Reminiscence security in Chrome is an ever-ongoing effort to guard our customers. We’re always experimenting with completely different applied sciences to remain forward of malicious actors. On this spirit, this submit is about our journey of utilizing heap scanning applied sciences to enhance reminiscence security of C++.
Let’s begin at the start although. All through the lifetime of an software its state is usually represented in reminiscence. Temporal reminiscence security refers back to the drawback of guaranteeing that reminiscence is at all times accessed with the hottest info of its construction, its kind. C++ sadly doesn’t present such ensures. Whereas there’s urge for food for various languages than C++ with stronger reminiscence security ensures, massive codebases akin to Chromium will use C++ for the foreseeable future.
Within the instance above, foo is used after its reminiscence has been returned to the underlying system. The out-of-date pointer known as a dangling pointer and any entry by way of it leads to a use-after-free (UAF) entry. In the perfect case such errors lead to well-defined crashes, within the worst case they trigger delicate breakage that may be exploited by malicious actors.
UAFs are sometimes onerous to identify in bigger codebases the place possession of objects is transferred between numerous elements. The final drawback is so widespread that to this date each trade and academia repeatedly give you mitigation methods. The examples are infinite: C++ good pointers of all types are used to higher outline and handle possession on software degree; static evaluation in compilers is used to keep away from compiling problematic code within the first place; the place static evaluation fails, dynamic instruments akin to C++ sanitizers can intercept accesses and catch issues on particular executions.
Chrome’s use of C++ is unfortunately no completely different right here and the vast majority of high-severity safety bugs are UAF points. So as to catch points earlier than they attain manufacturing, all the aforementioned strategies are used. Along with common assessments, fuzzers be sure that there’s at all times new enter to work with for dynamic instruments. Chrome even goes additional and employs a C++ rubbish collector referred to as Oilpan which deviates from common C++ semantics however gives temporal reminiscence security the place used. The place such deviation is unreasonable, a brand new sort of good pointer referred to as MiraclePtr was launched lately to deterministically crash on accesses to dangling pointers when used. Oilpan, MiraclePtr, and smart-pointer-based options require important adoptions of the appliance code.
During the last decade, one other method has seen some success: reminiscence quarantine. The fundamental thought is to place explicitly freed reminiscence into quarantine and solely make it accessible when a sure security situation is reached. Microsoft has shipped variations of this mitigation in its browsers: MemoryProtector in Web Explorer in 2014 and its successor MemGC in (pre-Chromium) Edge in 2015. Within the Linux kernel a probabilistic method was used the place reminiscence was ultimately simply recycled. And this method has seen consideration in academia in recent times with the MarkUs paper. The remainder of this text summarizes our journey of experimenting with quarantines and heap scanning in Chrome.
(At this level, one might ask the place pointer authentication suits into this image – carry on studying!)
Quarantining and Heap Scanning, the Fundamentals
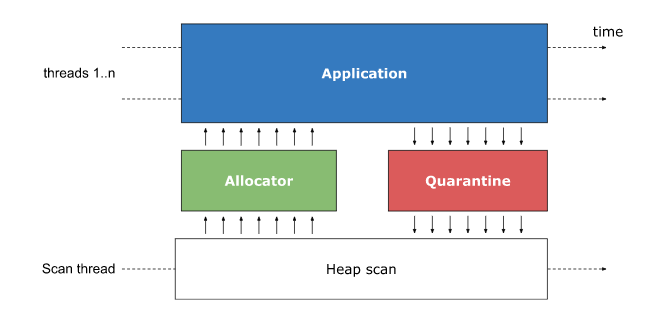
The principle thought behind assuring temporal security with quarantining and heap scanning is to keep away from reusing reminiscence till it has been confirmed that there aren’t any extra (dangling) pointers referring to it. To keep away from altering C++ person code or its semantics, the reminiscence allocator offering new and delete is intercepted.
Upon invoking delete, the reminiscence is definitely put in a quarantine, the place it’s unavailable for being reused for subsequent new calls by the appliance. Sooner or later a heap scan is triggered which scans the entire heap, very like a rubbish collector, to search out references to quarantined reminiscence blocks. Blocks that haven’t any incoming references from the common software reminiscence are transferred again to the allocator the place they are often reused for subsequent allocations.
