Let’s face it: all of us use e-mail, and all of us use passwords. Passwords create inherent vulnerability within the system. The success price of phishing assaults is skyrocketing, and alternatives for the assault have vastly multiplied as lives moved on-line. All it takes is one password to be compromised for all different customers to grow to be victims of a knowledge breach.
To ship extra safety, due to this fact, digital identities depend on verification plasters. MFA (multi-factor authentication) typically falls again to information components corresponding to password resets and OTP codes, however these are nonetheless susceptible. So long as credentials might be shared or intercepted, they are often misused.
What is required is a paradigm shift – from knowledge-based credentials to sturdy possession-factor safety that may’t be compromised, alongside different verification safety corresponding to biometrics.
A brand new possession-factor API now goals to do exactly that, changing knowledge-based credentials, by utilizing the SIM card for possession issue gadget binding and person authentication, thus lowering the opportunity of phishing.
Phishing: a human downside
Phishing and different sorts of social engineering depend on the human issue to be the weakest hyperlink in a breach. They make use of the handy, credential-based entry afforded to the common person of a platform, by tricking these common customers into sharing credentials. And it really works: 83% of organizations surveyed mentioned they skilled a profitable email-based phishing assault in 2021.
Even 2FA codes at the moment are targets
It is common information that passwords might be shared and, due to this fact, simply phished. However a lesser-known reality is that many types of 2FA – such because the OTP or PIN code added in an effort to strengthen the recognized weaknesses in passwords – are additionally phishable.
Even worse, criminals at the moment are focusing on these strategies particularly: researchers not too long ago discovered that over 1,200 phishing kits designed to steal 2FA codes are out in operation.
The reply to identification and entry administration, due to this fact, is to not apply extra patches that kill the person expertise, as these do not actually hold attackers out. As an alternative, MFA wants a stronger, less complicated possession issue – with nothing to sort, which means nothing to phish.
Goal-designed MFA possession components embody safety dongles or tokens. However they’re costly, and never one thing the common person will purchase. Stronger safety for everybody can solely work with gadgets which might be broadly out there, straightforward to make use of, straightforward to combine, and cost-effective.
Enter the SIM card. It is inside everybody’s cell phone, and is constructed on cryptographic safety when connecting to cellular community authentication.
Now, for the primary time, an API from tru.ID opens up SIM-based cellular community authentication to each enterprise and app developer, which means you’ll be able to leverage the safety of the SIM card as a safe possession issue for MFA.
SIM-based authentication: the brand new phishing-resistant possession issue
The SIM card has so much going for it. SIM playing cards use the identical extremely safe, cryptographic microchip expertise that’s constructed into each bank card. It is troublesome to clone or tamper with, and there’s a SIM card in each cell phone – so each one in every of your customers already has this {hardware} of their pocket.
The mixture of the cell phone quantity with its related SIM card identification (the IMSI) is a mixture that is troublesome to phish as it is a silent authentication test.
The person expertise is superior too. Cellular networks routinely carry out silent checks {that a} person’s SIM card matches their telephone quantity with the intention to allow them to ship messages, make calls, and use information – making certain real-time authentication with out requiring a login.
Till not too long ago, it wasn’t potential for companies to program the authentication infrastructure of a cellular community into an app as simply as every other code. tru.ID makes community authentication out there to everybody.
Including the tru.ID SDK into current account journeys that use the cell phone quantity immediately permits possession-factor safety for each person. Furthermore, with no further enter from the person, there is no assault vector for malicious actors: SIM-based authentication is invisible, so there is no credentials or codes to steal, intercept or misuse.
tru.ID doesn’t entry the person’s SIM card. As an alternative, it verifies SIM card standing immediately with the cellular operator in real-time. It checks {that a} telephone quantity hasn’t been assigned to a different SIM and for latest SIM modifications, serving to to forestall SIM swap fraud.
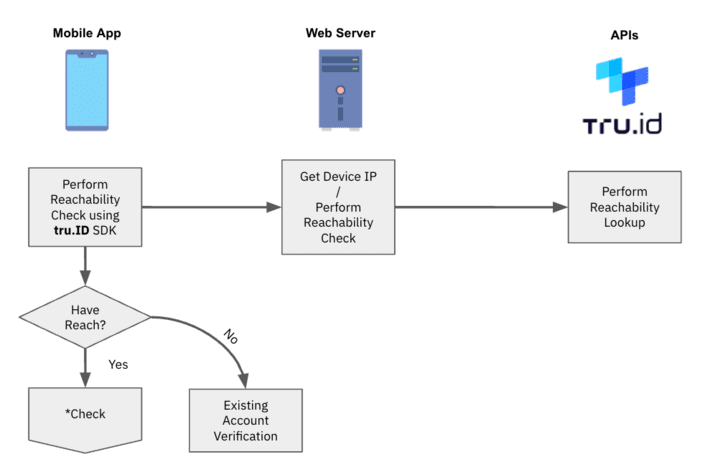
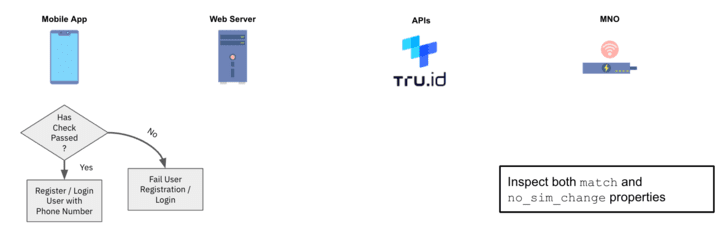
An instance situation to allow SIM-based verification
Though there are a variety of processes described within the situation under, the tip person of the system has to do just one factor – present their cell phone quantity.
