An “aggressive” superior persistent menace (APT) group often called SideWinder has been linked to over 1,000 new assaults since April 2020.
“A number of the fundamental traits of this menace actor that make it stand out among the many others, are the sheer quantity, excessive frequency and persistence of their assaults and the big assortment of encrypted and obfuscated malicious parts used of their operations,” cybersecurity agency Kaspersky mentioned in a report that was offered at Black Hat Asia this month.
SideWinder, additionally referred to as Rattlesnake or T-APT-04, is claimed to have been energetic since a minimum of 2012 with a monitor file of concentrating on navy, protection, aviation, IT firms, and authorized companies in Central Asian international locations corresponding to Afghanistan, Bangladesh, Nepal, and Pakistan.
Kaspersky’s APT tendencies report for Q1 2022 revealed late final month revealed that the menace actor is actively increasing the geography of its targets past its sufferer profile to different international locations and areas, together with Singapore.
SideWinder has additionally been noticed capitalizing on the continued Russo-Ukrainian warfare as a lure in its phishing campaigns to distribute malware and steal delicate data.
The adversarial collective’s an infection chains are notable for incorporating malware-rigged paperwork that benefit from a distant code vulnerability within the Equation Editor part of Microsoft Workplace (CVE-2017-11882) to deploy malicious payloads on compromised techniques.
Moreover, SideWinder’s toolset employs a number of subtle obfuscation routines, encryption with distinctive keys for every malicious file, multi-layer malware, and splitting command-and-control (C2) infrastructure strings into totally different malware parts.
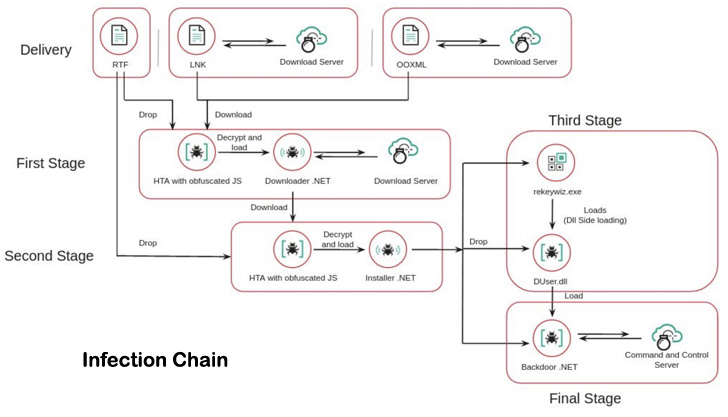
The three-stage an infection sequence commences with the rogue paperwork dropping a HTML Utility (HTA) payload, which subsequently masses a .NET-based module to put in a second-stage HTA part that is designed to deploy a .NET-based installer.
This installer, within the subsequent section, is each chargeable for establishing persistence on the host and loading the ultimate backdoor in reminiscence. The implant, for its half, is able to harvesting information of curiosity in addition to system data, amongst others.
No fewer than 400 domains and subdomains have been put to make use of by the menace actor over the previous two years. So as to add a further layer of stealth, the URLs used for C2 domains are sliced into two elements, the primary portion of which is included within the .NET installer and the latter half is encrypted contained in the second stage HTA module.
“This menace actor has a comparatively excessive stage of sophistication utilizing numerous an infection vectors and superior assault strategies,” Noushin Shabab of Kaspersky mentioned, urging that organizations use up-to-date variations of Microsoft Workplace to mitigate such assaults.