ACM.63 Implement the existence of VPC Stream Logs on All VPCs
This can be a continuation of my sequence of posts on Automating Cybersecurity Metrics.
Governance by means of Automation
We’ve already began how we are able to implement finest practices by means of using automation on this sequence. Nevertheless, there could also be methods across the governance because it might be too simple for somebody to alter the code. I’ll handle that later.
Right here’s one other factor we are able to automate. An AWS safety finest follow is to activate VPC Stream Logs for each VPC you create. We are able to make sure that occurs by incorporating that into our VPC deployment template.
As I simply talked about, the one caveat is that it’s a must to guarantee all VPCs are created along with your licensed template. For now assume your staff are all on good conduct and so they solely use the templates and code you may have outlined for deployments.
There are another instruments you should utilize for governance which I could handle sooner or later however the base start line is to get the code proper from the beginning, not discover it after it’s been deployed and is much more time consuming and costly to alter as a result of numerous issues have been deployed on high of it. So I’m beginning with what try to be beginning with — creating assets by means of code that adhere to your safety insurance policies.
Why you want community logs
I may give you a state of affairs as to why this issues. One time somebody requested me to have a look at his AWS account as a result of one in every of his hosts received ransomware on it. After I logged in, I might see that he arrange his networking guidelines incorrectly. Though he had opened a sure port, he additionally left a default rule within the community guidelines that allowed all site visitors on any port. Not solely that, logging was not enabled on any of this networking.
The implications of which can be that initially, there aren’t any longs to have a look at what connections had been produced from the place to carry out this assault from a community perspective. As well as there can be zero rejected site visitors so there can be a ton of noise within the logs. Moreover, it was a flat community to a site controller kind server with no bastion host, VPN, and so on. Fortunately it was solely to guage a demo product in a stand-alone account, so no actually hurt carried out.
By the best way, after I received on the host, it was tremendous simple to bypass the ransomware and work out they had been utilizing XMRig. I later had the identical ideas I used launched in a complicated penetration testing class and though among the ideas in that class had been very superior, that specific matter was not. I discovered that the attacker had turned off the host-based firewall. Attackers can flip off host-based controls once they get onto a bunch, however they’ll’t flip off your community logs with host-only entry (except they get onto a bunch with entry to alter your community guidelines).
I used to be capable of glean some data from the host however lack of community logs made it troublesome to find out the supply of the assault or which ports and protocols the attacker used, to not point out higher guidelines would have prevented the assault altogether.
Should you monitor your community logs for anomalous exercise, you might can spot an intrusion makes an attempt earlier than the attacker succeeds. Chances are you’ll want further particulars past what exists in VPC Stream Logs for low-level community assaults however they may help typically. You possibly can even auto-block nefarious IP addresses on a everlasting foundation once you see a malformed request that’s clearly looking for a gap in your defenses.
Not solely that, VPC stream logs are invaluable for troubleshooting community errors. When you may’t hook up with one thing, you’ll be capable to search for rejects in VPC Stream Logs to pinpoint the issue. (More often than not…consult with my publish on Lambda networking.)
Stream Logs
Community admins will likely be accustomed to the idea of netflow logs. VPC Stream Logs are related.
In my lessons, I present individuals learn how to use VPC Stream Logs and why they’re vital. For now, we simply wish to make certain they’re created for each VPC.
Stream Log Stipulations
There are some things we’ll have to create earlier than we are able to deploy Stream Logs which we are able to see within the documentation:

DeliverLogsPermissionArn: The identify of this parameter ought to actually be extra constant like FlowLogsRole.
LogDestination: We wish to ship our Stream Logs to CloudWatch so we’ll have to create a CloudWatch Log Group.
LogDestinationType: We’re utilizing the default so we don’t need to set this. Some individuals discover S3 buckets cheaper for storing logs however then you definately want to have the ability to parse out and search by means of the information shortly within the occasion of an incident or for troubleshooting. Make sure that you are able to do that. You’ll most likely wish to encrypt your logs and ensure to configure the S3 bucket accurately — one thing we haven’t coated but.
LogGroupName: Neither Log Vacation spot nor Log Group Identify is required and it doesn’t say whether or not it’s a must to set one or the opposite or each. However, once you attempt to set each you get this error so we solely want one or the opposite. The documentation might be clearer.
Useful resource handler returned message: "Please solely present LogGroupName or solely present LogDestination.
ResourceID: We are able to reference our VPC in the identical template.
ResourceType: VPC
TrafficType: Legitimate values are ACCEPT | REJECT | ALL. We would like ALL. You possibly can inform if somebody is making an attempt to interrupt in by rejects. You possibly can see who’s made a profitable connection and if something appears anomalous by need was accepted. We would like all.
We are able to skip the others for now.
VPC Stream Logs Function
Typically to allow providers in AWS we have to create a job and provides the service permission to take actions in our account. Earlier than we add FlowLogs to the VPC template we have to create a job.

Can we use one in every of our present position templates? Probably not as a result of the belief coverage is totally different. But it surely does look fairly just like our Lambda position aside from the service identify.
As a substitute of rewriting a brand new position for each service let’s alter our Lambda position to work for all AWS providers, beginning with the 2 we’re presently utilizing: Lambda and VPC Stream Logs.

We’re utilizing a map within the above template the best way I described on this publish to set the service within the belief coverage primarily based on the service identify handed into the template.
Add a name to the brand new operate to the deployment script for the VPC stream logs position. The calls to deploy the lambda operate roles ought to nonetheless work.

