|
| Picture Supply: Toptal |
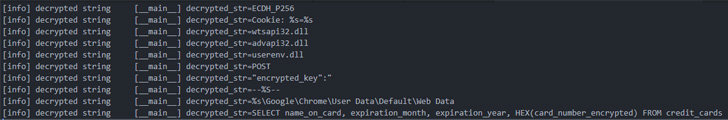
The infamous Emotet malware has turned to deploy a brand new module designed to siphon bank card info saved within the Chrome internet browser.
The bank card stealer, which solely singles out Chrome, has the flexibility to exfiltrate the collected info to completely different distant command-and-control (C2) servers, in keeping with enterprise safety firm Proofpoint, which noticed the part on June 6.
The event comes amid a spike in Emotet exercise because it was resurrected late final 12 months following a 10-month-long hiatus within the wake of a regulation enforcement operation that took down its assault infrastructure in January 2021.
Emotet, attributed to a menace actor often known as TA542 (aka Mummy Spider or Gold Crestwood), is a complicated, self-propagating and modular trojan that is delivered through e-mail campaigns and is used as a distributor for different payloads similar to ransomware.
As of April 2022, Emotet remains to be the preferred malware with a worldwide affect of 6% of organizations worldwide, adopted by Formbook and Agent Tesla, per Test Level, with the malware testing out new supply strategies utilizing OneDrive URLs and PowerShell in .LNK attachments to get round Microsoft’s macro restrictions.
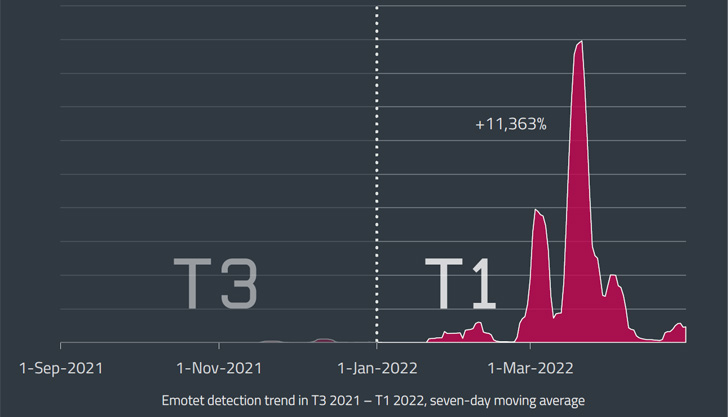
The regular development in Emotet-related threats is substantiated additional by the truth that the variety of phishing emails, usually hijacking already current correspondence, grew from 3,000 in February 2022 to roughly 30,000 in March concentrating on organizations in varied international locations as a part of a mass-scale spam marketing campaign.
Stating that Emotet exercise have “shifted to the next gear” in March and April 2022, ESET mentioned that detections jumped a 100-fold, registering a development of over 11,000% throughout the first 4 months of the 12 months when in comparison with the previous three-month interval from September to December 2021.
A few of the frequent targets for the reason that botnet’s resurrection have been Japan, Italy, and Mexico, the Slovak cybersecurity firm famous, including the most important wave was recorded on March 16, 2022.
“The scale of Emotet’s newest LNK and XLL campaigns was considerably smaller than these distributed through compromised DOC recordsdata seen in March,” Dušan Lacika, senior detection engineer at Dušan Lacika, mentioned.
“This means that the operators are solely utilizing a fraction of the botnet’s potential whereas testing new distribution vectors that might substitute the now disabled-by-default VBA macros.”
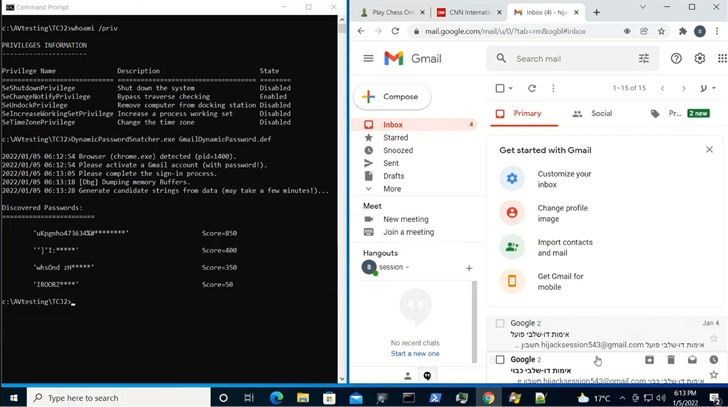
The findings additionally come as researchers from CyberArk demonstrated a brand new approach to extract plaintext credentials immediately from reminiscence in Chromium-based internet browsers.
“Credential information is saved in Chrome’s reminiscence in cleartext format,” CyberArk’s Zeev Ben Porat mentioned. “Along with information that’s dynamically entered when signing into particular internet functions, an attacker could cause the browser to load into reminiscence all of the passwords which can be saved within the password supervisor.”
This additionally consists of cookie-related info similar to session cookies, doubtlessly permitting an attacker to extract the knowledge and use it to hijack customers’ accounts even when they’re protected by multi-factor authentication.