A brand new covert assault marketing campaign singled out a number of navy and weapons contractor firms with spear-phishing emails to set off a multi-stage an infection course of designed to deploy an unknown payload on compromised machines.
The highly-targeted intrusions, dubbed STEEP#MAVERICK by Securonix, additionally focused a strategic provider to the F-35 Lightning II fighter plane.
“The assault was carried out beginning in late summer time 2022 concentrating on no less than two high-profile navy contractor firms,” Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in an evaluation.
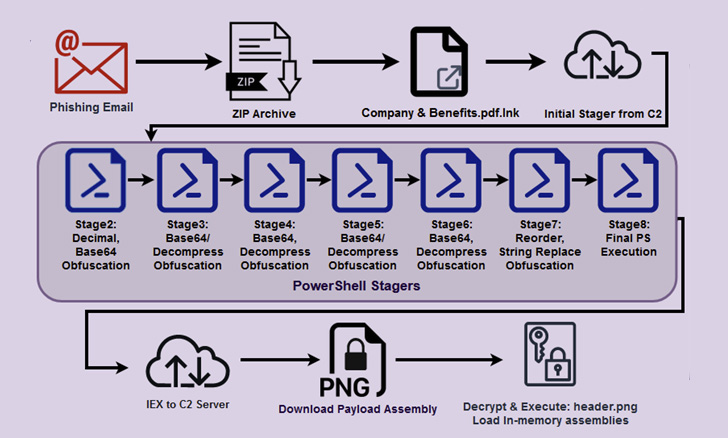
An infection chains start with a phishing mail with a ZIP archive attachment containing a shortcut file that claims to be a PDF doc about “Firm & Advantages,” which is then used to retrieve a stager — an preliminary binary that is used to obtain the specified malware — from a distant server.
This PowerShell stager units the stage for a “strong chain of stagers” that progresses by means of seven extra steps, when the ultimate PowerShell script executes a distant payload “header.png” hosted on a server named “terma[.]app.”
“Whereas we had been capable of obtain and analyze the header.png file, we weren’t capable of decode it as we imagine the marketing campaign was accomplished and our concept is that the file was changed as a way to forestall additional evaluation,” the researchers defined.
“Our makes an attempt to decode the payload would solely produce rubbish knowledge.”
What’s notable in regards to the modus operandi is the incorporation of obfuscated code designed to thwart evaluation, along with scanning for the presence of debugging software program and halt the execution if the system language is about to Chinese language or Russian.
The malware can be designed to confirm the quantity of bodily reminiscence, and as soon as once more terminate itself if it is lower than 4GB. Additionally included is a test for virtualization infrastructure to find out if the malware is being executed in an evaluation surroundings or sandbox.
But when this take a look at fails, fairly than merely quitting the execution, the malware disables system community adapters, reconfigures Home windows Firewall to dam all inbound and outbound visitors, recursively deletes knowledge in all drives, and shuts down the pc.
Ought to all these checks move, the PowerShell stager proceeds to disable logging, add Home windows Defender exclusions for LNK, RAR, and EXE information, and set up persistence through a scheduled process or Home windows Registry modifications.
“General, it’s clear that this assault was comparatively refined with the malicious menace actor paying particular consideration to opsec,” the researchers famous. “Whereas this was a really focused assault, the ways and strategies used are well-known and you will need to keep vigilant.”