Particulars have emerged a few lately patched crucial distant code execution vulnerability within the V8 JavaScript and WebAssembly engine utilized in Google Chrome and Chromium-based browsers.
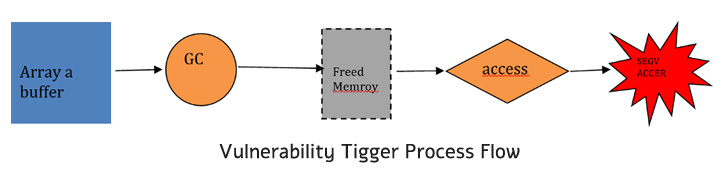
The difficulty pertains to a case of use-after-free within the instruction optimization element, profitable exploitation of which may “permit an attacker to execute arbitrary code within the context of the browser.”
The flaw, which was recognized within the Dev channel model of Chrome 101, was reported to Google by Weibo Wang, a safety researcher at Singapore cybersecurity firm Numen Cyber Know-how and has since been quietly fastened by the corporate.
“This vulnerability happens within the instruction choice stage, the place the incorrect instruction has been chosen and leading to reminiscence entry exception,” Wang stated.
Use-after-free flaws happen when previous-freed reminiscence is accessed, inducing undefined conduct and inflicting a program to crash, use corrupted information, and even obtain execution of arbitrary code.
What’s extra regarding is that the flaw will be exploited remotely by way of a specifically designed web site to bypass safety restrictions and run arbitrary code to compromise the focused programs.
“This vulnerability will be additional exploited utilizing heap spraying methods, after which results in ‘kind confusion’ vulnerability,” Wang defined. “The vulnerability permits an attacker to manage the perform pointers or write code into arbitrary areas in reminiscence, and in the end result in code execution.”
The corporate has not but disclosed the vulnerability by way of the Chromium bug tracker portal to provide as many customers as potential to put in the patched model first. Additionally, Google doesn’t assign CVE IDs for vulnerabilities present in non-stable Chrome channels.
Chrome customers, particularly builders who use the Dev version of Chrome for testing to make sure that their purposes are appropriate with the most recent Chrome options and API adjustments, ought to replace to the most recent out there model of the software program.
 |
| TurboFan meeting directions after vulnerability patched |
This isn’t the primary time use-after-free vulnerabilities have been found in V8. Google in 2021 addressed seven such bugs in Chrome which were exploited in real-world assaults. This yr, it additionally fastened an actively exploited use-after-free vulnerability within the Animation element.