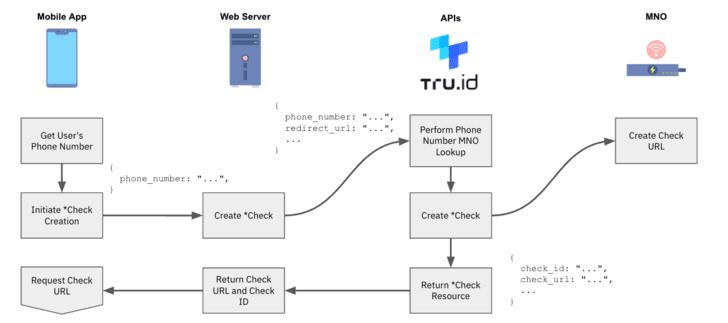
1 — After the person gives their cellular quantity, the tru.ID API performs a lookup for the telephone quantity to find out which cellular community operator (MNO) it’s assigned to.
2 — tru.ID requests from the MNO a novel Examine URL to start the cellular authentication workflow.
3 — tru.ID shops the MNO’s Examine URL, and returns a tru.ID Examine URL to your net server for the cellular gadget to open.
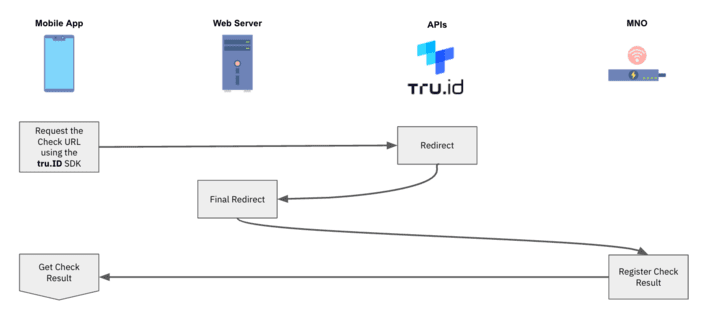
4 — The cellular utility opens the tru.ID Examine URL. It’s most well-liked to make use of tru.ID SDKs for this as a result of it forces the online request to be over a cellular information session.
5 — The MNO will obtain the online request by way of a redirect from the tru.ID platform.
6 — The ultimate redirect takes the gadget to the online server’s redirect url endpoint. The physique of this request will comprise a ‘code’ and the ‘check_id’, and the online server submits this code to tru. ID’s API to finish the SubscriberCheck course of.
7 — The MNO then determines if the telephone quantity related to the authenticated cellular information session matches the telephone quantity related to the requested Examine URL. If it does, then the telephone quantity has been efficiently verified.
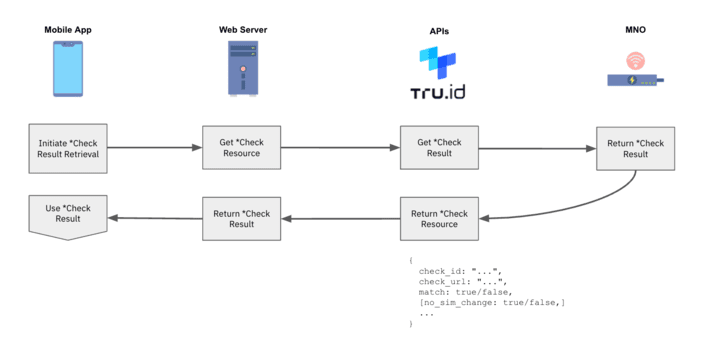
8 — tru.ID performs a SIM card lookup and shops the results of its standing.
9 — On completion of the Examine URL request, and when the SIM card standing has been retrieved, the cellular utility can request the results of the telephone verification from the tru.ID API.
10 — Use the telephone verification match and SIM card change `no_sim_change` properties inside your utility logic.
Tips on how to get began
With tru. ID’s developer platform, you can begin testing SIM-based authentication immediately, free of charge, and make your first API name inside minutes.
To learn the way next-gen authentication can ship excessive safety, low friction authentication experiences to your customers, merely ebook a free demo or go to tru.ID.