 A part of a six-month assault, e-mail accounts on the NHS’ Microsoft 365 occasion had been compromised, leading to over 1,100 focused e-mail assaults used to acquire extra credentials.
A part of a six-month assault, e-mail accounts on the NHS’ Microsoft 365 occasion had been compromised, leading to over 1,100 focused e-mail assaults used to acquire extra credentials.
In accordance with safety researchers at e-mail safety vendor Inky, the 139 compromised NHS accounts had been being misused from October 2021 till March of 2022 because the cornerstone of additional phishing assaults tried to both harvest credentials to main on-line platforms, or to trick victims into offering banking particulars.
Emails had been possible despatched utilizing two IP addresses serving as SMTP relays for the NHS’ 27,000+ customers, permitting attackers to work remotely. What could have allowed this assault to stay undetected for six months was the variety of emails being despatched:
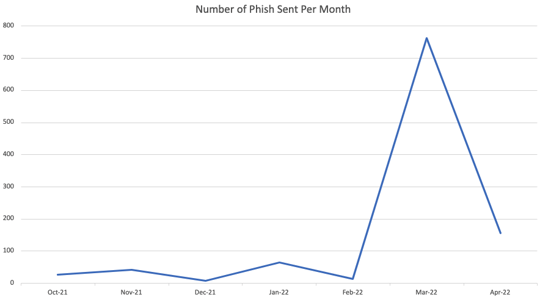
You’ll word the dramatic spike within the variety of emails despatched in March of this yr, possible drawing consideration to the assault.
Emails impersonated each the NHS and people inside, utilizing NHS e-mail footers, and names of compromised people so as to add credibility to the scams.
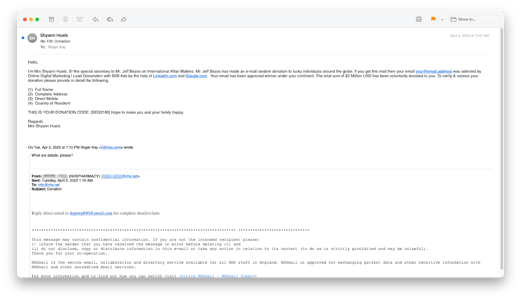
Whereas there have been solely 139 compromised e-mail accounts (out of over 27,000, in line with the NHS), it actually solely takes a single phishing e-mail to change the course of a person or a company. As a result of most phishing scams must get the sufferer to deal with one response motion (e.g., clicking a hyperlink or opening an attachment), the scams can usually be recognized fairly simply, if the person is vigilant.
And this vigilance comes with training by means of Safety Consciousness Coaching designed to assist customers perceive the character of phishing assaults, social engineering strategies, and the position they play in company cybersecurity.


