MIT Pc Science and Synthetic Intelligence Laboratory (CSAIL) researchers say they’ve found an unpatchable vulnerability affecting Apple’s customized Arm-based M1 silicon on the chip’s final stage of protection. Since it isn’t doable to patch out the flaw, are homeowners of
M1 systems sitting geese? Not essentially.
Observe that this does not have an effect on all Arm processors. Apple’s M1 SoC is the primary desktop processor to help Arm Pointer Authentication, which is a
safety mechanism that verifies software program utilizing a cryptographic hash known as Pointer Authentication Code (PAC). Based on the researchers, different corporations together with Samsung and Qualcomm have both introduced or are anticipated to ship new chips supporting Pointer Authentication, however to date solely
Apple has performed so.
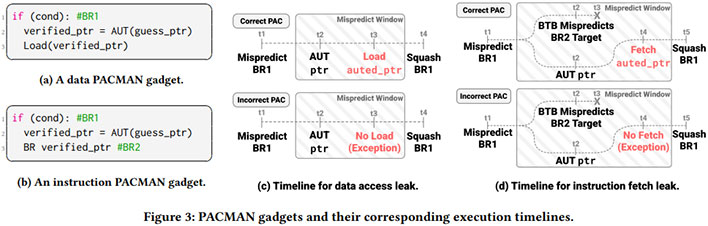
They might need to rethink these plans. In a not too long ago printed paper, the researchers contend it’s doable to leverage speculative execution assaults to bypass this safety mechanism. These kind of assaults, which they’ve dubbed “PACMAN,” are considerably paying homage to
Spectre and Meltdown.
“On this paper, we suggest the PACMAN assault, which extends speculative execution assaults to bypass Pointer
Authentication by establishing a PAC oracle. Given a pointer in
a sufferer execution context, a PAC oracle can be utilized to exactly
distinguish between an accurate PAC and an incorrect one with out
inflicting any crashes,” the researchers state of their paper.
Sadly, bypassing this final stage of protection would give an attacker unauthorized entry on the kernel stage, at which level they may just about “do no matter they’d like on a tool.” That is not good, clearly. The researchers say they developed a number of proof of ideas that accomplish this very factor. They have not examined it on Apple’s new
M2 chip, although, so it is unclear if it is susceptible to PACMAN assaults.
Is it sport over for M1-based MacBook homeowners, although? Not essentially. There are studies that bodily entry to a machine is required, although the parents at Tom’s {Hardware} say they have been instructed a distant assault is feasible as nicely.
There are different components which have to return in play, although, together with the presence of an current reminiscence bug. Apple additionally downplayed the safety danger in a press release.
“We need to thank the researchers for his or her collaboration as this proof of idea advances our understanding of those strategies. Based mostly on our evaluation in addition to the main points shared with us by the researchers, now we have concluded this subject doesn’t pose an instantaneous danger to our customers and is inadequate to bypass working system safety protections by itself,” Apple stated.
However, the researchers say their findings have vital implications for designers contemplating implementing Pointer Authentication in future merchandise.