There are numerous hardening choices which include a efficiency price:
-
Overwrite the quarantined reminiscence with particular values (e.g. zero);
-
Cease all software threads when the scan is working or scan the heap concurrently;
-
Intercept reminiscence writes (e.g. by web page safety) to catch pointer updates;
-
Scan reminiscence phrase by phrase for potential pointers (conservative dealing with) or present descriptors for objects (exact dealing with);
-
Segregation of software reminiscence in protected and unsafe partitions to opt-out sure objects that are both efficiency delicate or will be statically confirmed as being protected to skip;
-
Scan the execution stack along with simply scanning heap reminiscence;
We name the gathering of various variations of those algorithms StarScan [stɑː skæn], or *Scan for brief.
Actuality Verify
We apply *Scan to the unmanaged elements of the renderer course of and use Speedometer2 to judge the efficiency impression.
We have now experimented with completely different variations of *Scan. To reduce efficiency overhead as a lot as potential although, we consider a configuration that makes use of a separate thread to scan the heap and avoids clearing of quarantined reminiscence eagerly on delete however slightly clears quarantined reminiscence when working *Scan. We decide in all reminiscence allotted with new and don’t discriminate between allocation websites and kinds for simplicity within the first implementation.
Observe that the proposed model of *Scan shouldn’t be full. Concretely, a malicious actor might exploit a race situation with the scanning thread by shifting a dangling pointer from an unscanned to an already scanned reminiscence area. Fixing this race situation requires retaining observe of writes into blocks of already scanned reminiscence, by e.g. utilizing reminiscence safety mechanisms to intercept these accesses, or stopping all software threads in safepoints from mutating the thing graph altogether. Both approach, fixing this situation comes at a efficiency price and reveals an fascinating efficiency and safety trade-off. Observe that this type of assault shouldn’t be generic and doesn’t work for all UAF. Issues akin to depicted within the introduction wouldn’t be vulnerable to such assaults because the dangling pointer shouldn’t be copied round.
For the reason that safety advantages actually depend upon the granularity of such safepoints and we need to experiment with the quickest potential model, we disabled safepoints altogether.
Operating our primary model on Speedometer2 regresses the overall rating by 8%. Bummer…
The place does all this overhead come from? Unsurprisingly, heap scanning is reminiscence sure and fairly costly as the complete person reminiscence should be walked and examined for references by the scanning thread.
To scale back the regression we applied numerous optimizations that enhance the uncooked scanning velocity. Naturally, the quickest solution to scan reminiscence is to not scan it in any respect and so we partitioned the heap into two lessons: reminiscence that may include pointers and reminiscence that we will statically show to not include pointers, e.g. strings. We keep away from scanning reminiscence that can’t include any pointers. Observe that such reminiscence continues to be a part of the quarantine, it’s simply not scanned.
We prolonged this mechanism to additionally cowl allocations that function backing reminiscence for different allocators, e.g., zone reminiscence that’s managed by V8 for the optimizing JavaScript compiler. Such zones are at all times discarded without delay (c.f. region-based reminiscence administration) and temporal security is established by way of different means in V8.
On high, we utilized a number of micro optimizations to hurry up and remove computations: we use helper tables for pointer filtering; depend on SIMD for the memory-bound scanning loop; and decrease the variety of fetches and lock-prefixed directions.
We additionally enhance upon the preliminary scheduling algorithm that simply begins a heap scan when reaching a sure restrict by adjusting how a lot time we spent in scanning in comparison with truly executing the appliance code (c.f. mutator utilization in rubbish assortment literature).
Ultimately, the algorithm continues to be reminiscence sure and scanning stays a noticeably costly process. The optimizations helped to scale back the Speedometer2 regression from 8% right down to 2%.
Whereas we improved uncooked scanning time, the truth that reminiscence sits in a quarantine will increase the general working set of a course of. To additional quantify this overhead, we use a specific set of Chrome’s real-world shopping benchmarks to measure reminiscence consumption. *Scan within the renderer course of regresses reminiscence consumption by about 12%. It’s this enhance of the working set that results in extra reminiscence being paged through which is noticeable on software quick paths.
{Hardware} Reminiscence Tagging to the Rescue
MTE (Reminiscence Tagging Extension) is a brand new extension on the ARM v8.5A structure that helps with detecting errors in software program reminiscence use. These errors will be spatial errors (e.g. out-of-bounds accesses) or temporal errors (use-after-free). The extension works as follows. Each 16 bytes of reminiscence are assigned a 4-bit tag. Pointers are additionally assigned a 4-bit tag. The allocator is chargeable for returning a pointer with the identical tag because the allotted reminiscence. The load and retailer directions confirm that the pointer and reminiscence tags match. In case the tags of the reminiscence location and the pointer don’t match a {hardware} exception is raised.
MTE would not supply a deterministic safety towards use-after-free. For the reason that variety of tag bits is finite there’s a probability that the tag of the reminiscence and the pointer match as a result of overflow. With 4 bits, solely 16 reallocations are sufficient to have the tags match. A malicious actor might exploit the tag bit overflow to get a use-after-free by simply ready till the tag of a dangling pointer matches (once more) the reminiscence it’s pointing to.
*Scan can be utilized to repair this problematic nook case. On every delete name the tag for the underlying reminiscence block will get incremented by the MTE mechanism. More often than not the block will likely be accessible for reallocation because the tag will be incremented throughout the 4-bit vary. Stale pointers would discuss with the previous tag and thus reliably crash on dereference. Upon overflowing the tag, the thing is then put into quarantine and processed by *Scan. As soon as the scan verifies that there aren’t any extra dangling tips that could this block of reminiscence, it’s returned again to the allocator. This reduces the variety of scans and their accompanying price by ~16x.
The next image depicts this mechanism. The pointer to foo initially has a tag of 0x0E which permits it to be incremented as soon as once more for allocating bar. Upon invoking delete for bar the tag overflows and the reminiscence is definitely put into quarantine of *Scan.
We obtained our fingers on some precise {hardware} supporting MTE and redid the experiments within the renderer course of. The outcomes are promising because the regression on Speedometer was inside noise and we solely regressed reminiscence footprint by round 1% on Chrome’s real-world shopping tales.
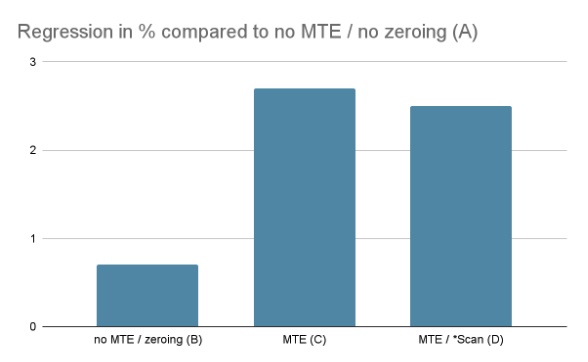
Is that this some precise free lunch? Seems that MTE comes with some price which has already been paid for. Particularly, PartitionAlloc, which is Chrome’s underlying allocator, already performs the tag administration operations for all MTE-enabled units by default. Additionally, for safety causes, reminiscence ought to actually be zeroed eagerly. To quantify these prices, we ran experiments on an early {hardware} prototype that helps MTE in a number of configurations:
-
MTE disabled and with out zeroing reminiscence;
-
MTE disabled however with zeroing reminiscence;
-
MTE enabled with out *Scan;
-
MTE enabled with *Scan;
(We’re additionally conscious that there’s synchronous and asynchronous MTE which additionally impacts determinism and efficiency. For the sake of this experiment we saved utilizing the asynchronous mode.)
The outcomes present that MTE and reminiscence zeroing include some price which is round 2% on Speedometer2. Observe that neither PartitionAlloc, nor {hardware} has been optimized for these eventualities but. The experiment additionally reveals that including *Scan on high of MTE comes with out measurable price.
Conclusions
C++ permits for writing high-performance functions however this comes at a value, safety. {Hardware} reminiscence tagging might repair some safety pitfalls of C++, whereas nonetheless permitting excessive efficiency. We’re trying ahead to see a extra broad adoption of {hardware} reminiscence tagging sooner or later and recommend utilizing *Scan on high of {hardware} reminiscence tagging to repair short-term reminiscence security for C++. Each the used MTE {hardware} and the implementation of *Scan are prototypes and we count on that there’s nonetheless room for efficiency optimizations.