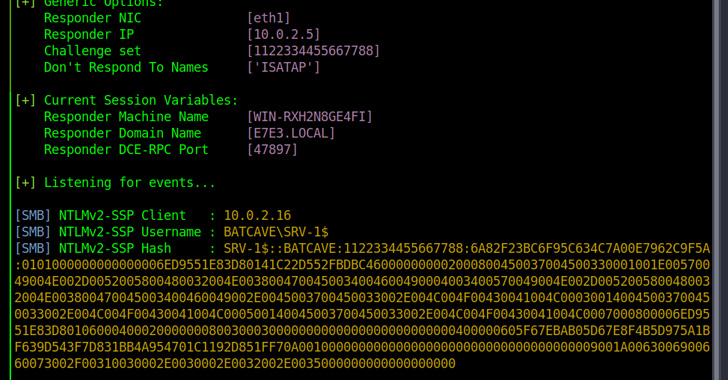
A brand new sort of Home windows NTLM relay assault dubbed DFSCoerce has been uncovered that leverages the Distributed File System (DFS): Namespace Administration Protocol (MS-DFSNM) to grab management of a website.
“Spooler service disabled, RPC filters put in to forestall PetitPotam and File Server VSS Agent Service not put in however you continue to need to relay [Domain Controller authentication to [Active Directory Certificate Services]? Don’t fret MS-DFSNM have (sic) your again,” safety researcher Filip Dragovic stated in a tweet.
MS-DFSNM offers a distant process name (RPC) interface for administering distributed file system configurations.
The NTLM (NT Lan Supervisor) relay assault is a widely known technique that exploits the challenge-response mechanism. It permits malicious events to take a seat between shoppers and servers and intercept and relay validated authentication requests with a purpose to achieve unauthorized entry to community assets, successfully gaining an preliminary foothold in Lively Listing environments.
The invention of DFSCoerce follows an identical technique referred to as PetitPotam that abuses Microsoft’s Encrypting File System Distant Protocol (MS-EFSRPC) to coerce Home windows servers, together with area controllers, into authenticating with a relay beneath an attacker’s management, letting menace actors probably take over a complete area.
“By relaying an NTLM authentication request from a website controller to the Certificates Authority Internet Enrollment or the Certificates Enrollment Internet Service on an AD CS system, an attacker can receive a certificates that can be utilized to acquire a Ticket Granting Ticket (TGT) from the area controller,” the CERT Coordination Heart (CERT/CC) famous, detailing the assault chain.
To mitigate NTLM relay assaults, Microsoft recommends enabling protections like Prolonged Safety for Authentication (EPA), SMB signing, and turning off HTTP on AD CS servers.