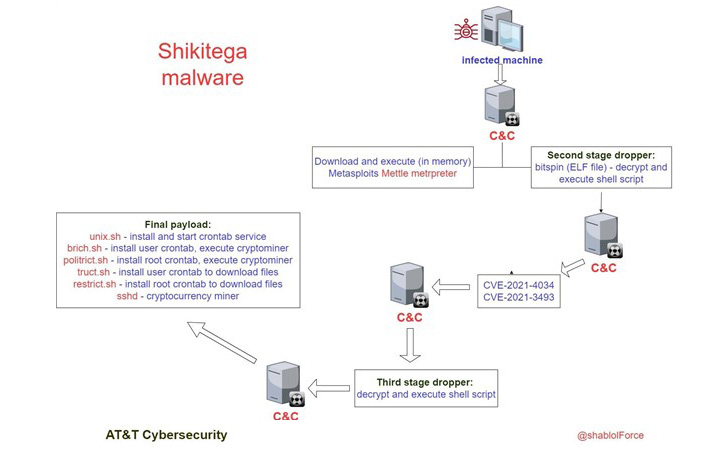
A brand new piece of stealthy Linux malware referred to as Shikitega has been uncovered adopting a multi-stage an infection chain to compromise endpoints and IoT gadgets and deposit extra payloads.
“An attacker can achieve full management of the system, along with the cryptocurrency miner that can be executed and set to persist,” AT&T Alien Labs stated in a brand new report printed Tuesday.
The findings add to a rising checklist of Linux malware that has been discovered within the wild in latest months, together with BPFDoor, Symbiote, Syslogk, OrBit, and Lightning Framework.
As soon as deployed on a focused host, the assault chain downloads and executes the Metasploit’s “Mettle” meterpreter to maximise management, exploits vulnerabilities to raise its privileges, provides persistence on the host through crontab, and finally launches a cryptocurrency miner on contaminated gadgets.
The precise methodology by which the preliminary compromise is achieved stays unknown as but, however what makes Shikitega evasive is its skill to obtain next-stage payloads from a command-and-control (C2) server and execute them immediately in reminiscence.
Privilege escalation is achieved by the use of exploiting CVE-2021-4034 (aka PwnKit) and CVE-2021-3493, enabling the adversary to abuse the elevated permissions to fetch and execute the ultimate stage shell scripts with root privileges to ascertain persistence and deploy the Monero crypto miner.
In an additional try and fly beneath the radar, the malware operators make use of a “Shikata ga nai” polymorphic encoder to make it tougher to detect by antivirus engines and abuse legit cloud companies for C2 capabilities.
“Risk actors proceed to seek for methods to ship malware in new methods to remain beneath the radar and keep away from detection,” AT&T Alien Labs researcher Ofer Caspi stated.
“Shiketega malware is delivered in a complicated manner, it makes use of a polymorphic encoder, and it step by step delivers its payload the place every step reveals solely a part of the full payload.”