Cybersecurity researchers have unearthed a brand new Python-based assault marketing campaign that leverages a Python-based distant entry trojan (RAT) to achieve management over compromised methods since at the very least August 2022.
“This malware is exclusive in its utilization of WebSockets to keep away from detection and for each command-and-control (C2) communication and exfiltration,” Securonix stated in a report shared with The Hacker Information.
The malware, dubbed PY#RATION by the cybersecurity agency, comes with a number of capabilities that enables the menace actor to reap delicate data. Later variations of the backdoor additionally sport anti-evasion strategies, suggesting that it is being actively developed and maintained.
The assault commences with a phishing e-mail containing a ZIP archive, which, in flip, harbors two shortcut (.LNK) recordsdata that masquerade as back and front facet photographs of a seemingly respectable U.Okay. driver’s license.
Opening every of the .LNK recordsdata retrieves two textual content recordsdata from a distant server which can be subsequently renamed to .BAT recordsdata and executed stealthily in background, whereas the decoy picture is exhibited to the sufferer.
Additionally downloaded from a C2 server is one other batch script that is engineered to retrieve extra payloads from the server, together with the Python binary (“CortanaAssistance.exe”). The selection of utilizing Cortana, Microsoft’s digital assistant, signifies an try and go off the malware as a system file.
Two variations of the trojan have been detected (model 1.0 and 1.6), with practically 1,000 traces of code added to the newer variant to assist community scanning options to conduct a reconnaissance of the compromised community and concealing the Python code behind an encryption layer utilizing the fernet module.
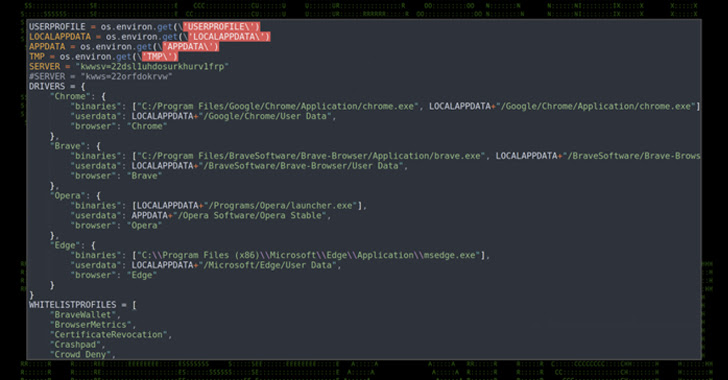
Different noteworthy functionalities comprise the power to switch recordsdata from host to C2 or vice versa, document keystrokes, execute system instructions, extract passwords and cookies from net browsers, seize clipboard information, and verify for the presence of antivirus software program.
What’s extra, PY#RATION capabilities as a pathway for deploying extra malware, which consists of one other Python-based info-stealer designed to siphon information from net browsers and cryptocurrency wallets.
The origins of the menace actor stay unknown, however the nature of the phishing lures posits that the supposed targets might doubtless be the U.Okay. or North America.
“The PY#RATION malware is just not solely comparatively tough to detect, the truth that it’s a Python compiled binary makes this extraordinarily versatile as it’ll run on virtually any goal together with Home windows, OSX, and Linux variants,” researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov stated.
“The truth that the menace actors leveraged a layer of fernet encryption to cover the unique supply compounds the issue of detecting recognized malicious strings.”