It is not a brand new idea that Workplace 365, Salesforce, Slack, Google Workspace or Zoom, and so forth., are superb for enabling the hybrid workforce and hyper-productivity in companies immediately. Nonetheless, there are three important challenges which have arisen stemming from this evolution: (1) Whereas SaaS apps embrace a number of native safety settings, they have to be hardened by the safety crew of the group. (2) Workers are granting third get together app entry to core SaaS apps that pose potential threats to the corporate. (3) These SaaS apps are accessed by completely different units with out their machine hygiene rating even being checked.
1 — Misconfiguration Administration
It is not a simple job to have each app setting correctly configured — always. The problem lies inside how burdensome this accountability is — every app has tens or a whole bunch of safety settings to configure, along with hundreds of person roles and permission in a typical enterprise, compounded by the various compliance trade requirements and frameworks that organizations attempt to comply with.
The complexity of securing SaaS apps is simply elevated by the truth that usually the SaaS app proprietor sits outdoors the safety crew, within the division that almost all makes use of the app (assume Gross sales has CRM app, Advertising has automation app) — and they’re untrained and never centered on the safety maintenance of the app. All of it quantities to only how burdensome and unrealistic it’s to anticipate safety groups to have the ability to keep in charge of the group’s SaaS stack.
2 — third Occasion App Entry
OAuth 2.0 has enormously simplified authentication and authorization and provides a fine-grained delegation of entry rights. Represented within the type of scopes, an software asks for the person’s authorization for particular permissions. An app can request a number of scopes. By way of the approval of the scopes, the person grants these apps permissions to execute code to carry out logic behind the scenes inside their surroundings. These apps may be innocent or as threatening as an executable file.
Relating to native machines and executable recordsdata, organizations have already got management built-in that allows safety groups to dam problematic applications and recordsdata. It must be the identical relating to SaaS apps.
3 — Gadget-to-SaaS-Consumer Posture
From the primary entry by means of to the machine posture, safety groups want to have the ability to establish and handle the dangers coming from SaaS customers and their related units. A tool with a low hygiene rating poses a excessive danger relying on which apps this worker is utilizing. Within the case of a extremely privileged person, an unsecured machine can pose a fair larger stage of danger for a corporation. The safety crew wants the flexibility to correlate SaaS app customers, their roles, and permissions with their related units’ compliance and integrity ranges. This end-to-end strategy permits a holistic zero-trust strategy to SaaS safety that’s solely now coming into the image.
SaaS Safety Posture Administration Handles the SaaS Stack Challenges
That is why Gartner named SaaS Safety Posture Administration (SSPM) a MUST HAVE answer to constantly assess safety dangers and handle the SaaS functions’ safety posture within the “4 Should-Have Applied sciences That Made the Gartner Hype Cycle for Cloud Safety, 2021.” Different cloud options do not provide preventative protection. For instance, a CASB answer is event-driven; CASB will alert the group to a SaaS leak or breach solely as soon as it has occurred.
An SSPM answer, like Adaptive Defend, comes into play to allow safety groups to establish, analyze, and prioritize misconfigurations in addition to present visibility to third get together apps with entry to their core apps and Gadget-to-SaaS-Consumer posture administration.
Click on right here to schedule a 15-minute demo of Adaptive Defend’s SSPM answer.
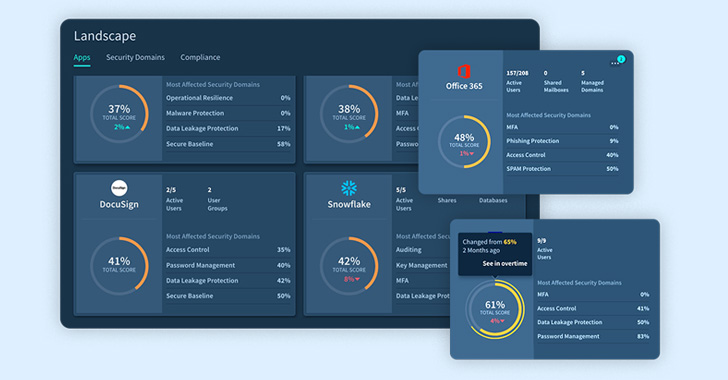
Adaptive Defend permits you to filter and slice the info by app, area, and compliance frameworks.
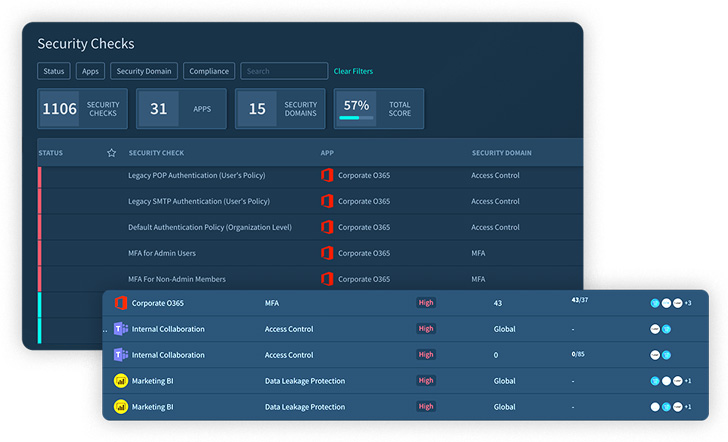
The core of the answer is the detailed and granular safety checks being constantly carried out throughout the SaaS stack, whereas safety groups can handle misconfigurations instantly or create a ticket that integrates with any ticketing system:
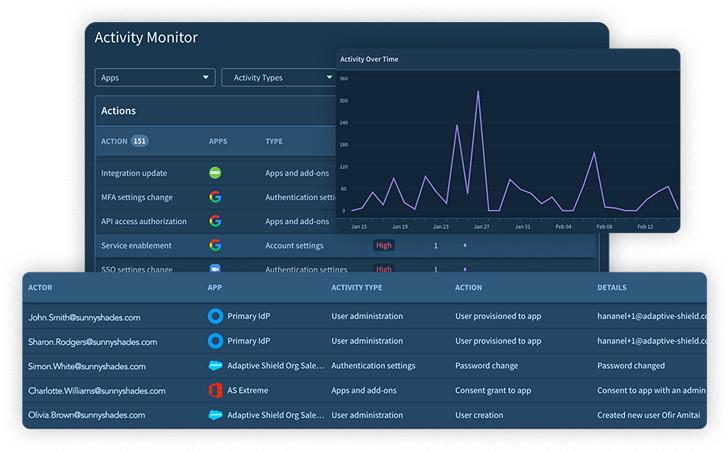
By way of the Exercise Monitoring function, Adaptive Defend displays the actions of privileged customers:
Click on right here to schedule a 15-minute demo to see all options and functionalities.