Endpoint gadgets like desktops, laptops, and cellphones allow customers to connect with enterprise networks and use their sources for his or her day-to-day work. Nonetheless, in addition they increase the assault floor and make the organisation weak to malicious cyberattacks and information breaches.
Why Fashionable Organisations Want EDR
In response to the 2020 world danger report by Ponemon Institute, smartphones, laptops, cellular gadgets, and desktops are among the most weak entry factors that enable risk actors to compromise enterprise networks. Safety groups should assess and tackle the safety dangers created by these gadgets earlier than they will injury the organisation. And for this, they require Endpoint Detection & Response (EDR).
EDR options present real-time visibility into endpoints and detect threats like malware and ransomware. By repeatedly monitoring endpoints, they permit safety groups to uncover malicious actions, examine threats, and provoke acceptable responses to guard the organisation.
The Limitations of EDR
Fashionable enterprise networks are advanced webs of customers, endpoints, purposes, and information flows distributed throughout on-premises and multi-cloud environments. As EDR options solely present visibility into endpoints, many safety gaps and challenges stay, considerably rising the danger of cyberattacks going unnoticed.
- Malware disabling/abusing EDR brokers: The emergence of refined hacker teams like Lapsus$ is one other danger that EDR instruments cannot take care of. In late 2021, Lapsus$ hacked into a number of massive firms by compromising distant endpoints and turning off their EDR instruments. They have been thus in a position to disguise their malicious behaviour on the contaminated endpoints and obtain their purpose of stealing delicate firm information. One other downside is that risk actors can abuse the “hooking” approach that EDRs use to observe operating processes. This system permits EDR instruments to observe packages, detect suspicious actions, and collect information for behaviour-based analytics. Nonetheless, this identical course of permits attackers to entry a distant endpoint and import malware.
- BYOD: Lately, many organisations have shifted to distant work fashions that enable workers and third-party customers to entry enterprise sources through distant networks and unsecured cellular gadgets. These gadgets are exterior the management of safety groups and their EDR instruments. Consequently, their safety options can’t sustain with all these endpoints, a lot much less shield them or the enterprise community from malicious assaults.
- Unsupported gadgets: Additionally, not each linked endpoint can assist EDR brokers. That is true for legacy endpoints like routers and switches, in addition to newer IoT gadgets. Additional, with linked Supervisory Management and Knowledge Acquisition (SCADA) and Industrial Management System (ICS) environments, some endpoints could also be exterior the organisation’s management and thus exterior the EDR’s safety perimeter. Consequently, these endpoints and programs stay weak to threats like malware, DDoS assaults, and crypto mining.
- Sustaining/deploying EDR: Lastly, with agent primarily based EDR merchandise, it may be an enormous burden for safety groups to put in and keep brokers on each endpoint throughout the enterprise community atmosphere.
Closing EDR’s Safety Gaps with Community Visibility and NDR
One of the crucial efficient methods to shut the safety gaps highlighted above is by including Community Detection and Response (NDR) to the enterprise cybersecurity stack for the next causes:
- Can’t disable NDR: As a log information primarily based NDR similar to ExeonTrace collects information from a number of totally different information sources within the community (and doesn’t depend on particular gadgets), the detection algorithms can’t be circumvented. Due to this fact, even when an EDR is disabled by malware, the NDR will detect it.
- Identification of shadow IT: An NDR resolution not solely permits to observe the community site visitors between recognized community gadgets but additionally identifies and screens but unknown gadgets and networks. And naturally, additionally endpoints with out EDR brokers are included within the community analytics (similar to BYOD).
- Misconfigured firewalls and gateways: Unproper configured firewalls and gateways will be entry doorways for attackers – an NDR permits for detection earlier than exploitation.
- Tamper-proof information assortment: Community-based information assortment is extra tamper-proof than agent-based information; very best for digital forensics required by regulators.
- Full visibility of the entire community: As no brokers are required, an NDR resolution similar to ExeonTrace permits for full visibility of all community connections and information flows. It thus supplies larger visibility throughout all the enterprise community and any potential threats throughout it.
Conclusion
As organisations grow to be more and more advanced and add extra end-user gadgets to their networks, they require a dependable monitoring resolution to guard their endpoints from potential threats. Nonetheless, Endpoint Detection and Response (EDR) supplies such endpoint safety solely to a sure extent. There are quite a few drawbacks of EDR that enable refined cybercriminals to surpass their safety perimeter and exploit community vulnerabilities.
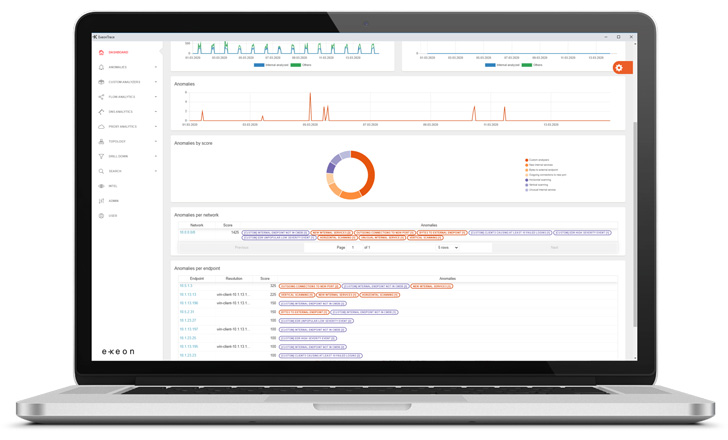 |
| ExeonTrace Platform: Screenshot of Dashboard |
To fill the safety gaps left by EDR options, organisations should reinforce their safety defences. Community Detection and Response (NDR) options like ExeonTrace are a dependable and confirmed strategy to monitor community site visitors and thus full enterprise cybersecurity stacks. As EDR and NDR options are complementary, their mixed detection capabilities can successfully shield organisations from refined cyberattacks.
E-book a free demo to find how ExeonTrace may also help tackle your safety challenges and make your organisation extra cyber resilient.