms.
Moreover, it doesn’t open when the consumer faucets on the app icon, and an error message seems when the consumer tries to uninstall it. The infamous malware was detected in 2021 when it contaminated many units in Spain and Finland.
In accordance with Interpol, FluBot was excessively virulent. It could possibly be multiplicated routinely by forwarding the SMS message to the contaminated smartphone’s contact listing. To keep away from an infection, smartphone customers ought to instantly reset their telephones on manufacturing unit settings in the event that they imagine a malicious app was downloaded on the gadget.
Extra Associated Information
- Microsoft takes down largest botnet community “Necurs”
- World’s Most ‘Resilient Malware’ Botnet Emotet Taken Down
- Authorities take down rip-off marketing campaign impersonating the WHO
- Dutch Police takes down 15 DDoS-for-hire providers in a single week
- Europol takes down VPN service VPNLab utilized by ransomware operators