A model of an open supply ransomware toolkit known as Cryptonite has been noticed within the wild with wiper capabilities attributable to its “weak structure and programming.”
Cryptonite, in contrast to different ransomware strains, shouldn’t be accessible on the market on the cybercriminal underground, and was as an alternative provided without spending a dime by an actor named CYBERDEVILZ till not too long ago via a GitHub repository. The supply code and its forks have since been taken down.
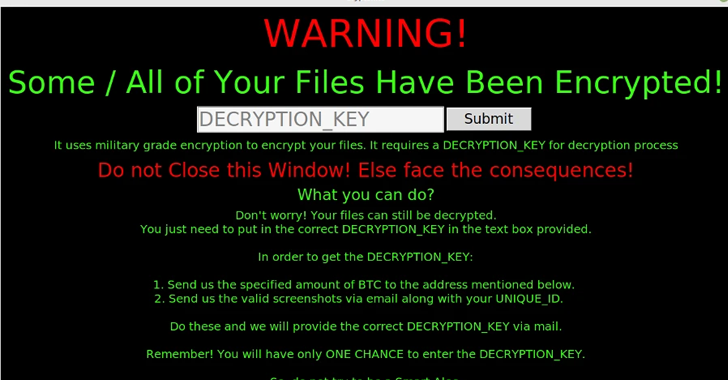
Written in Python, the malware employs the Fernet module of the cryptography bundle to encrypt recordsdata with a “.cryptn8” extension.
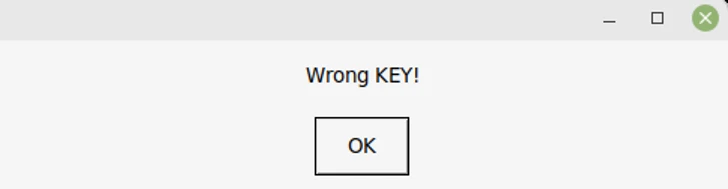
However a new pattern analyzed by Fortinet FortiGuard Labs has been discovered to lock recordsdata with no choice to decrypt them again, primarily appearing as a harmful knowledge wiper.
However this alteration is not a deliberate try on a part of the menace actor, however somewhat stems from a scarcity of high quality assurance that causes this system to crash when making an attempt to show the ransom notice after finishing the encryption course of.
“The issue with this flaw is that as a result of design simplicity of the ransomware if this system crashes — or is even closed — there isn’t a technique to get well the encrypted recordsdata,” Fortinet researcher Gergely Revay mentioned in a Monday write-up.
The exception thrown in the course of the execution of the ransomware program additionally implies that the “key” used to encrypt the recordsdata is rarely transmitted to the operators, thereby locking customers out of their knowledge.
The findings come in opposition to the backdrop of an evolving ransomware panorama the place wipers beneath the guise of file-encrypting malware are being more and more deployed to overwrite knowledge with out permitting for decryption.