On this digital period, on-line threats are booming as a lot because the web person base. Generally, malware infects gadgets because of vulnerabilities unknown to individuals. Nonetheless, it often comes as a direct consequence of customers’ actions. As an illustration, getting into that suspicious web site promising unique content material or software program free of charge. Talking of human error, one of the crucial standard methods utilized by hackers is pretend updates.
However what are pretend updates? These are malicious software program downloads masquerading as legit updates. Any such malware is usually used to contaminate gadgets with ransomware. The latest growth in that is Vidar Malware. What are its dangers, and tips on how to comprise them?
What’s Vidar malware?
The latest pretend replace was found impersonating a Home windows 11 obtain portal. These portals in the end triggered a Vidar malware an infection. The identical malware was discovered to be spreading via the pretend InterVPN web site.
Vidar is a form of info-stealing malware that could be utilized to watch customers. This malicious software program can steal login credentials, take screenshots, financial institution particulars, and many others. Moreover common information stealing, Vidar was additionally found downloading and executing further malware payloads. Furthermore, the malware deletes itself from the system after finishing its work.
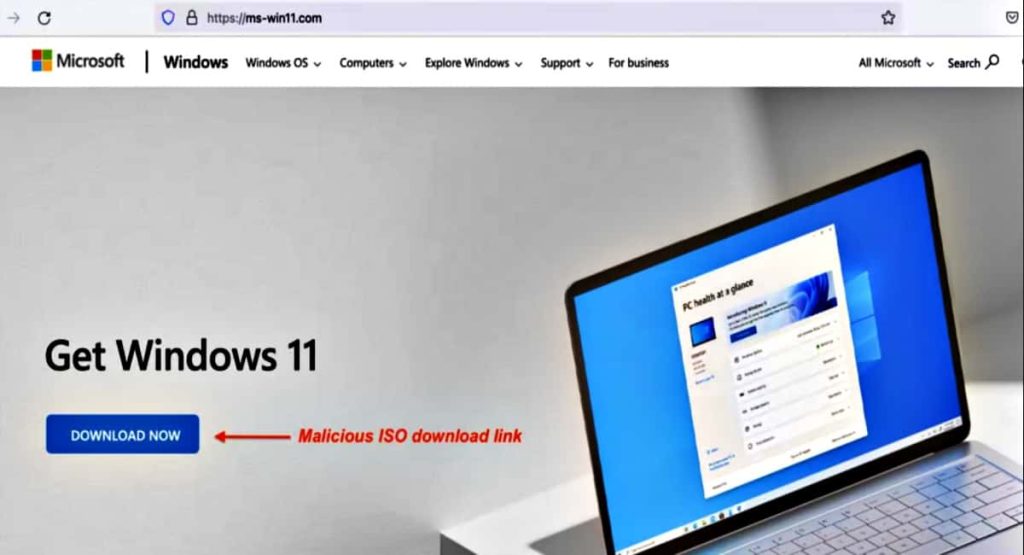
How does Vidar work?
It’s being unfold throughout the web utilizing phishing, fallout exploit package, and pay-per-install PrivateLoader dropper. The e-mail comprises an attachment as a .iso disk picture, which is misleadingly known as “request.doc.” This ISO is principally composed of two information: an executable (app.exe) and a Microsoft Compiled HTML Assist (CHM) file (pss10r.chm).
Right here’s the way it enters the methods: When a infamous CHM file is loaded, a JavaScript snippet executes the app.exe. The second stage downloads and decodes the Vidar malware, which is then carried out on the system.
Then, the Vidar samples talk with their C2 server by way of Mastodon and Telegram. After profitable communication, person profile bio sections are examined, and C2 addresses are extracted from the profiles. The malware is then copied to the goal system, the place it units up its configuration and begins accumulating person information.
So, that is the way it hides its presence in your system. However tips on how to save our gadgets from such assaults?
Learn how to defend your self?
Now that you know the way to establish pretend updates, it’s time to take measures to guard your self. Listed here are some ideas:
Use a firewall
This safety system helps display screen out incoming and outgoing community site visitors. Good firewalls can typically stop malware from contacting the Command & Management server. It’s how ransomware works – it must contact the C&C server to get a key that may encrypt your information. If it could possibly’t attain the C&C server, it could possibly’t get the important thing and thus can’t do any hurt.
Shield web connection
Your laptop is barely part of the protection technique you could make use of. Malware can exploit many vulnerabilities, together with unsecured networks. Fortunately, you’ll be able to assure that every community you connect with is protected.
All it takes is establishing a VPN for Home windows in your laptop computer and enabling it everytime you use it outdoors the house. Public Wi-Fi could be extraordinarily harmful: outsiders can snoop in your actions or use safety loopholes to contaminate your system. Due to this fact, keep in mind by no means to attach your gadgets, be it a Home windows laptop computer or an Android smartphone, to free Wi-Fi with out a VPN.
Change your replace settings
We regularly have our replace settings on auto-update. It’s going to set up itself as quickly as an replace is obtainable. This feature ought to be most popular because it ensures you’ll be able to have a PC working the newest working system. If you don’t schedule automated updates, chances are you’ll delay updates indefinitely.
Say no to piracy
Free software program and video games could be tempting however could be a supply of cyberattacks. Due to this fact, use solely licensed software program. This fashion, you can be certain that your updates are from a trusted supply. Moreover, steer clear of alleged unique affords for applications on random web sites.
Set up an antivirus
An antivirus program will scan all incoming and outgoing information for a malicious exercise like ransomware or adware. If it detects something suspicious, it can alert customers and advocate elimination. In fact, it’s important to get a trusted antivirus program. Many pretend antivirus applications may warn you about pretend threats as a result of they want you to purchase premium variations.
So, even should you by chance click on on a pretend replace, the antivirus will maintain it. Set up updates solely from official web sites. It’s the most secure approach to make sure that the replace is legit. In case you ever come throughout any pop-ups that look legit, don’t click on on them. It’s best to counter-check the replace on the official web site after which obtain it from there.
At all times preserve your system up to date
The easiest way to know whether or not any replace is pretend is to maintain your system updated. Any surprising replace now might be fairly suspicious. Furthermore, updates typically comprise safety patches that repair vulnerabilities in your system. So, it’s at all times a good suggestion to maintain your system up to date.
Backup your information
That is extra of a precautionary measure than the rest. By backing up your information, you make sure that you gained’t lose any necessary information even when your system will get contaminated with ransomware. Many cloud storage choices can be found as of late that provide good safety and are inexpensive.
Conclusion
Other than these precautions, it’s important to observe protected browsing to keep away from these threats from detecting your system.


