The prolific North Korean nation-state actor often known as the Lazarus Group has been linked to a brand new distant entry trojan known as MagicRAT.
The beforehand unknown piece of malware is alleged to have been deployed in sufferer networks that had been initially breached by way of profitable exploitation of internet-facing VMware Horizon servers, Cisco Talos mentioned in a report shared with The Hacker Information.
“Whereas being a comparatively easy RAT capability-wise, it was constructed with recourse to the Qt Framework, with the only intent of constructing human evaluation tougher, and automatic detection via machine studying and heuristics much less probably,” Talos researchers Jung soo An, Asheer Malhotra, and Vitor Ventura mentioned.
Lazarus Group, often known as APT38, Darkish Seoul, Hidden Cobra, and Zinc, refers to a cluster of economic motivated and espionage-driven cyber actions undertaken by the North Korean authorities as a way to sidestep sanctions imposed on the nation and meet its strategic goals.
Like different umbrella collectives Winnti and MuddyWater, the state-sponsored hacking collective additionally has “spin-off” teams comparable to Bluenoroff and Andariel, which give attention to particular sorts of assaults and targets.
Whereas the Bluenoroff subgroup is targeted on attacking overseas monetary establishments and perpetrating financial theft, Andariel is devoted in its pursuit of South Korean organizations and companies.
“Lazarus develops their very own assault instruments and malware, can use modern assault strategies, works very methodically, and takes their time,” cybersecurity agency NCC Group mentioned in a report detailing the menace actor.
“Particularly, the North Korean strategies goal to keep away from detection by safety merchandise and to stay undetected throughout the hacked programs for so long as doable.”
The most recent addition to its wide-ranging malware toolset reveals the group’s capacity to make use of a large number of ways and strategies relying on their targets and their operational objectives.
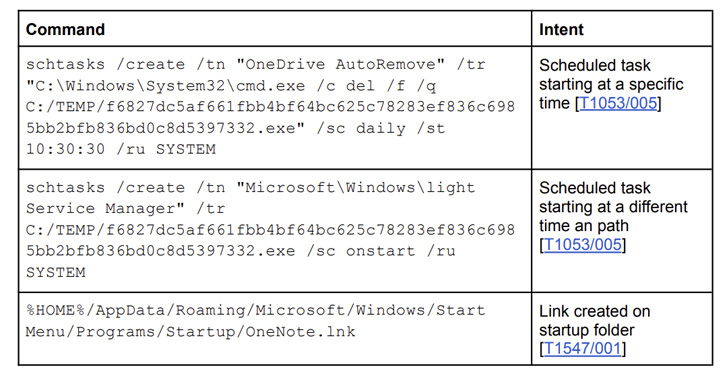
A C++-based implant, MagicRAT is designed to attain persistence by creating scheduled duties on the compromised system. It is also “slightly easy” in that it supplies the attacker with a distant shell to execute arbitrary instructions and perform file operations.
MagicRAT can be able to launching further payloads retrieved from a distant server on contaminated hosts. One of many executables retrieved from the command-and-control (C2) server takes the type of a GIF picture file, however in actuality is a light-weight port scanner.
Moreover, the C2 infrastructure related to MagicRAT has been discovered harboring and serving newer variations of TigerRAT, a backdoor previously attributed to Andariel and is engineered to execute instructions, take screenshots, log keystrokes, and harvest system data.
Additionally included within the newest variant is a USB Dump function that permits the adversary to hunt for recordsdata with particular extensions, alongside laying the groundwork for implementing video seize from webcams.
“The invention of MagicRAT within the wild is a sign of Lazarus’ motivations to quickly construct new, bespoke malware to make use of together with their beforehand recognized malware comparable to TigerRAT to focus on organizations worldwide,” the researchers mentioned.