The Raspberry Robin worm has been utilized in assaults towards telecommunications and authorities workplace techniques throughout Latin America, Australia, and Europe since a minimum of September 2022.
“The principle payload itself is full of greater than 10 layers for obfuscation and is able to delivering a faux payload as soon as it detects sandboxing and safety analytics instruments,” Pattern Micro researcher Christopher So stated in a technical evaluation printed Tuesday.
A majority of the infections have been detected in Argentina, adopted by Australia, Mexico, Croatia, Italy, Brazil, France, India, and Colombia.
Raspberry Robin, attributed to an exercise cluster tracked by Microsoft as DEV-0856, is being more and more leveraged by a number of menace actors as an preliminary entry mechanism to ship payloads akin to LockBit and Clop ransomware.
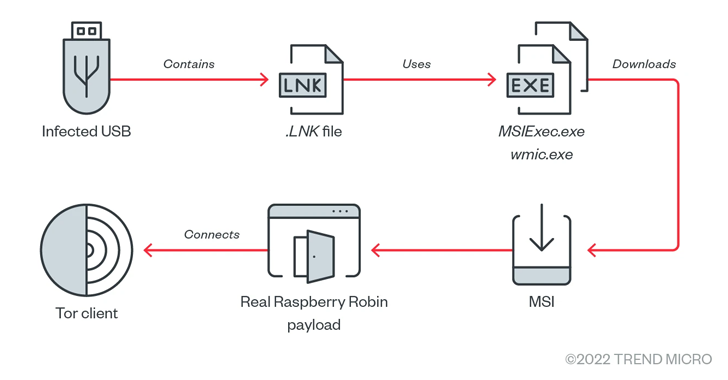
The malware is thought for counting on contaminated USB drives as a distribution vector to obtain a rogue MSI installer file that deploys the primary payload chargeable for facilitating post-exploitation.
Additional evaluation of Raspberry Robin reveals using heavy obfuscation to stop evaluation, with the malware “composed of two payloads embedded in a payload loader packed six instances.”
The payload loader, for its half, is orchestrated to load the decoy payload, an adware dubbed BrowserAssistant, to throw off detection efforts.
Ought to no sandboxing and evaluation be noticed, the legit payload is put in and proceeds to connect with a hard-coded .onion handle utilizing a customized TOR shopper embedded inside it to await additional instructions.
The TOR shopper course of masquerades as legit Home windows processes like dllhost.exe, regsvr32.exe, and rundll32.exe, as soon as once more underscoring the appreciable efforts made by the menace actor to fly beneath the radar.
What’s extra, the malware’s actual routine is run in Session 0, a specialised Home windows session reserved for providers and different non-interactive person functions to mitigate safety dangers akin to shatter assaults.
Pattern Micro stated it discovered similarities in a privilege escalation and an anti-debugging method utilized by Raspberry Robin and LockBit ransomware, hinting at a possible connection between the 2 legal actors.
“The group behind Raspberry Robin is the maker of among the instruments LockBit can also be utilizing,” the corporate theorized, including it alternatively “availed of the providers of the affiliate chargeable for the methods utilized by LockBit.”
That having stated, the intrusions seem like a reconnaissance operation, as no knowledge is returned from the TOR area, suggesting that the group behind the malware is “testing the waters to see how far its deployments can unfold.”