Researchers are warning a few spike in exploitation makes an attempt weaponizing a essential distant code execution flaw in Realtek Jungle SDK because the begin of August 2022.
In line with Palo Alto Networks Unit 42, the continued marketing campaign is alleged to have recorded 134 million exploit makes an attempt as of December 2022, with 97% of the assaults occurring up to now 4 months.
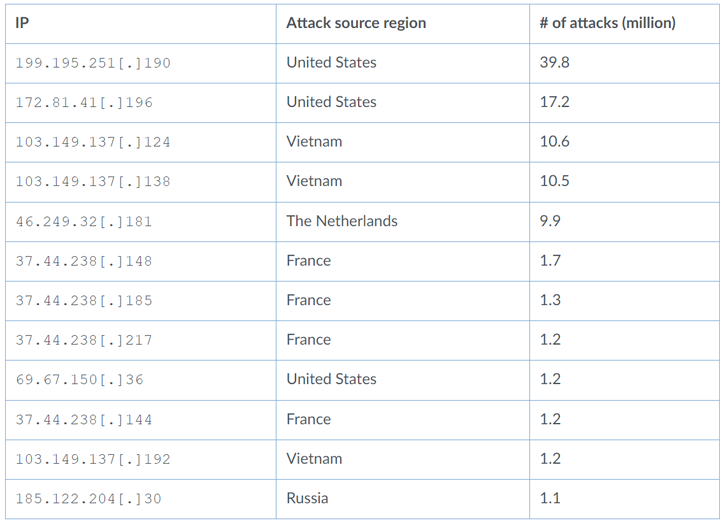
Near 50% of the assaults originated from the U.S. (48.3%), adopted by Vietnam (17.8%), Russia (14.6%), The Netherlands (7.4%), France (6.4%), Germany (2.3percent0, and Luxembourg (1.6%).
What’s extra, 95% of the assaults leveraging the safety shortcoming that emanated from Russia singled out organizations in Australia.
“Lots of the assaults we noticed tried to ship malware to contaminate susceptible IoT units,” Unit 42 researchers stated in a report, including “menace teams are utilizing this vulnerability to hold out large-scale assaults on good units all over the world.”
The vulnerability in query is CVE-2021-35394 (CVSS rating: 9.8), a set of buffer overflows and an arbitrary command injection bug that might be weaponized to execute arbitrary code with the very best stage of privilege and take over affected home equipment.
The problems had been disclosed by ONEKEY (beforehand IoT Inspector) in August 2021. The vulnerability impacts a variety of units from D-Hyperlink, LG, Belkin, Belkin, ASUS, and NETGEAR.
Unit 42 stated it found three totally different sorts of payloads distributed on account of in-the-wild exploitation of the flaw –
- A script executes a shell command on the focused server to obtain further malware
- An injected command that writes a binary payload to a file and executes it, and
- An injected command that instantly reboots the focused server to trigger a denial-of-service (DoS) situation
Additionally delivered via the abuse of CVE-2021-35394 are recognized botnets like Mirai, Gafgyt, and Mozi, in addition to a brand new Golang-based distributed denial-of-service (DDoS) botnet dubbed RedGoBot.
First noticed in September 2022, the RedGoBot marketing campaign includes dropping a shell script that is designed to obtain plenty of botnet purchasers tailor-made to totally different CPU architectures. The malware, as soon as launched, is supplied to run working system instructions and mount DDoS assaults.
The findings as soon as once more underscore the significance of updating software program in a well timed style to keep away from publicity to potential threats.
“The surge of assaults leveraging CVE-2021-35394 exhibits that menace actors are very curious about provide chain vulnerabilities, which might be tough for the common person to determine and remediate,” the researchers concluded. “These points could make it tough for the affected person to determine the particular downstream merchandise which might be being exploited.”