An enhanced model of the XLoader malware has been noticed adopting a probability-based method to camouflage its command-and-control (C&C) infrastructure, in accordance with the newest analysis.
“Now it’s considerably more durable to separate the wheat from the chaff and uncover the true C&C servers amongst 1000’s of official domains utilized by Xloader as a smokescreen,” Israeli cybersecurity firm Verify Level mentioned.
First noticed within the wild in October 2020, XLoader is a successor to Formbook and a cross-platform info stealer that is able to plundering credentials from internet browsers, capturing keystrokes and screenshots, and executing arbitrary instructions and payloads.
Extra just lately, the ongoing geopolitical battle between Russia and Ukraine has proved to be a profitable fodder for distributing XLoader by the use of phishing emails aimed toward high-ranking authorities officers in Ukraine.
The most recent findings from Verify Level construct on a earlier report from Zscaler in January 2022, which revealed the inside workings of the malware’s C&C (or C2) community encryption and communication protocol, noting its use of decoy servers to hide the official server and evade malware evaluation methods.
“The C2 communications happen with the decoy domains and the true C2 server, together with sending stolen knowledge from the sufferer,” the researchers defined. “Thus, there’s a chance {that a} backup C2 could be hidden within the decoy C2 domains and be used as a fallback communication channel within the occasion that the first C2 area is taken down.”
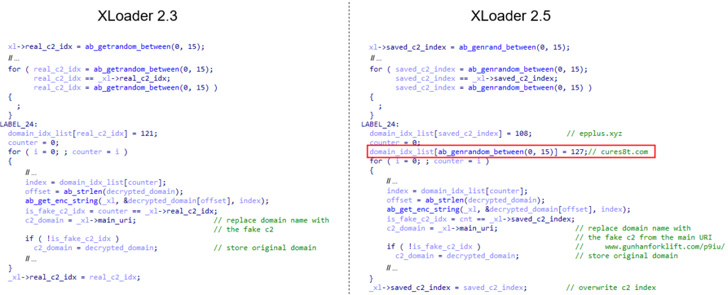
The stealthiness comes from the actual fact the area identify for the true C&C server is hidden alongside a configuration containing 64 decoy domains, from which 16 domains are randomly picked, adopted by changing two of these 16 with the pretend C&C handle and the genuine handle.
What’s modified within the newer variations of XLoader is that after the collection of 16 decoy domains from the configuration, the primary eight domains are overwritten with new random values earlier than every communication cycle whereas taking steps to skip the true area.
Moreover, XLoader 2.5 replaces three of the domains within the created checklist with two decoy server addresses and the true C&C server area. The final word aim is to stop the detection of the true C&C server, based mostly on the delays between accesses to the domains.
The truth that the malware authors have resorted to rules of likelihood principle to entry the official server as soon as once more demonstrates how risk actors continuously fine-tune their techniques to additional their nefarious targets.
“These modifications obtain two targets without delay: every node within the botnet maintains a gradual knockback charge whereas fooling automated scripts and stopping the invention of the true C&C servers,” Verify Level researchers mentioned.