The lately found Linux-Primarily based ransomware pressure referred to as Cheerscrypt has been attributed to a Chinese language cyber espionage group recognized for working short-lived ransomware schemes.
Cybersecurity agency Sygnia attributed the assaults to a risk actor it tracks below the title Emperor Dragonfly, which is also referred to as Bronze Starlight (Secureworks) and DEV-0401 (Microsoft).
“Emperor Dragonfly deployed open supply instruments that had been written by Chinese language builders for Chinese language customers,” the corporate stated in a report shared with The Hacker Information. “This reinforces claims that the ‘Emperor Dragonfly’ ransomware operators are primarily based in China.”
The usage of Cheerscrypt is the newest addition to an extended record of ransomware households beforehand deployed by the group in little over a 12 months, together with LockFile, Atom Silo, Rook, Evening Sky, Pandora, and LockBit 2.0.
Secureworks, in its profile of the group, famous “it’s believable that Bronze Starlight deploys ransomware as a smokescreen somewhat than for monetary achieve, with the underlying motivation of stealing mental property theft or conducting espionage.”
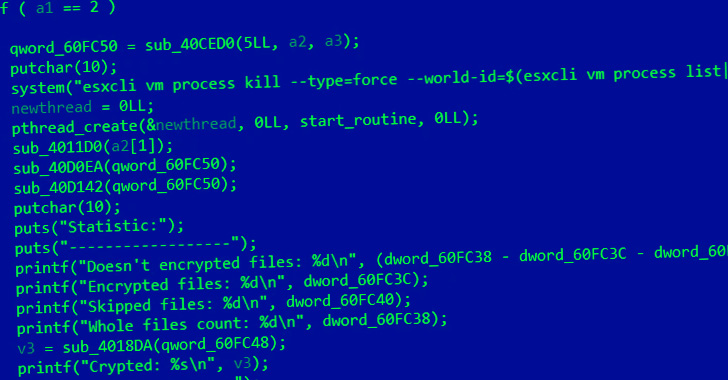
Cheerscrypt was first documented by Pattern Micro in Could 2022, calling out its skills to focus on VMware ESXi servers as a part of a tried-and-tested tactic known as double extortion to coerce its victims into paying the ransom or threat going through knowledge publicity.
It has additionally claimed to be pro-Ukrainian, displaying a “Glory to Ukraine!” message on their darkish net knowledge leak web site.
Apparently, the ransomware shares overlaps with the Linux model of the Babuk ransomware, which had its supply code leaked in September 2021 and likewise kinds the premise of Emperor Dragonfly’s Rook, Evening Sky, and Pandora households.
The risk actor’s modus operandi additional stands out for its dealing with of all phases of the ransomware assault lifecycle, proper from preliminary entry to ransomware deployment, with out counting on associates and entry brokers. Microsoft described DEV-0401 as a “lone wolf” actor.
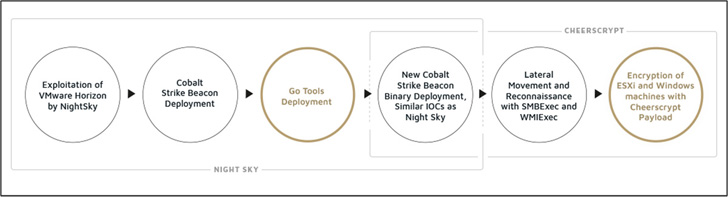
An infection chains noticed up to now have made use of the vital Log4Shell vulnerability in Apache Log4j library to compromise VMware Horizon servers to drop a PowerShell payload able to delivering an encrypted Cobalt Strike beacon.
Sygnia stated that it additionally found three extra Go-based instruments deployed in tandem to the beacon: a keylogger that exports the recorded keystrokes to Alibaba Cloud, an web proxy utility known as iox, and a tunneling software program referred to as NPS.
Cheerscrypt’s hyperlinks to Emperor Dragonfly stems from similarities in preliminary entry vectors, lateral motion methods, and the deployment of the encrypted Cobalt Strike beacon through DLL side-loading.
“Emperor Dragonfly is a China-based ransomware operator, making it a rarity in immediately’s risk panorama,” researchers stated, including “a single risk actor carried out your entire operation.”