ACM.33 Limiting the Confused Deputy Assault in IAM Insurance policies
This can be a continuation of my collection on Automating Cybersecurity Metrics.
Within the put up on the confused deputy drawback I referred to the IAM documentation that explains the way to restrict the flexibility for a person to imagine a job with a IAM Coverage like this:
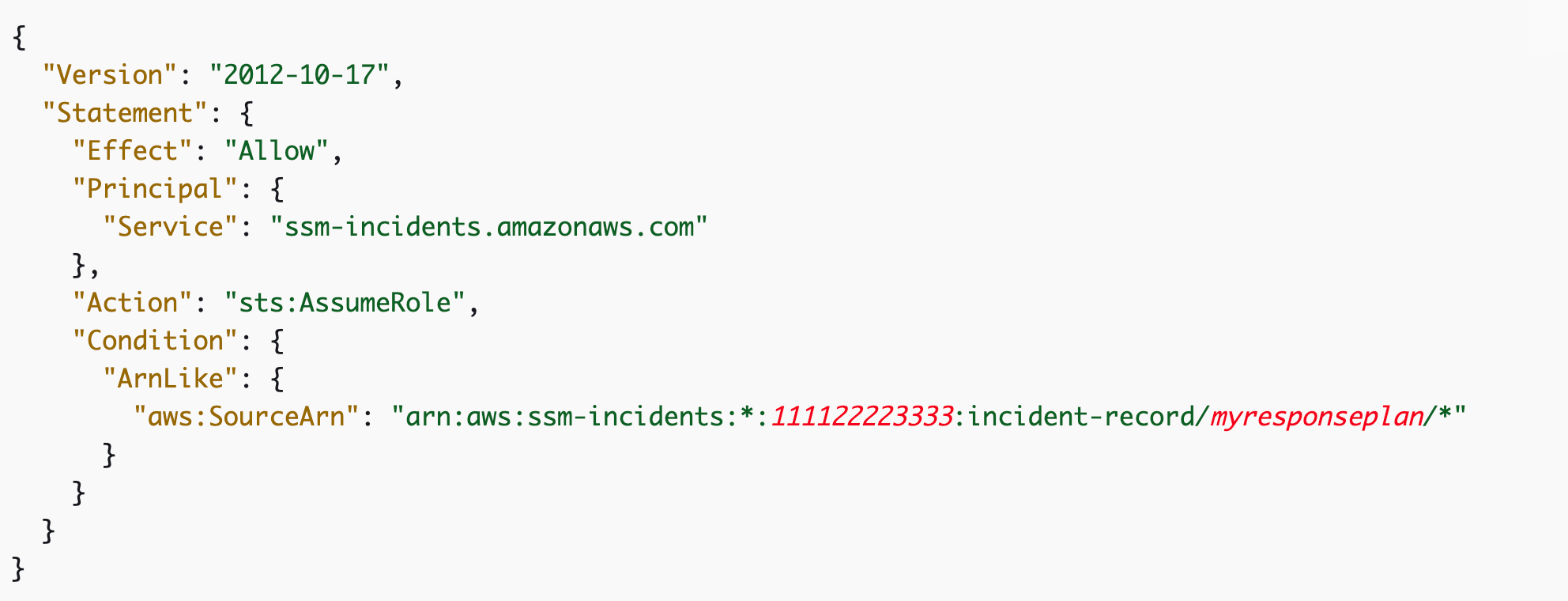
Recall that an IAM Coverage locations restrictions on an identification versus a useful resource or function assumption as I defined right here:
Let’s overview the coverage for our IAM Admin person that we created earlier. Navigate to the IAM console and seek for your IAM Admin are overview permissions. Discover that now we have allowed the IAM person to imagine a job that begins with the identify BatchRole.

Query:
That is applied with no situation like the instance above. This coverage as an alternative whitelists the function sources the person can assume. Does it work?
Run the script within the root listing yet another time.
When the script asks me for a code to imagine the function it does fail with an unauthorized message:

Why didn’t we get the unauthorized message after we examined the primary time? Possibly I missed it. It additionally could possibly be that the belief coverage had not utterly up to date by the point the batch job check ran. As I discussed, IAM is finally constant, that means it doesn’t lock out customers whereas making modifications. AWS will implement the brand new coverage because the change will get pushed out to all methods.
Let’s replace our IAM coverage to make use of the brand new prefix for IAM roles.
Our IAM administrator coverage exists at:
iam/iam_admins/cfn/coverage.yaml
Change this:

To this:

Deploy the change by executing the deploy script discovered right here:
iam/iam_admins/deploy.sh
like this:
./deploy.sh
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Discover how straightforward it was to deploy one change in comparison with an enormous monolithic CloudFormation template. You’ll have seen such templates elsewhere. Don’t do it. Assume forward and construct your CloudFormation templates so you possibly can change and check particular person sources simply.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Now in case you have been to attempt to check the script once more you’ll nonetheless get an error.
./check.sh
That’s as a result of the function BatchRoleDeployBatchJobCredentials now not exists and that’s what now we have configured the AWS CLI to make use of as defined in these two posts:
Head over to IAM and seek for the function:

Now simply seek for Deploy:

Our function has been renamed to start out with IAM as anticipated. Edit your AWS config file as defined within the posts above to make use of this function as an alternative of the outdated batch job function.
Now I can assume the function.
This proves that our model of an IAM Coverage works simply nearly as good as a coverage with a situation. In truth, I feel it’s a bit cleaner. Defining particular ARNs possible has stricter sort checking than the logic used behind the scenes to parse situations. For those who’re questioning why that’s, it’s defined on this collection on safe code:
Subsequent we’ll take a look at useful resource insurance policies and the confused deputy assault.
Comply with for updates.
Teri Radichel
For those who preferred this story please clap and comply with:
Medium: Teri Radichel or Electronic mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, shows, and podcasts