Run the deployment script:
./deploy.sh
With a purpose to re-deploy the Lambda operate roles we’ll need to delete and redeploy the Lambda features and insurance policies after which re-deploy them. Whereas we’re at it we’ll utterly delete the Lambda roles and begin over. This is among the caveats of adjusting roles after you’re far alongside into growth and why it’s a good suggestion to assume by means of your organizational deployment construction prematurely — and check it!
After working the deployment script:
- Verify the CloudFormation stacks for errors
- Verify that your roles exist in IAM with the right names
Deploy the Stream Logs Coverage
Now we have to create and deploy the Stream Logs coverage proven above. Observe that we’re specifying the position we simply created for the Roles property.

We are able to use our present operate to deploy a job for a coverage. Add the next traces to the deploy script:

Deploy the coverage and confirm it exists on the position we simply created.
Create a CloudWatch Log Group
Subsequent we have to create our CloudWatch log group. CloudWatch is sort of a log aggregation supply in AWS the place all logs might be despatched. That features software logs and nearly any sort of logs that you can imagine in AWS. You create a log group after which you may ship your logs to it.
We’re going to make use of CloudFormation once more to create our log group:
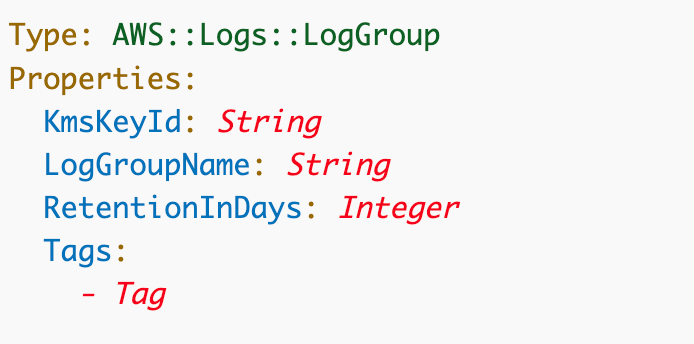
Add the LogGroup useful resource to the VPC template we’ve been engaged on.
I’m not going so as to add a KMS key simply but. We’ll want a reputation and we’ll set the retention to 30 days. Most organizations would wish to retailer logs longer — maybe 90 days or ideally a yr.
Typically attackers exist in environments lengthy earlier than they’re recognized so extra logs are useful. We’re simply making a POC right here so don’t need an excessive amount of expense. One of many points I’m having with AWS ControlTower proper now as a small enterprise is the price of all of the logs. They will add up. You may also archive your logs to save cash however I’m unsure I’ll get to that on this sequence. I have to revisit that myself.
Deploy the VPC once more to verify the log group creation code is OK.

At this level we get an error saying our NetworkAmin position doesn’t have permission to create a log group so we have to repair this:
Useful resource handler returned message: "Consumer: arn:aws:sts::xxxxx:assumed-role/NetworkAdminsGroup/botocore-session-xxxx just isn't licensed to carry out: logs:CreateLogGroup on useful resource: arn:aws:logs:xxxxx:xxxxx:log-group:RemoteAccessPublicVPCLogGroup:log-stream: as a result of no identity-based coverage permits the logs:CreateLogGroup motion (Service: CloudWatchLogs, Standing Code: 400, Request ID: xxxxx)" (RequestToken: xxxxx, HandlerErrorCode: GeneralServiceException)
We additionally want: logs:PutRetentionPolicy and logs:DescribeLogGroups
Head over the NetworkAdmin position coverage and add these permissions like we’ve carried out in prior posts. Deploy the position coverage once more after which attempt to deploy the VPC once more.
Add VPC Stream Log Useful resource to The VPC Template
Now that we now have a job and a log group we are able to add VPC Stream logs to the VPC template.

Whereas deploying Stream logs I received this pretty error message:
Should you get an encoded error message on AWS decode it like this:
aws sts decode-authorization-message — encoded-message encoded-message
The message I received again didn’t make a complete lot of sense however I can glean from it that I most likely want so as to add the iam:PassRole permission for the actual position under to my NetworkAdmin permissions. I actually hope AWS fixes this error message…it’s simply time consuming to need to cope with this.
"DecodedMessage": "{"allowed":false,"explicitDeny":false,"matchedStatements":{"gadgets":[]},"failures":{"gadgets":[]},"context":{"principal":{"id":"AROAZ7U3253AOWN23LBU6:botocore-session-xxx","arn":"arn:aws:sts::xxxx:assumed-role/NetworkAdminsGroup/botocore-session-xxx"},"motion":"iam:PassRole","useful resource":"arn:aws:iam::xxx:position/VPCFlowLogsRole","circumstances":{"gadgets":[{"key":"aws:Region","values":{"items":[{"value":"global"}]}},{"key":"aws:Service","values":{"gadgets":[{"value":"iam"}]}},{"key":"aws:Useful resource","values":{"gadgets":[{"value":"role/VPCFlowLogsRole"}]}},{"key":"iam:RoleName","values":{"gadgets":[{"value":"VPCFlowLogsRole"}]}},{"key":"aws:Account","values":{"gadgets":[{"value":"xxx"}]}},{"key":"aws:Sort","values":{"gadgets":[{"value":"role"}]}},{"key":"aws:ARN","values":{"gadgets":[{"value":"arn:aws:iam::xxx:role/VPCFlowLogsRole"}]}}]}}}"}
After including that final permission and just for that particular position (as talked about earlier than the iam:PassRole permission might be problematic if not particular) Stream Logs deployed efficiently.
Now we now have efficiently put in Stream Logs on our VPCs and they’ll get created for any new VPCs we create utilizing this template.
Teri Radichel
Should you preferred this story please clap and comply with:
Medium: Teri Radichel or E mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts


