A brand new, multi-functional Go-based malware dubbed Chaos has been quickly rising in quantity in latest months to ensnare a variety of Home windows, Linux, small workplace/dwelling workplace (SOHO) routers, and enterprise servers into its botnet.
“Chaos performance contains the flexibility to enumerate the host atmosphere, run distant shell instructions, load extra modules, routinely propagate by stealing and brute-forcing SSH non-public keys, in addition to launch DDoS assaults,” researchers from Lumen’s Black Lotus Labs stated in a write-up shared with The Hacker Information.
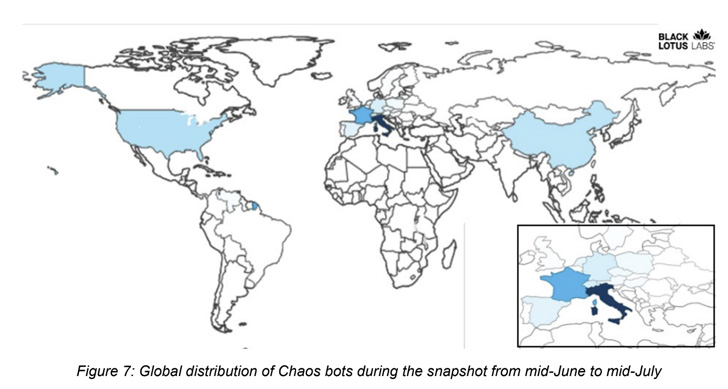
A majority of the bots are positioned in Europe, particularly Italy, with different infections reported in China and the U.S., collectively representing “a whole lot of distinctive IP addresses” over a one-month time interval from mid-June by mid-July 2022.
Written in Chinese language and leveraging China-based infrastructure for command-and-control, the botnet joins a protracted record of malware which might be designed to ascertain persistence for prolonged intervals and sure abuse the foothold for nefarious functions, akin to DDoS assaults and cryptocurrency mining.
If something, the event additionally factors to a dramatic uptick in menace actors shifting to programming languages like Go to evade detection and render reverse engineering troublesome, to not point out focusing on a number of platforms directly.
Chaos (to not be confused with the ransomware builder of the identical title) lives as much as its title by exploiting identified safety vulnerabilities to achieve preliminary entry, subsequently abusing it to conduct reconnaissance and provoke lateral motion throughout the compromised community.
What’s extra, the malware has versatility that related malware doesn’t, enabling it to function throughout a variety of instruction set architectures from ARM, Intel (i386), MIPS, and PowerPC, successfully permitting the menace actor to broaden the scope of its targets and swiftly accrue in quantity.
On prime of that, Chaos additional has the flexibility to execute as many as 70 totally different instructions despatched from the C2 server, considered one of which is an instruction to set off the exploitation of publicly-disclosed flaws (CVE-2017-17215 and CVE-2022-30525) outlined in a file.
Chaos can be believed to be an evolution of one other Go-based DDoS malware named Kaiji that has beforehand focused misconfigured Docker cases. The correlations, per Black Lotus Labs, stem from overlapping code and features primarily based on an evaluation of over 100 samples.
A GitLab server positioned in Europe was one among the many victims of the Chaos botnet within the first weeks of September, the corporate stated, including it recognized a string of DDoS assaults aimed toward entities spanning gaming, monetary providers, and expertise, media and leisure, and internet hosting suppliers. Additionally focused was a crypto mining change.
The findings come precisely three months after the cybersecurity firm uncovered a brand new distant entry trojan dubbed ZuoRAT that has been singling out SOHO routers as a part of a classy marketing campaign directed in opposition to North American and European networks.
“We’re seeing a fancy malware that has quadrupled in measurement in simply two months, and it’s well-positioned to proceed accelerating,” stated Mark Dehus, director of menace intelligence for Lumen Black Lotus Labs. “Chaos poses a menace to quite a lot of shopper and enterprise gadgets and hosts.”