Insider threats are a severe and rising drawback. In response to latest analysis, malicious workers contribute to twenty% of incidents and the assaults that insiders are concerned in are, on common, 10 occasions bigger than these carried out by exterior actors. Additional information (PDF) has proven a rise in insider menace assaults over the previous two years, as the chance has been exacerbated by the distant working by the pandemic.
To attenuate insider threats, all organizations ought to monitor marketplaces, boards, and social media channels for chatter about their firm. This helps them to identify the early warning indicators of an imminent assault, comparable to cybercriminals in search of insider data, or disgruntled workers making unsavory feedback. This monitoring should additionally lengthen to the Darkish Net, as it is a gold mine for cybercriminal reconnaissance on organizations, as a result of menace actors consider that they are out of the attain of regulation enforcement and cybersecurity groups.
Forms of Insider Risk
Once we discuss insider threats it is very important perceive that there’s a couple of sort of malicious insider. Broadly, you possibly can categorize them in three teams:
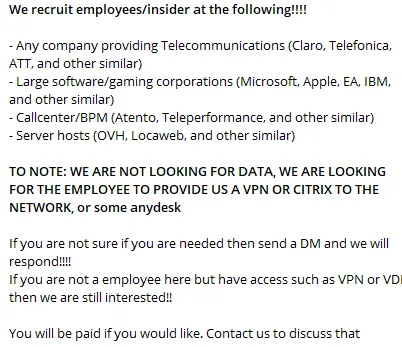
Insiders motivated by monetary positive factors: Within the present financial local weather, workers might be nudged into malicious exercise by menace teams. For instance, the menace group Lapsus$ infamously posted a recruitment name for assist from workers in telecom corporations, software program and gaming companies, and name facilities — providing cash in alternate for data.
Loners and opportunistic menace actors: These are hard-to-spot insiders who use their privileged place within the community to hurt the corporate. Whereas they’re statistically much less widespread, they will have a extreme influence on a corporation once they do strike. For instance, the New York Put up worker who took an ax to the corporate’s repute lately by posting offensive messages on its company Twitter account. Darkish Net evaluation can assist to identify these malicious actors if and once they publish an inquiry or ask for assistance on particular points they face when navigating across the company setting. They can be noticed providing to promote insider data on the Darkish Net.
Harmless insiders: These can additionally unwittingly hurt the corporate by being concerned in menace exercise with out their consent or data. In response to analysis, workers are greater than twice as more likely to make an error and click on malicious hyperlinks, reasonably than to maliciously misuse their entry.
That is who you are up towards, but it surely’s additionally essential to know what malicious actors might be in search of, inquiring about, or promoting.
Risk Modeling for Insider Risk
Corporations menace modeling for malicious insiders must determine the place their infrastructure is probably the most insecure, what property they’ve which might be the best worth, and which techniques are most often utilized by menace actors. Perception into the Darkish Net can assist the group set up how criminals go about their reconnaissance and use malicious insiders, which can assist inform their defenses.
The most well-liked technique used to realize entry to an organization’s setting is acquiring and using leaked credentials. However aside from primary “password and username” gross sales, companies additionally must look out for cookie-session leaks for apps comparable to Slack and Groups, which menace actors can use to socially engineer their manner into the corporate and abuse the belief of an worker.
One other facet that corporations have to be acutely aware of are set off occasions that enhance the chance of an organization being focused for assault. For instance, if an oil firm is ready to announce its annual income throughout a cost-of-living disaster, the group should assess the animosity degree from workers, ex-employees, and outsiders reacting to the announcement. The income reveal, on this instance, is a possible set off occasion, requiring the enterprise to be notably diligent in monitoring the Darkish Net for any chatter across the firm earlier than, throughout, and after the occasion. In instances like these, corporations should ask themselves whether or not they need to implement further defenses or apportion extra sources.
Throughout set off occasions, corporations may doubtlessly spot malicious insiders by monitoring an uptick in alerts or irregular on-line exercise. Connections between an organization gadget and the Tor community are a really dependable information level for locating an insider menace, as a result of there may be just about no good purpose why an worker could be connecting to the Darkish Net in most organizations.
Shifting Left within the Cyber Kill Chain
As with every incident, time is at all times of the essence. The place doable, organizations must pinpoint insider menace exercise throughout reconnaissance, the primary stage of the cyber kill chain, to efficiently mitigate towards a malicious actor. Logic dictates that the sooner, or additional to the left within the kill chain, that menace actors might be recognized, then the much less doubtless they’re to achieve success of their assault.
Organizations perceive the necessity for preparedness, shielding their borders, and educating their workers. Nonetheless, these are merely a strong basis of safety infrastructure that requires augmenting with intelligence to cease threats earlier. Darkish Net menace intelligence needs to be thought-about as an integral part to enhancing an organizations’ safety posture. As most cybercriminals depend on Darkish Net infrastructure to conduct their operations, chopping off this channel can vastly scale back the prospect of insider threats taking maintain and disrupting enterprise operations.